**Project Fail: Cracking a Laptop BIOS Password Using AI**
The world of used computers can be a minefield, filled with unpleasant surprises that have nothing to do with insects. When buying second-hand laptops, there's always a risk of encountering issues like Apple hardware being iCloud-locked with the original owner MIA or PCs having BIOS passwords in place. While clearing CMOS memory often resolves these issues, Casey Bralla found that this wasn't always the case when he purchased a former student-issued HP ProBook laptop from Facebook Marketplace.
The HP ProBook laptop in question had a BIOS password set, which was likely implemented to prevent enterprising students from accessing and potentially misusing the system. However, HP's policy of locking down access to the BIOS is more than just a precautionary measure - it's designed to be virtually unbreakable. The encrypted password and associated settings are written to a separate Flash memory, making it difficult for users to recover without the master key.
Unfortunately, even the master key may not guarantee access, as HP's policy dictates that replacing the system board is often the only solution when attempting to bypass the BIOS password. This leaves users like Casey with limited options for recovery, which can be frustrating and time-consuming.
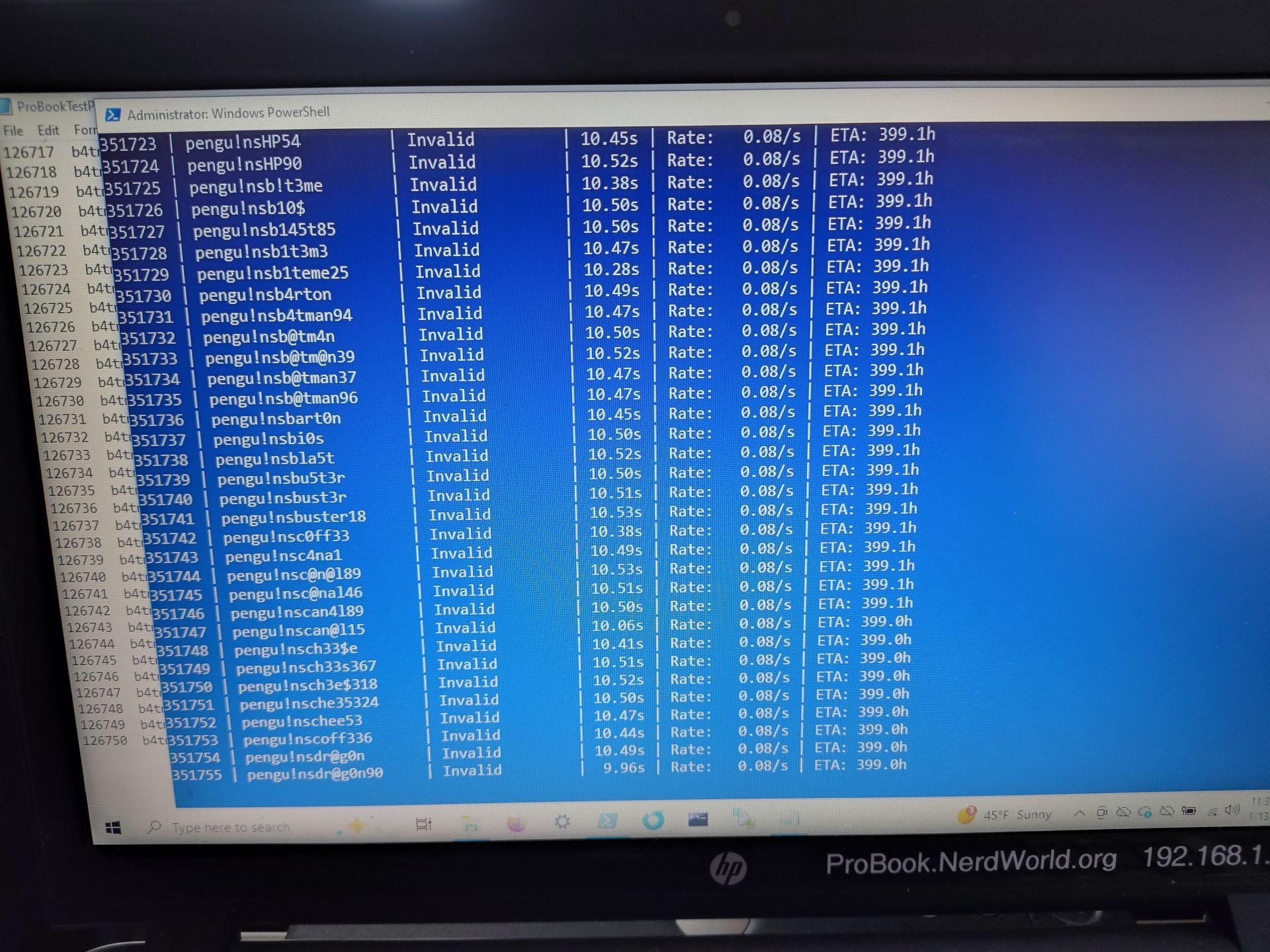
Faced with this challenge, Casey decided to take a more unconventional approach - using AI to brute-force crack the BIOS password. He began by utilizing a Rust-based project on GitHub that promised to simplify the process, but unfortunately, it failed to build.
Undeterred, Casey turned to the Claude AI chatbot to assist him in writing a Python script to perform brute-force cracking using the Windows-based HP BIOS utility. The chatbot was also tasked with generating multiple lists of unique passwords that might be potential candidates based on human guesses.
Over the course of six months, Casey ran near-continuous attempts at cracking the BIOS password, with each try taking approximately nine seconds. Unfortunately, despite the best efforts of the AI and his own human input, they were unable to crack the code.
While Casey's attempts may have been unsuccessful, they did provide valuable insights into the strength of HP's BIOS security. It appears that the company has taken measures to ensure that its systems are protected from unauthorized access, even if it means sacrificing user convenience.
For Casey, this failure may have been a setback, but it also provided an opportunity to explore alternative solutions. In the end, he was able to continue using his laptop, albeit without BIOS access - a small price to pay for the valuable lesson learned about the importance of robust security measures in modern computing.