**CERT-UA Reports PLUGGYAPE Cyberattacks on Defense Forces**
A recent report by CERT-UA has shed light on a series of cyberattacks targeting Ukraine's defense forces using the PLUGGYAPE malware. The attacks have been linked to the Russian-linked group Void Blizzard, active since 2024.
**The Attack Chain**
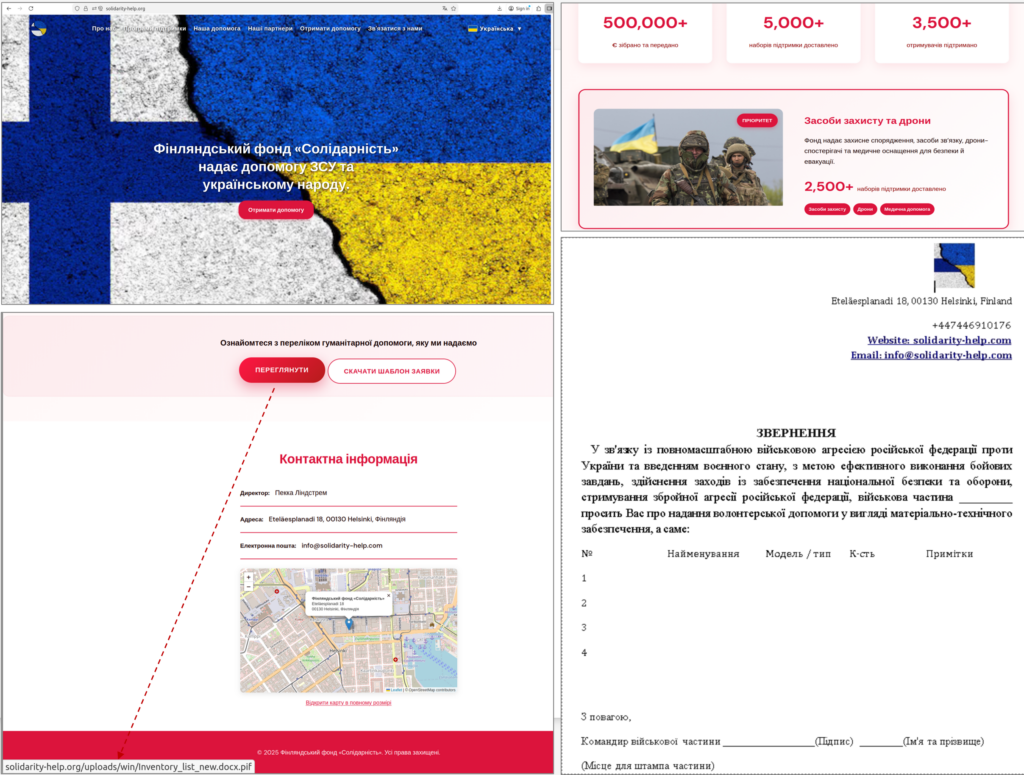
The attack chain begins with social engineering tactics, where attackers contact targets through instant messaging apps and convince them to visit a fake website posing as a charitable foundation. The site encourages victims to download supposed "documents," which are actually malicious executable files. These files often arrive inside password-protected archives or are sent directly via chat, using misleading extensions such as ".docx.pif" to appear harmless.
**PLUGGYAPE Malware**
When opened, the file runs a Python-based program packaged with PyInstaller, which installs the PLUGGYAPE backdoor on the infected system. This gives attackers remote access to the infected system and allows them to execute malicious code.
**Evolution of PLUGGYAPE**
The report highlights the evolution of the PLUGGYAPE malware over time. In October 2025, attackers used a file with the extension ".pdf.exe," which launched a loader that downloaded a Python interpreter and a PLUGGYAPE file from Pastebin. Later versions became more advanced, using the MQTT protocol for communication and including anti-analysis checks.
**PLUGGYAPE.V2 Variant**
From December 2025, attackers deployed an obfuscated PLUGGYAPE.V2 variant using MQTT for communication and anti-analysis checks. This variant hides C2 server details on public sites in encoded form.
**Command-and-Control (C2) Server**
The report notes that the C2 server details are often hidden and retrieved from public sites like Pastebin or rentry.co, often encoded to evade detection.
**Impact of PLUGGYAPE**
PLUGGYAPE is a Python-based tool that connects to a command server via WebSockets or MQTT and exchanges data in JSON format. It collects system identifiers to generate a unique device ID using SHA-256, executes code received from the server, and maintains persistence by adding itself to the system's Run registry key.
**Conclusion**
The report concludes by emphasizing the constantly evolving nature of the cyberthreat landscape. The initial interaction with the object of a cyberattack is increasingly carried out using legitimate accounts, phone numbers of Ukrainian mobile operators, and the Ukrainian language, audio, and video communication are used. The attacker can demonstrate detailed and relevant knowledge about the person, organization, and features of its functioning.
**The Rise of Instant Messaging Apps**
The report also notes that widely used instant messengers available on mobile devices and personal computers are becoming the most common delivery channel for software tools implementing cyberthreats.
**Link to Void Blizzard Group**
The PLUGGYAPE attacks have been linked to the Russian-linked group Void Blizzard, which was previously undetected until a 2024 police breach in the Netherlands. The Dutch authorities blamed a state actor for the breach, and the police reported the security breach to the Data Protection Authority.
**Stay Informed**
Follow me on Twitter: @securityaffairs and Facebook and Mastodon for the latest updates on cybersecurity threats and news.