**Windows 2000 Rots in Peace by the Sea**
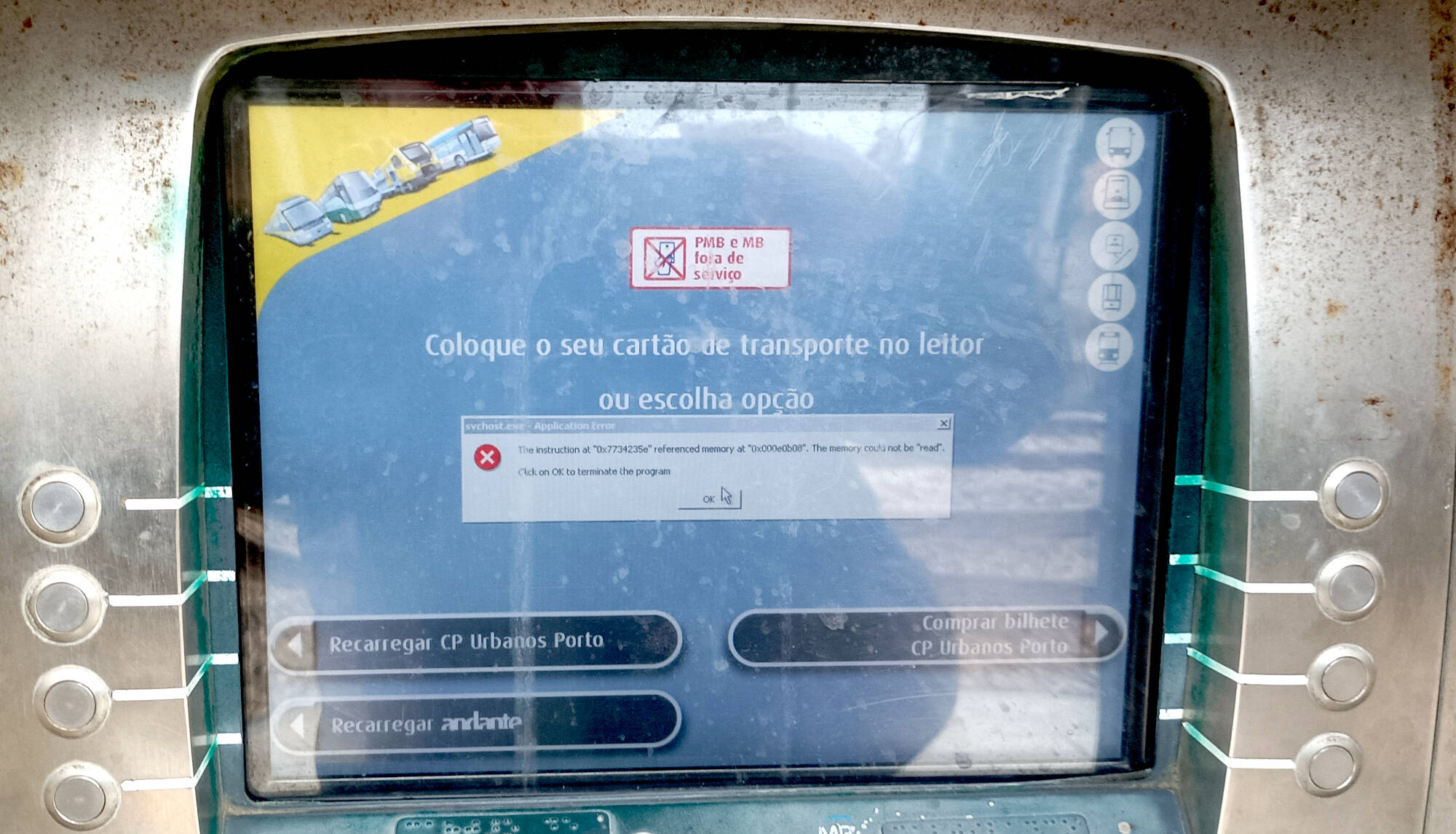
As we reported earlier, Windows 2000 has been making headlines lately for its continued presence in outdated technology. The latest sighting is a rail ticket machine at Granja station in Portugal, where the salty coastal air seems to be taking its toll on the aged operating system.
The machine's rusty surroundings are a testament to its seaside location, but it's clear that Windows 2000 is not happy about being here. A Register reader, who must have a penchant for punishment, spotted the issue and shared it with us. The machine's touchscreen interface appears to be frozen, with error messages indicating memory-related problems.
For those familiar with our earlier articles on this topic, you'll recall that Windows 2000 is still lurking behind the scenes of these automated ticket retail systems. And it seems like a rogue software process has strayed into the machine's memory, causing a conflict and resulting in an error. Our reader speculated that this might be why card payments are being flagged as out of service.
While we're not brave enough to test our hypothesis by pressing the OK button, we can report that there is no Blue Screen of Death – yet. It's likely that the issue lies with a software problem rather than any hardware issues, despite this terminal having lived a hard life.
The history of Portugal's railways is a story of expansion and contraction, as passengers and bean counters discovered the joys of travel by road. A recent analysis suggested that express bus services are often a better bet than taking the train. Perhaps the same is true for Microsoft's operating system – Windows 2000 may be best left in its glory days, while Windows 11 struggles to gain traction.
As we bid farewell to this rusting relic of the past, it's clear that Windows 2000 has seen better days. With only a few scattered remnants like this ticket machine remaining, we're reminded that even the most stalwart operating system eventually succumbs to the passage of time. But who knows? Perhaps one day, someone will come along and breathe new life into this old technology.