**The Striking-Looking Number Puzzle Game Stip is More Than Meets the Eye**
As I delved into the world of Stip, a number puzzle game that has been generating quite the buzz, I couldn't help but feel drawn in by its striking visuals. The clean design and intriguing aesthetic had me hooked from the very start, but it was only when I began to scratch beneath the surface that I truly understood what made this game so unique.
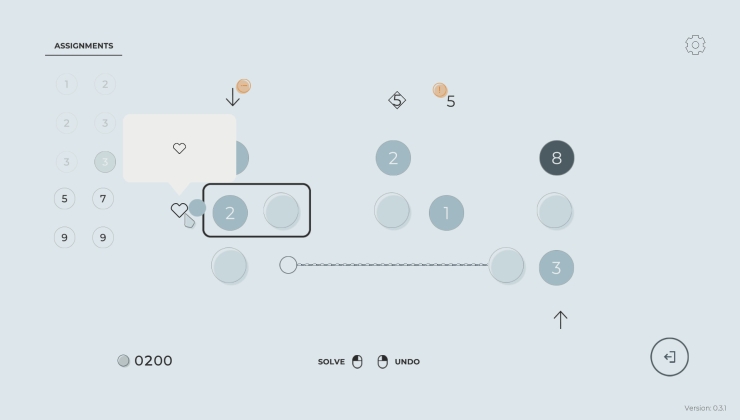
Developed by the creator of Midnight Protocol, a tactical hacking narrative-driven RPG, Stip is no ordinary puzzle game. On the surface, it appears to be a simple yet engaging challenge where players are required to place numbers in a series of dots with specific constraints. However, as I soon discovered, things aren't always as straightforward as they seem.
The rules and constraints are not explicitly clear, leaving the player to experiment and figure out the underlying logic behind each puzzle. And it's precisely this uncertainty that adds an extra layer of depth to the game. The press release hinted at a narrative layer of secrets throughout, where puzzles will "start to misbehave" and require players to peel back the layers to uncover more hidden treasures.
The trailer for Stip has been doing the rounds, and it's no wonder why – it's an absolute attention-grabber. The game's promise of a Metroidvania-style narrative, where exploration and discovery are key, is incredibly enticing. And with its unique blend of puzzle-solving and mystery-unraveling, Stip has all the makings of a true gaming experience.
So when can we expect to get our hands on this enigmatic number puzzle game? The answer is sometime later in 2026. Rest assured that I – and many other gamers out there – will be eagerly anticipating its release, ready to dive headfirst into the world of Stip and uncover all its secrets.
**About Stip**
* Developer: [Developer Name] * Release Date: TBA (2026) * Genre: Number Puzzle Game * Platforms: [Platforms]
Stay tuned for more updates on this exciting new game, and get ready to embark on a thrilling journey of discovery and puzzle-solving with Stip.