**Critical n8n Flaw Could Enable Arbitrary Code Execution**
A critical flaw in the popular n8n automation platform has been discovered, allowing attackers to execute arbitrary code if exploited under specific conditions.
Researchers have identified a critical vulnerability, tracked as CVE-2025-68613 (CVSS score of 9.9), in the n8n workflow automation platform that could enable attackers to achieve arbitrary code execution under certain circumstances.
n8n is a widely-used workflow automation platform designed for technical teams, combining the flexibility of custom code with the speed and simplicity of no-code tools. It supports over 400 integrations, includes native AI features, and uses a fair-code license, allowing organizations to build powerful automations while retaining full control over their data and deployment environments.
The vulnerability, which affects specific versions of n8n (1.120.4, 1.121.1, and 1.122.0), lies in the platform's workflow expression evaluation system. According to an advisory from n8n's developers, "expressions supplied by authenticated users during workflow configuration may be evaluated in an execution context that is not sufficiently isolated from the underlying runtime."
An attacker could exploit this weakness during workflow configuration to run arbitrary code with the same privileges as the n8n process. This could potentially lead to full system compromise, data exposure, workflow tampering, and execution of system-level commands.
The vulnerability has been fixed in the latest versions of n8n (1.120.4, 1.121.1, and 1.122.0), and users are strongly urged to upgrade as soon as possible. If upgrading is not immediately possible, administrators should restrict workflow creation and editing to fully trusted users and run n8n in a hardened environment, keeping in mind that these measures only reduce risk temporarily and do not fully resolve the issue.
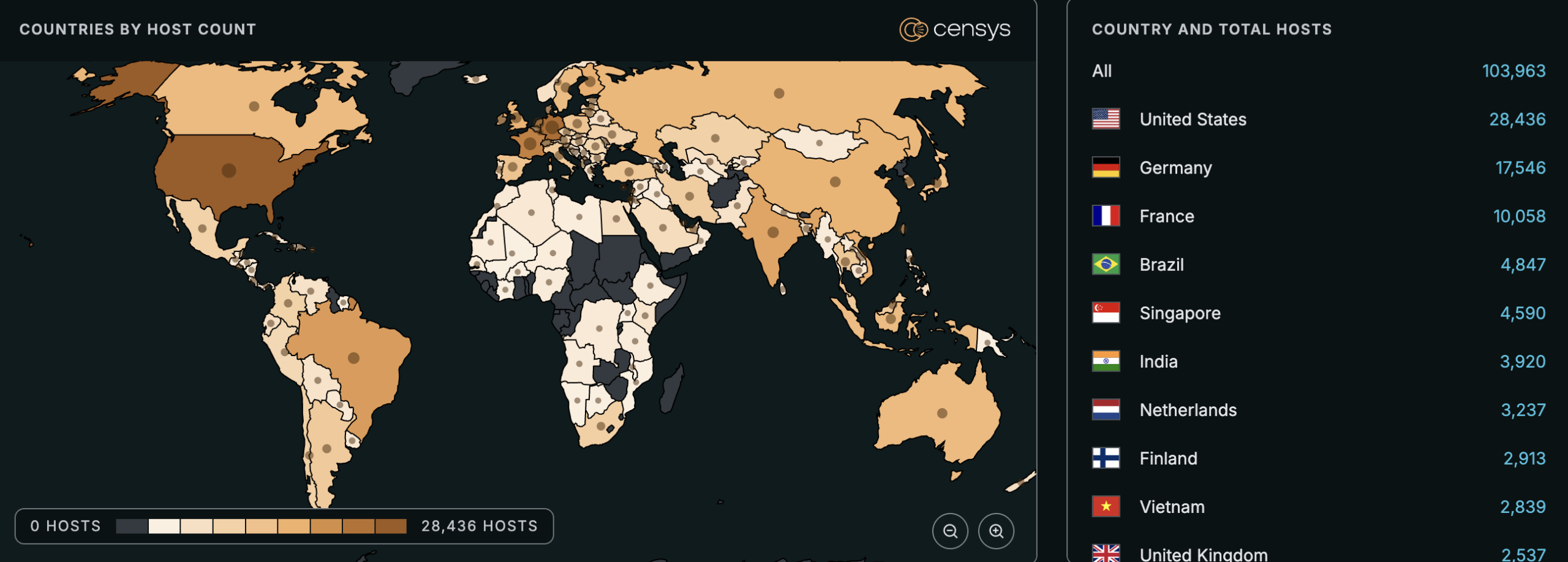
Cybersecurity firm Censys has observed 103,476 potentially vulnerable instances as of December 22, 2025. Most of these instances are located in the U.S., Germany, and France.
**What You Need to Do**
- Install the latest versions of n8n (1.120.4, 1.121.1, and 1.122.0) immediately.
- If patching isn’t possible, restrict workflow editing to trusted users.
- Run n8n in a hardened environment with restricted operating system privileges and network access.
We urge all n8n users to take immediate action to protect their instances from potential exploitation of this critical vulnerability. Stay informed about the latest cybersecurity threats by following us on Twitter (@securityaffairs) and Facebook, or connecting with us on Mastodon.