Russia-Linked COLDRIVER Speeds Up Malware Evolution After LOSTKEYS Exposure
Since May 2025, the Russia-linked hacking group COLDRIVER has been rapidly evolving its malware in response to the exposure of its LOSTKEYS variant. According to Google's Threat Intelligence Group (GTIG), the hackers have been rolling out frequent updates and improvements to their malicious tools, showcasing an accelerated pace of development and aggressive operations.
The ColdRiver APT: A Russian Cyberespionage Group
COLD RIVER APT, also known as "Seaborgium," "UNC4057," "Callisto," "Star Blizzard," and "TA446," is a Russian cyberespionage group that has been targeting government officials, military personnel, journalists, and think tanks since at least 2015. GTIG has been monitoring the group's activities for years and has observed their tactics, techniques, and procedures (TTPs).
The LOSTKEYS Variant Exposure
The exposure of LOSTKEYS, a malware variant attributed to COLDRIVER, marked a turning point in the group's evolution. In response to this development, the hackers quickly refined their tools, demonstrating an accelerated pace of development and aggressive operations.
The NOROBOT Malware
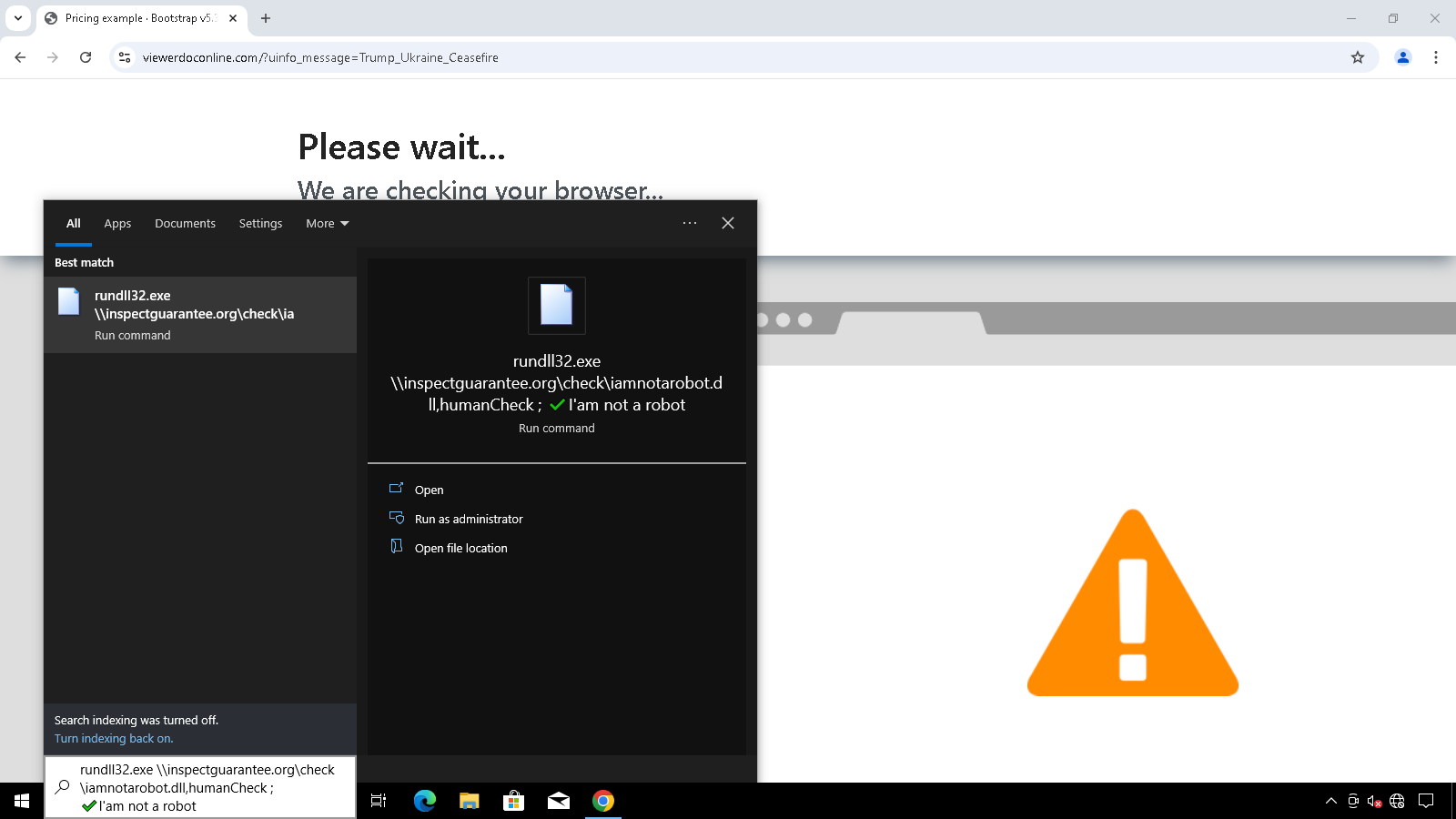
COLDRIVER shifted its focus to a new malicious DLL named NOROBOT, delivered through an updated COLDCOPY "ClickFix" lure disguised as a CAPTCHA. Unlike older PowerShell-based infections, this version tricks users into launching the malware via rundll32.
The initial NOROBOT version dropped a Python backdoor called YESROBOT, but the group soon replaced it with a more flexible PowerShell variant named MAYBEROBOT. Since then, COLDRIVER has constantly refined NOROBOT, simplifying the chain to improve success and reintroducing complexity with split encryption keys to make detection harder.
The Evolution of NOROBOT
COLDRIVER's NOROBOT malware has undergone significant changes since its introduction. Initially, it dropped a Python backdoor called YESROBOT, but the group soon replaced it with MAYBEROBOT, a more flexible PowerShell variant. The NOROBOT infection chain evolved rapidly, with COLDRIVER simplifying the malware delivery and evading detection.
Since June 2025, GTIG observed COLDRIVER intensifying the development of its NOROBOT malware. Simplified versions made tracking easier, while later variants reintroduced cryptographic keys and multi-stage download steps to hinder analysis. The group phased out the Python-based YESROBOT backdoor, which was prone to detection and limited in functionality, replacing it with the leaner, more flexible MAYBEROBOT.
The Focus on Concealing Delivery Mechanisms
COLDRIVER's focus on concealing delivery mechanisms is reflected in the group's use of rotated infrastructure, changed file names, DLL names, and export names. This approach demonstrates the group's determination to stay hidden and maintain access to high-value intelligence targets.
Conclusion
COLDRIVER's rapid evolution of its malware since May 2025 is a clear indication of the group's commitment to staying ahead of security measures. The exposure of LOSTKEYS marked a turning point in this process, as the hackers quickly refined their tools and focused on concealing delivery mechanisms.
"It is currently not known why COLDRIVER chooses to deploy malware over more traditional phishing methods," states GTIG's report. "However, it is clear that they have spent significant development effort to re-tool and deploy their malware to specific targets."
The group's strategy of continuously refining malware delivery, evading detection, and ensuring persistent intelligence collection against high-value targets demonstrates its dedication to achieving its goals.