**Decapsulating a PIC12F683: Unveiling its CMOS Implementation**
In a fascinating five-part series, [Andrew Zonenberg](https://www.youtube.com/channel/UCz9ZvK4hO5k2Vp8f3yGgDlw) takes us on a journey of discovery as he decapsulates a PIC12F683 to reveal its intricate CMOS implementation. This 8-pin, flash-based, 8-bit microcontroller from Microchip has been the subject of [Andrew's] fascination since 2011, when he first managed to break read-protection on it.
**The Why Behind the Chip**
[Andrew] chose to revisit the PIC12F683 for decapsulation due to his own personal connection with the chip. Having successfully broken its read-protection in 2011, he wanted to delve deeper into its inner workings using the advanced resources and skills he had acquired over the intervening period.
**The Decapsulation Process**
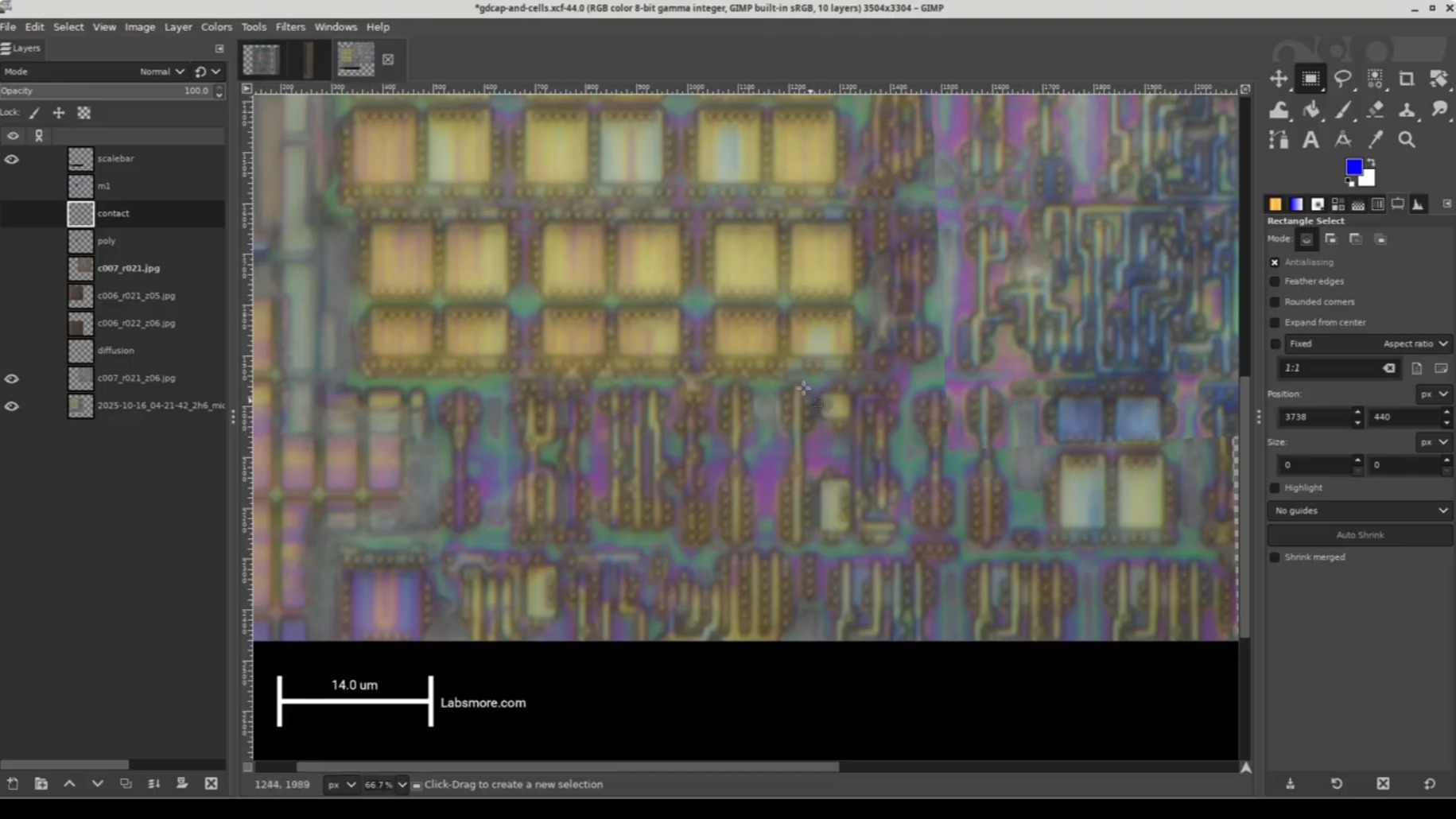
In this engaging series, [Andrew] guides us through each stage of the decapsulation process with meticulous detail. The first step involves taking a package cross-section, which provides an initial glimpse into the chip's internal structure. He then proceeds to decapsulate and delayer the chip, capturing high-resolution photos as he goes along.
**Safety Precautions**
As [Andrew] carefully navigates the decapsulation process, he takes time to emphasize the dangers of working with acid and the risks associated with it. He also shares his risk mitigations strategies, providing valuable insights for anyone attempting to replicate this process.
**Floorplan Analysis and SRAM Implementation**
The next stage involves a floorplan analysis, where [Andrew] takes stock of the entire chip before zooming in on its SRAM implementation. This is where things get really interesting, as he delves into the intricate details of the chip's design.
**Resources for Aspiring Decapsulators**
For those interested in decapsulating integrated circuits, [Andrew]'s videos offer a wealth of information and inspiration. Additionally, you may want to explore:
* **Laser Fault Injection: Now With Optional Decapping**: A fascinating video that explores the use of laser fault injection to compromise IC security * **A Particularly Festive Chip Decapping**: A lighthearted take on chip decapsulation, highlighting the art and science behind it * **Decapping Components Hack Chat with John McMaster**: A transcript from a live hack chat where experts share their experiences and insights on decapping integrated circuits
Thanks to [Peter Monta](https://twitter.com/monta) for bringing this fascinating series to our attention.