# $150K Awarded for L1TF Reloaded Exploit That Bypasses Cloud Mitigations
In a significant breakthrough, researchers from Vrije Universiteit Amsterdam have earned a whopping $150,000 for discovering an exploit dubbed "L1TF Reloaded." This innovative attack combines the L1TF (Foreshadow) vulnerability with half-Spectre to leak memory from virtual machines (VMs) on public cloud services, despite existing mitigations. The research highlights the persistent threat of transient CPU vulnerabilities and their ability to bypass security measures.
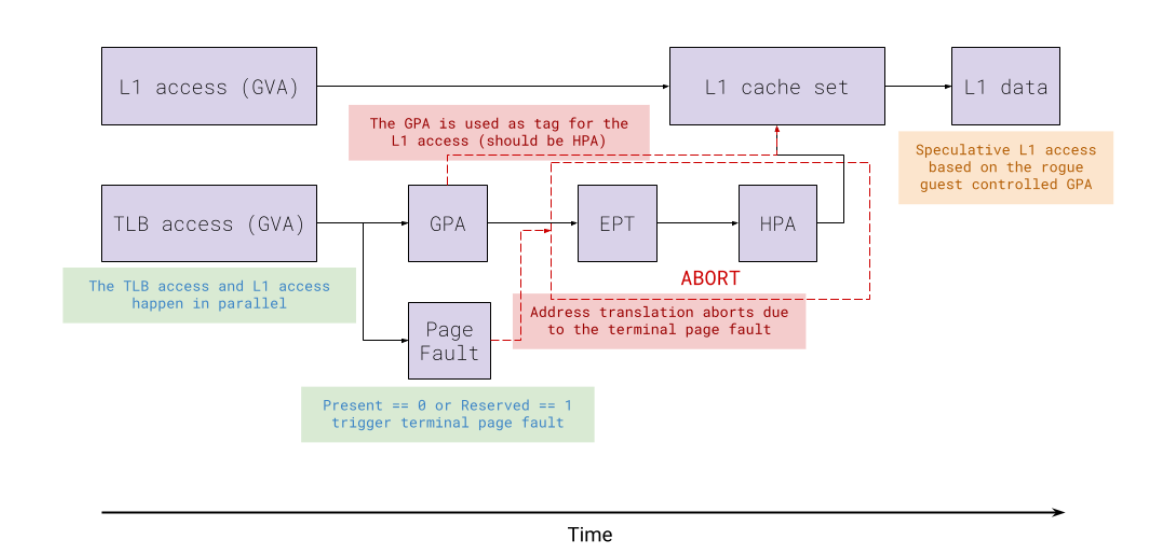
The L1TF Reloaded flaw allows attackers to bypass prior mitigations and access sensitive data from Google Cloud hypervisors and co-tenants. By utilizing a technique called pointer-chasing, researchers translated guest virtual addresses to host physical ones, enabling the leakage of any victim memory byte through L1TF.
In their research paper, published by the VUSec group, the researchers explained that they used a novel approach based on pointer chasing through the host and guest to leak all required information for manually performing two-dimensional page table walks. This allowed them to translate arbitrary virtual guest addresses to host physical addresses, thereby enabling the leakage of any byte in the memory of the victim via L1TF.
The researchers tested their exploit on Google Cloud, successfully leaking an Nginx TLS key from a victim VM within approximately 14 hours, even under noisy conditions. They also demonstrated that the attack could access host OS data, identify co-tenant VMs, and steal sensitive keys.
Their research was conducted over six different physical hosts, with 25 out of 28 successful exploit runs completing successfully. Each successful run leaked the entire private key correctly, with an average run time of 14.2 hours (standard deviation: 16.2 hours).
The researchers tested their L1TF exploit under extreme cloud noise conditions and found that it remained reliable every time. They filled a host with vCPUs running aggressive I/O and memory/cache thrashing while hitting a victim Nginx server at a rate of 100×/s.
Across 10 noisy runs on Google Cloud, the exploit succeeded every time, leaking the key in an average of 15.2 hours. The team concluded that the attack remains robust even under realistic, high-noise cloud conditions.
To mitigate L1TF attacks, researchers recommend disabling SMT or EPT plus L1D flushing. However, these measures can reduce performance and may be enabled by default in Linux.
In contrast, standard defenses like flushing and core scheduling did not block guest-to-host attacks if sensitive data was loaded via a half-Spectre gadget. On AWS, extra protections like XPFO and process-local memory blocked leaks of guest data, leaving only harmless host info exposed.
The researchers' discovery serves as a stark reminder that transient execution flaws are still a significant threat. As new exploit tricks emerge, cloud defenses may be vulnerable to being broken through.
In recognition of their groundbreaking research, Google awarded the VUSec group $151,515 – the top Google Cloud VRP payout. The award was made possible by Google's sponsorship of a sole-tenant node for the researchers' research project in Amsterdam.
The researchers demonstrated their work in person at Google's offices in Zurich and presented their findings to the company's representatives.
#Follow us on Twitter: @securityaffairs #Like us on Facebook and Mastodon