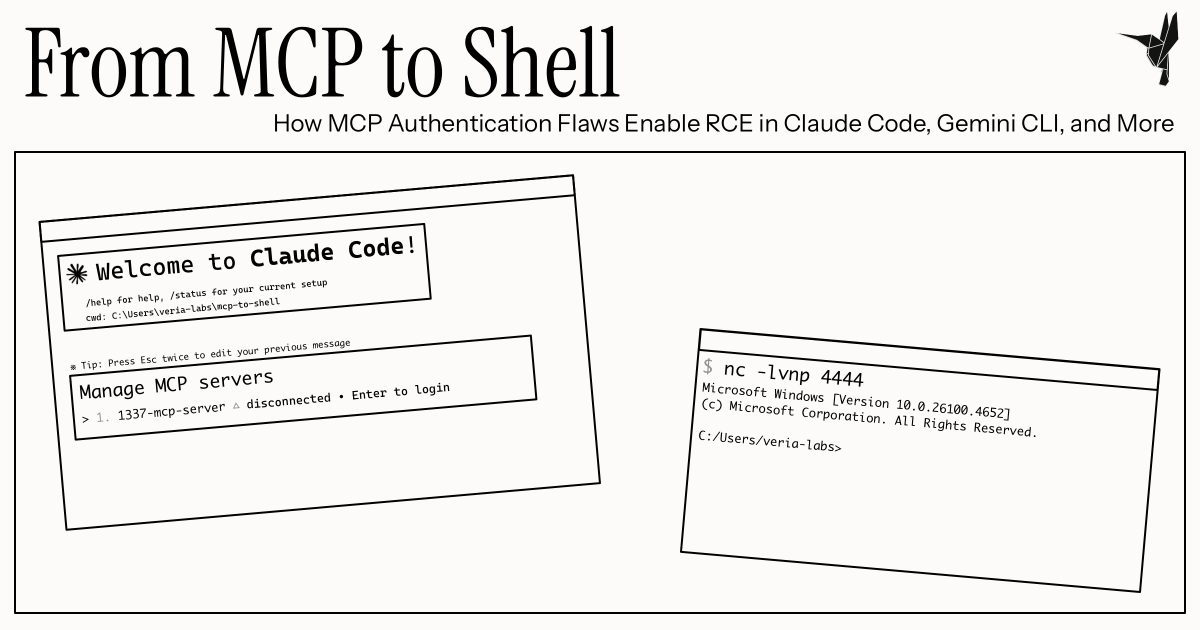
From MCP to Shell: MCP Auth Flaws Enable RCE in Claude Code, Gemini CLI and More
Security vulnerabilities are a constant threat to the digital world. In recent times, researchers have identified multiple critical flaws in various software applications that can compromise user data and grant unauthorized access to malicious actors. One such application is Claude Code, which has recently been found to be vulnerable to Remote Code Execution (RCE) due to an authentication flaw.
For those unfamiliar with MCP, it stands for Microsoft's Connected Platform, a set of tools designed to simplify the development process for developers building connected experiences. However, the recent discovery of security vulnerabilities in its authentication system has left many wondering if their applications are at risk.
Gemini CLI is another popular tool that has been affected by the same vulnerability. Gemini CLI is an open-source command-line interface that provides a simple and intuitive way to interact with Git repositories. Despite its ease of use, its security has recently come under scrutiny due to the widespread adoption of MCP in various development environments.
But what exactly does this mean for users? In short, if you're using applications built on top of MCP or Gemini CLI, you could be at risk of a security breach. RCE vulnerabilities can allow malicious actors to inject code into your system, potentially leading to data theft, system compromise, and even physical harm.
Fortunately, researchers have been working tirelessly to identify and address these vulnerabilities. By developing secure protocols and implementing robust authentication systems, developers can ensure that their applications remain protected from cyber threats.
A Message of Hope
No matter how daunting the task of securing your application may seem, there is hope. With the rapid pace of technological advancements comes a commitment to security that can provide real results in hours, not weeks.
At [Your Company], we understand the importance of timely and effective security measures. Our team of experts is dedicated to helping businesses protect their applications from cyber threats. We offer a range of solutions designed to address the latest security vulnerabilities and ensure your data remains safe.
Contact Us Today
If you're concerned about the security of your application or would like to learn more about our solutions, please don't hesitate to get in touch. Our team is here to help and can be reached at [Your Contact Information].