Beware: GitHub repos distributing Atomic Infostealer on macOS
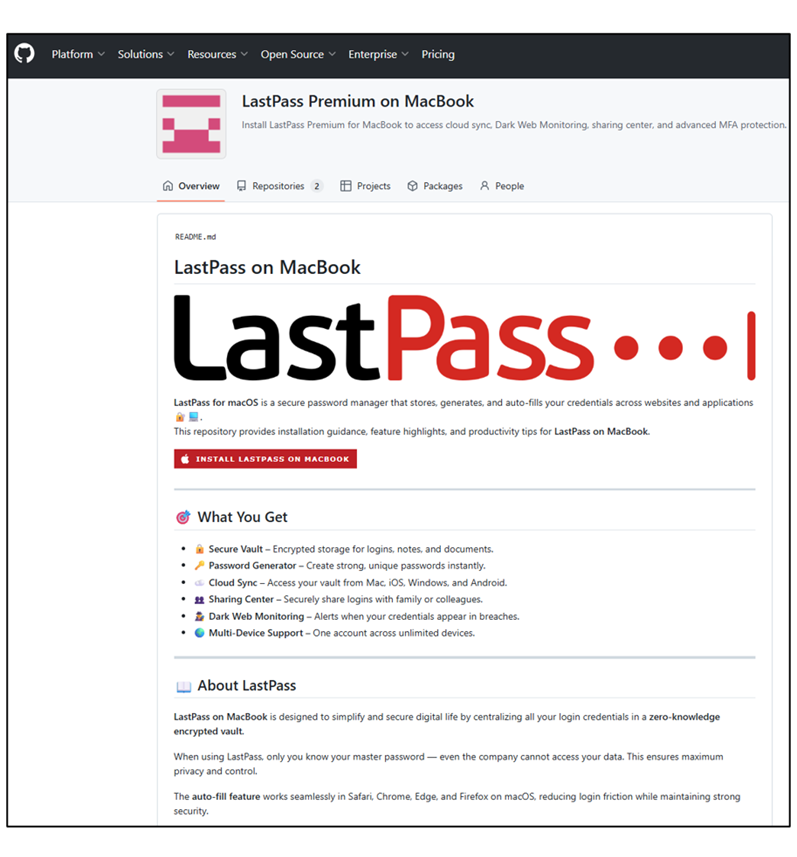
LastPass has issued a warning to macOS users about the distribution of malicious software through fake GitHub repositories, which are masquerading as legitimate tools. The cybersecurity company's Threat Intelligence, Mitigation, and Escalation (TIME) team has been tracking an ongoing campaign that aims to trick Mac users into installing the Atomic infostealer malware.
The LastPass report highlights how threat actors have created multiple GitHub repositories under different usernames in an attempt to evade takedowns. The fake pages are designed to appear as if they belong to real companies, using terminology such as "MacOS," "Mac," and "Premium on MacBook" to make them seem legitimate.
Once a victim clicks on one of these repositories, they are redirected to a page that instructs them to follow ClickFix-style instructions in the Terminal. This allows the malicious software to be installed on the user's device, compromising their personal data and passwords.
The Campaign: Impersonating Popular Tools
The Atomic infostealer malware campaign is targeting tech firms, banks, and password managers, including popular tools such as 1Password, Dropbox, Notion, Shopify, and others. The threat actors are using search engine optimization (SEO) techniques to push malicious sites to the top of search results on Google and Bing.
Security teams have been sharing Indicators of Compromise (IoCs) to help detect and mitigate this campaign. By being aware of these threats, users can take steps to protect themselves from falling victim to this malicious software.
Protecting Yourself
To avoid falling victim to this malware, users are advised to be cautious when clicking on links or downloading software from unknown sources. Here are some tips to help you stay safe:
- Only download software from reputable sources.
- Be wary of unfamiliar websites and links.
- Use strong, unique passwords for all accounts.
By staying informed and taking the necessary precautions, users can protect themselves against this malicious campaign. Stay safe online!
Follow me on Twitter: @securityaffairs and Facebook and Mastodon
Share your thoughts:
Do you have any experience with similar malware campaigns? Share your story in the comments below.