HybridPetya Ransomware Bypasses UEFI Secure Boot: A Growing Threat
Researchers at ESET have discovered a new ransomware malware called HybridPetya, which has been found to bypass the UEFI Secure Boot mechanism on outdated systems. This malicious software (malware) echoes the infamous Petya/NotPetya attacks of 2016-2017 and has several additional capabilities that make it noteworthy for threat monitoring.
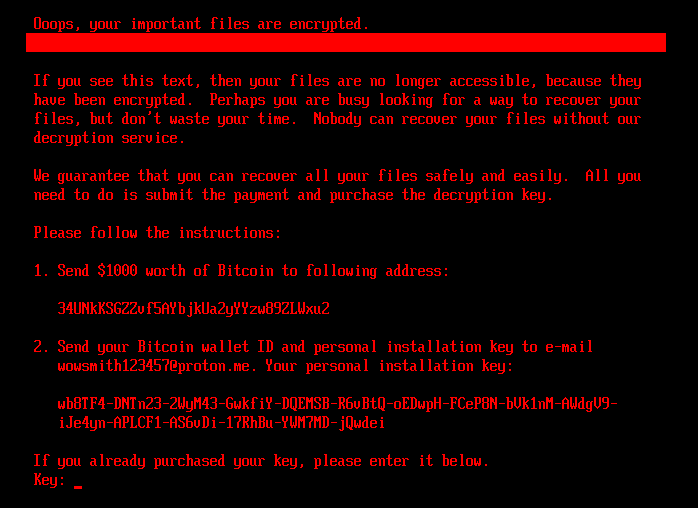
The discovery was made public after researchers analyzed HybridPetya's components, including its bootkit and installer. The UEFI bootkit has two similar versions, each with a unique set of functionalities. When executed, the bootkit checks the encryption flag in the config file: 0 (ready), 1 (encrypted), or 2 (decrypted). If set to 0, it extracts a Salsa20 key and nonce, zeros the config file key, sets the flag to 1, encrypts the 'verify' file, and creates a counter file.
The bootkit searches for NTFS partitions and encrypts the Master File Table. It then updates the counter file with the number of encrypted clusters and displays a fake CHKDSK status. After encryption, the malware reboots. If the disk is already encrypted (flag 1), it shows a ransom note and accepts a 32-character key.
The HybridPetya installer locates the EFI System Partition on GPT disks, removes the fallback loader (\EFI\Boot\Bootx64.efi), and drops an encryption config (\EFI\Microsoft\Boot\config) containing the Salsa20 key, nonce, and victim key. It also includes a 0x200-byte verification blob that the bootkit later decrypts to validate entered keys.
The installer backs up bootmgfw.efi to bootmgfw.efi.old, forces a BSOD (NtRaiseHardError) so the system reboots into the replaced bootflow and executes the bootkit. HybridPetya is the fourth known UEFI bootkit with Secure Boot bypass after BlackLotus, BootKitty, and the Hyper-V Backdoor PoC (exploiting CVE-2020-26200).
"Although HybridPetya is not actively spreading, its technical capabilities – especially MFT encryption, UEFI system compatibility, and Secure Boot bypass – make it noteworthy for future threat monitoring," concludes the report.
A Growing Threat Landscape
HybridPetya's capabilities demonstrate a growing trend in attacks that are exploiting vulnerabilities in UEFI systems. As threat actors continue to push the boundaries of what is possible, it is essential to stay informed and vigilant about emerging threats like HybridPetya.
A New Normal for Cybersecurity
HybridPetya's discovery serves as a reminder that cybersecurity is an ongoing battle. The importance of staying up-to-date with the latest security patches, monitoring system logs, and implementing robust threat detection mechanisms cannot be overstated.
By staying informed about emerging threats like HybridPetya, individuals and organizations can better prepare themselves for the challenges of this evolving threat landscape.
Stay Informed
To stay up-to-date with the latest cybersecurity news and analysis, follow us on Twitter (@securityaffairs) and Facebook. You can also join our Mastodon community to discuss the latest security topics with fellow enthusiasts.
By joining the conversation, you'll be better equipped to navigate the ever-changing landscape of cyber threats like HybridPetya.