Phishing Attack Nets Enormous npm Supply Chain Compromise
A devastating phishing attack has left one of the largest supply chain compromises to date, compromising JavaScript packages with around 2.7 billion weekly downloads.
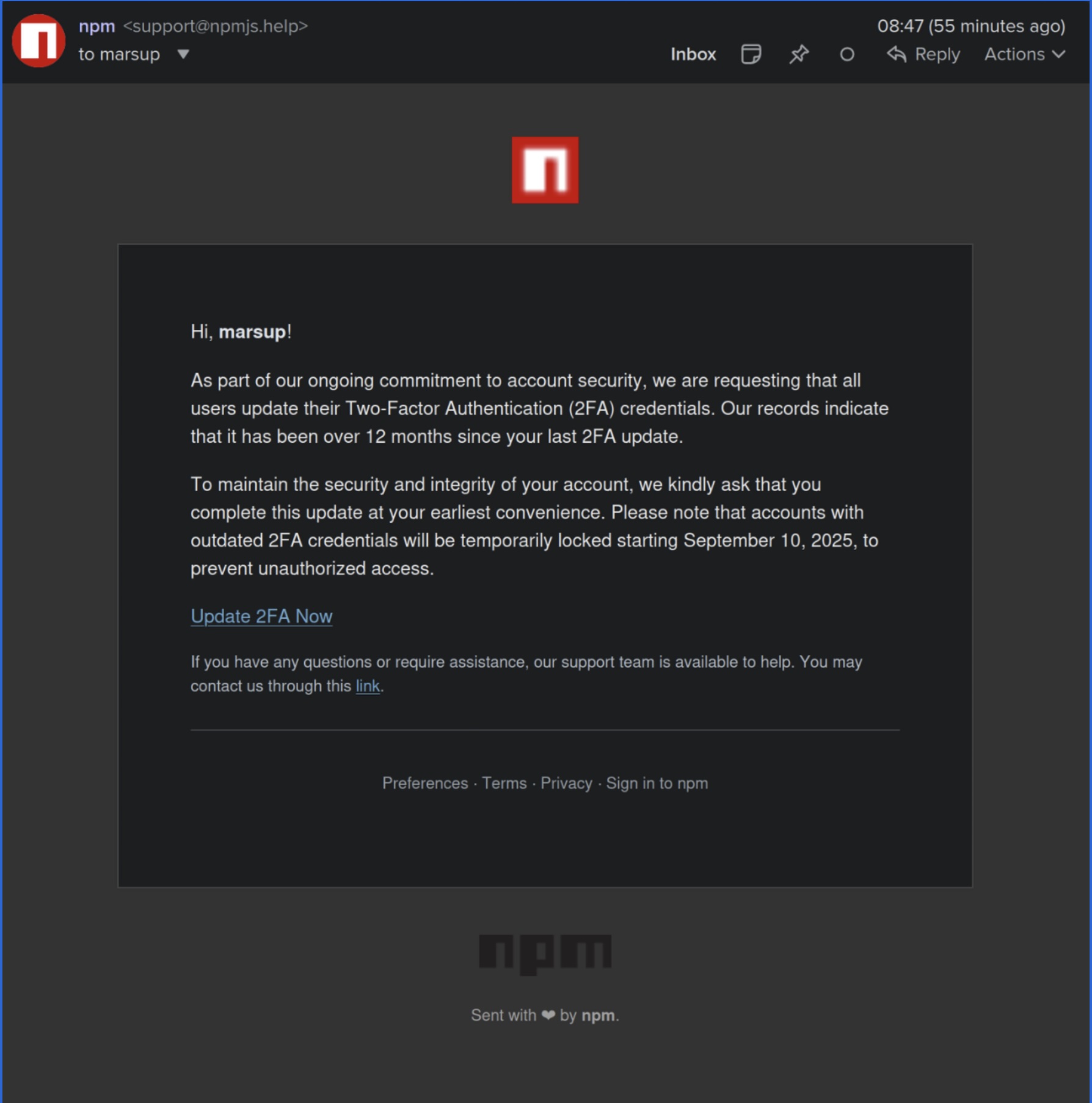
Developers targeted in this new hacking campaign received very legitimate-looking phishing emails from "support@npmjs.help," asking them to update their two-factor authentication (2FA) credentials. The npm acronym stands for node package manager, a registry acting as a massive database with reusable code, containing over 2 million items.
The attack on the npm developer community began when one developer, Josh "qix" Junon, fell prey to the phishing message and lost control of his account. This was just the beginning, as the successful phishing attack resulted in at least 18 very popular npm packages being compromised, with around 2.7 billion downloads a week.
Security vendor Aikido analyzed the malicious code and revealed that it would be executed on the client-side of a website, silently intercepting crypto and web3 activity in the browser, manipulating wallet interactions, and rewriting payment destinations to redirect funds and approvals to attacker-controlled accounts without any obvious signs to the user.
Following the discovery of the compromise, package clean-up efforts are underway. However, it appears that other developers are currently being targeted as well by this unknown threat actor.
This large-scale compromise follows another successful attack on the popular Nx package and plugins for it at the end of August. The s1ngularity attack was caused by a vulnerable workflow that allowed executable code to be injected into a pull request title, with artificial intelligence command line tools being abused for local file system scans.
Thousands of corporate secrets were leaked and published on GitHub in the s1ngularity repository from over 1700 users. The success of these attacks highlights the importance of robust security measures for developers working with sensitive information.
The npmjs.help Domain: A New Front in the War Against Phishing
The attacker-controlled domain "npmjs.help" was registered just three days ago, demonstrating the speed and sophistication of modern phishing campaigns. This new development raises concerns about the ability of threat actors to quickly adapt and evolve their tactics.
Protecting Yourself from npm Supply Chain Compromise
To avoid falling victim to similar attacks, developers are advised to exercise extreme caution when receiving unexpected emails or requests for sensitive information. It is essential to verify the authenticity of any communication before responding or taking action.
A thorough review of your account settings and security protocols can help prevent such breaches. Keeping your software up-to-date and using strong passwords can also reduce the risk of compromise.
The Future of npm Security: A Call for Vigilance
The recent npm supply chain compromise serves as a stark reminder of the importance of robust security measures in the developer community. As threat actors continue to evolve, it is crucial that developers and security vendors remain vigilant and proactive in defending against such attacks.