SVG Files Used in Hidden Malware Campaign Impersonating Colombian Authorities
A recent malware campaign has been uncovered by VirusTotal researchers, using SVG files to impersonate the Colombian justice system and deploy malicious software. The campaign, which went undetected by antivirus tools for a significant period, is a stark reminder of the evolving threats in the cybersecurity landscape.
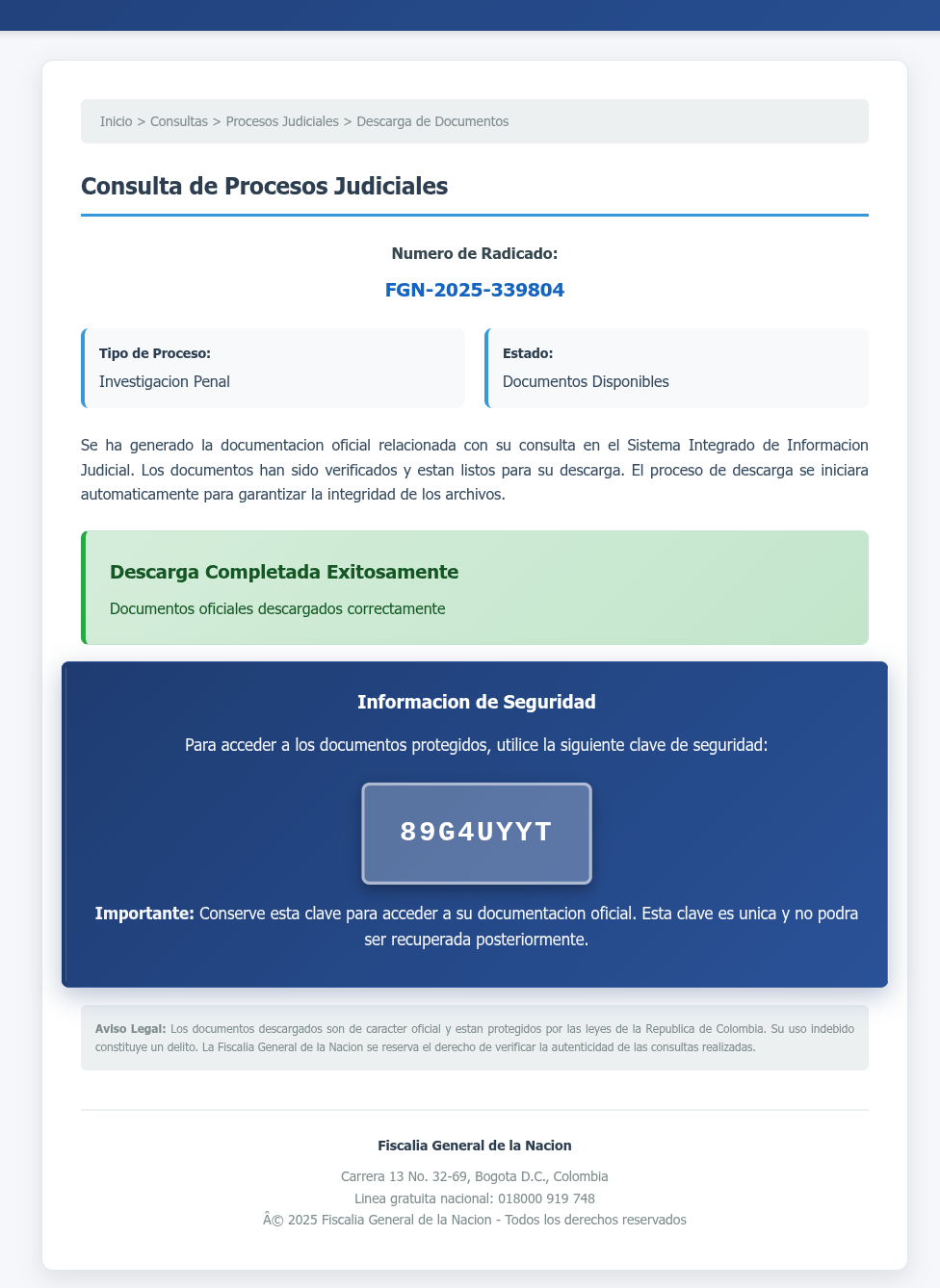
According to VirusTotal, the campaign used SVG files with hidden JavaScript to create fake Fiscalía General de la Nación login pages in Colombia. The files were designed to trick victims into downloading and executing malware, which would then spread across their devices.
The use of SVG files in this campaign is a unique twist on traditional phishing attacks, which often rely on HTML-based lures. However, the use of XML-based files like SVGs can make them more difficult for antivirus tools to detect.
The Abuse of SWF and SVG Files
VirusTotal researchers noted that despite being outdated, SWF (Shockwave Flash) files are still being used in attacks. In fact, the platform logged 47,812 unique SWFs in 30 days, with 466 flagged as malicious.
Furthermore, the study found that SVGs remain widely abused by threat actors. With 140,803 unique SVGs reported, only about 1% of which were flagged as malicious by at least one antivirus engine. Attackers often hide malicious JavaScript, redirects, or obfuscation in these files, making them difficult to analyze.
One recent case highlighted the dangers of relying solely on traditional antivirus tools for protection. A seemingly harmless SVG file, with zero detections on VirusTotal, was revealed to contain hidden JavaScript that built a fake Colombian judicial portal and delivered a malicious ZIP file.
The Importance of Deeper Analysis
This single SVG pulled double duty as both a phishing lure and a malware dropper – a perfect example of why traditional AV alone isn’t enough. A deeper analysis by Code Insight revealed the truth behind this seemingly innocuous file, exposing it for what it truly was: a sophisticated piece of malware.
Code Insight, which added SVG support recently, uncovered 44 malicious SVGs, all invisible to antivirus tools but flagged by its advanced analysis capabilities. The attackers used various techniques such as obfuscation, polymorphism, and dummy code to evade detection.
The experts even discovered a simple YARA rule that caught 523 samples dating back to August 2025. While the first payloads were large and heavy, later versions became lighter and were mostly delivered through email.
Conclusion
"SWF and SVG are very different formats from very different eras, but both can still cause headaches for analysts," concludes the report. "In the first case, Code Insight helped explain why a SWF file looked suspicious without actually being malicious. In the second, it uncovered malicious behavior in an SVG that had gone completely undetected."
This study serves as a reminder of the need for ongoing vigilance and the importance of using advanced threat detection tools to stay ahead of evolving malware campaigns.