Amazon Blocks APT29 Campaign Targeting Microsoft Device Code Authentication
Amazon has disrupted a sophisticated watering hole campaign orchestrated by the Russia-linked cyber espionage group APT29 (also known as SVR group, Cozy Bear, Nobelium, BlueBravo, Midnight Blizzard, and The Dukes), which aimed to hijack Microsoft device code authentication via compromised sites.
The Attack: A Sophisticated Watering Hole Campaign
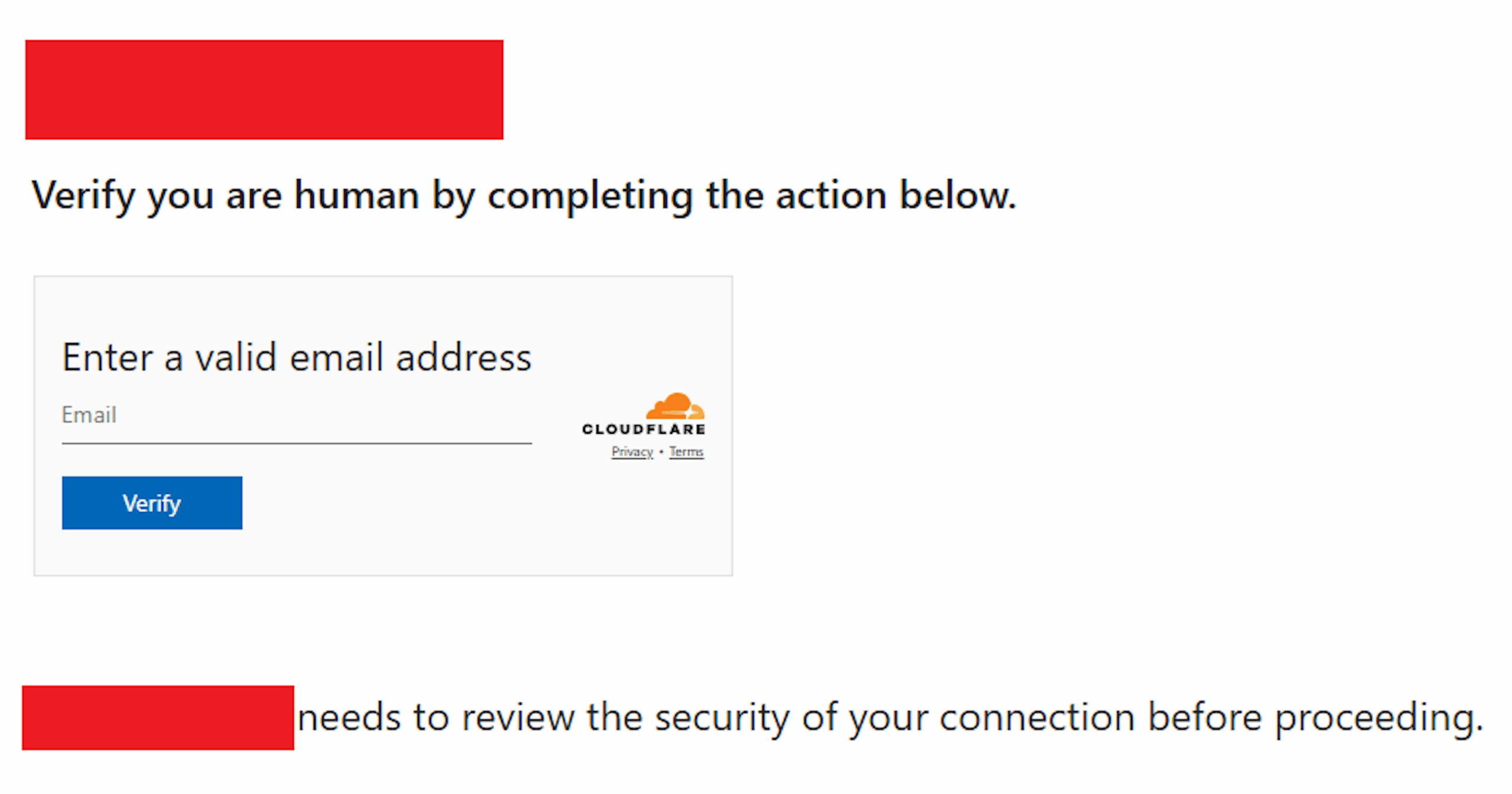
Apt29 has continued its evolution in scaling its operations, with the latest watering hole campaign showcasing refined tradecraft. The attackers injected obfuscated JavaScript into legitimate sites, redirecting around 10% of visitors to capture Microsoft device code authentication credentials.
The tactics employed by Apt29 were diverse and cunning. They used randomization, base64 encoding, cookies, and rapid infrastructure pivots to evade detection. The campaign specifically targeted academics and Russia critics in an effort to gather intelligence.
Amazon's Disruption: A Collaborative Effort
Amazon's threat intelligence team identified the watering hole campaign through custom analytics, discovering actor domains such as findcloudflare[.]com mimicking Cloudflare pages. The attackers had attempted to migrate their operations from AWS to another cloud provider, but Amazon continued to track and disrupt their activities.
Working with Cloudflare and Microsoft, Amazon isolated the affected EC2 instances and blocked malicious domains. This collaborative effort not only disrupted Apt29's operations but also helped to prevent further exploitation of compromised sites.
The Aftermath: Recommendations for Users and Administrators
Amazon's report highlights the importance of vigilance in protecting against cyber threats. The organization provides recommendations for users and administrators, including the need to stay up-to-date with security patches, use strong passwords, and be cautious when clicking on links or accessing suspicious websites.
"Despite our intervention, we observed the actor registering additional domains such as cloudflare[.]redirectpartners[.]com, which again attempted to lure victims into Microsoft device code authentication workflows," concludes the report. This highlights the ongoing threat posed by Apt29 and the need for continued vigilance in the face of evolving cyber threats.
Conclusion
The disruption of this watering hole campaign by Amazon serves as a reminder of the importance of cybersecurity awareness and cooperation between organizations. By staying informed and taking proactive steps to protect against cyber threats, individuals and organizations can help prevent the spread of malicious activity.
FOLLOW US ON TWITTER: @securityaffairs
Stay Connected:
Facebook: @securityaffairs
Mastodon: @securityaffairs
Note: The HTML code is designed to provide better readability, with headings, paragraphs and links to social media profiles.