DOJ Takes Action Against 22-Year-Old RapperBot Botnet Operator
The U.S. Department of Justice (DOJ) has taken action against 22-year-old Ethan Foltz, the administrator of the notorious RapperBot botnet, a Distributed Denial-of-Service (DDoS) for-hire service responsible for over 370,000 attacks in more than 80 countries since 2021.
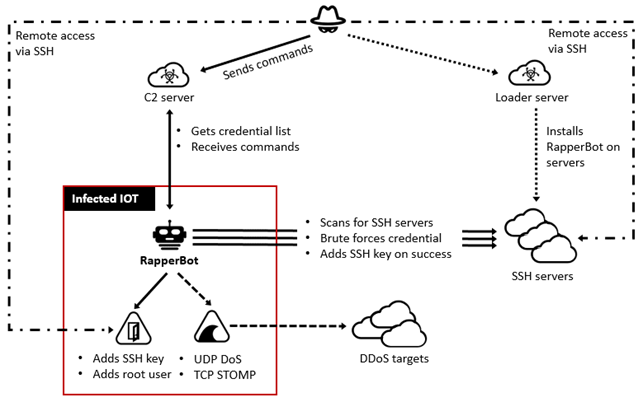
Foltz, identified as the mastermind behind the RapperBot botnet, allegedly developed and managed the service, which enabled large-scale disruptions and impacted victims globally. The botnet, also known as Eleven Eleven Botnet or CowBot, infects DVRs and routers to launch massive DDoS attacks worldwide on command.
According to a press release published by the DOJ, RapperBot allegedly utilized roughly 65,000 to 95,000 infected victim devices to regularly conduct DDoS attacks that commonly measured between two to three Terabits per second. The largest attack may have exceeded six Terabits per second.
Investigators believe that at least five infected victim devices are located in Alaska and were forced to participate in attacks. Researchers from FortiGuard Labs first discovered the RapperBot botnet in August 2022, but they speculate it had been active since 2021.
The bot borrows a large portion of its code from the original Mirai botnet, but unlike other IoT malware families, it implements built-in capability to brute force credentials and gain access to SSH servers instead of Telnet as implemented in Mirai. Threat actors used the RapperBot botnet to launch DDoS attacks against victims and extort them.
On August 6, 2025, law enforcement seized Rapper Bot and gained control of the infrastructure, halting all attacks. Foltz faces one count of aiding computer intrusions, with up to 10 years in prison.
Disruption of the RapperBot Botnet
"Rapper Bot was one of the most powerful DDoS botnets to ever exist, but the outstanding investigatory work by DCIS cyber agents and support of my office and industry partners has put an end to Foltz’s time as administrator and effectively disrupted the activities of this transnational criminal group," said U.S. Attorney Michael J. Heyman for the District of Alaska.
"Our office remains committed to disrupting and dismantling cyber criminals that threaten internet security and infrastructure in the District of Alaska and across the United States."
"Today’s announcement highlights the ongoing efforts by law enforcement to disrupt and dismantle emerging cyber threats targeting the Department of Defense and the defense industrial base," said Special Agent in Charge Kenneth DeChellis of the Department of Defense Office of Inspector General, DCIS, Cyber Field Office.
Amazon Web Services Helps Disrupt RapperBot Botnet
"The Rapper Bot malware was a clear threat, and the focused efforts of DCIS, our industry partners, and the federal prosecutors at the U.S. Attorney’s Office in Alaska, sends a clear signal to those who would harm the DoD’s personnel, infrastructure, and intellectual property, that their actions will come at a cost,"
Amazon Web Services (AWS) played a crucial role in disrupting the RapperBot botnet. AWS aided the DOJ by mapping Rapper Bot’s C2 infrastructure and analyzing its IoT malware, helping halt attacks and improve overall internet security.