**The Evolution of Noodlophile: A Sophisticated Malware Campaign**
The world of cyber threats is constantly evolving, and one malware that has been making headlines recently is Noodlophile Stealer. This sophisticated threat actor has been active for over a year, targeting firms in the U.S., Europe, the Baltics, and APAC with tailored spear-phishing lures.
**A New Form of Malware**
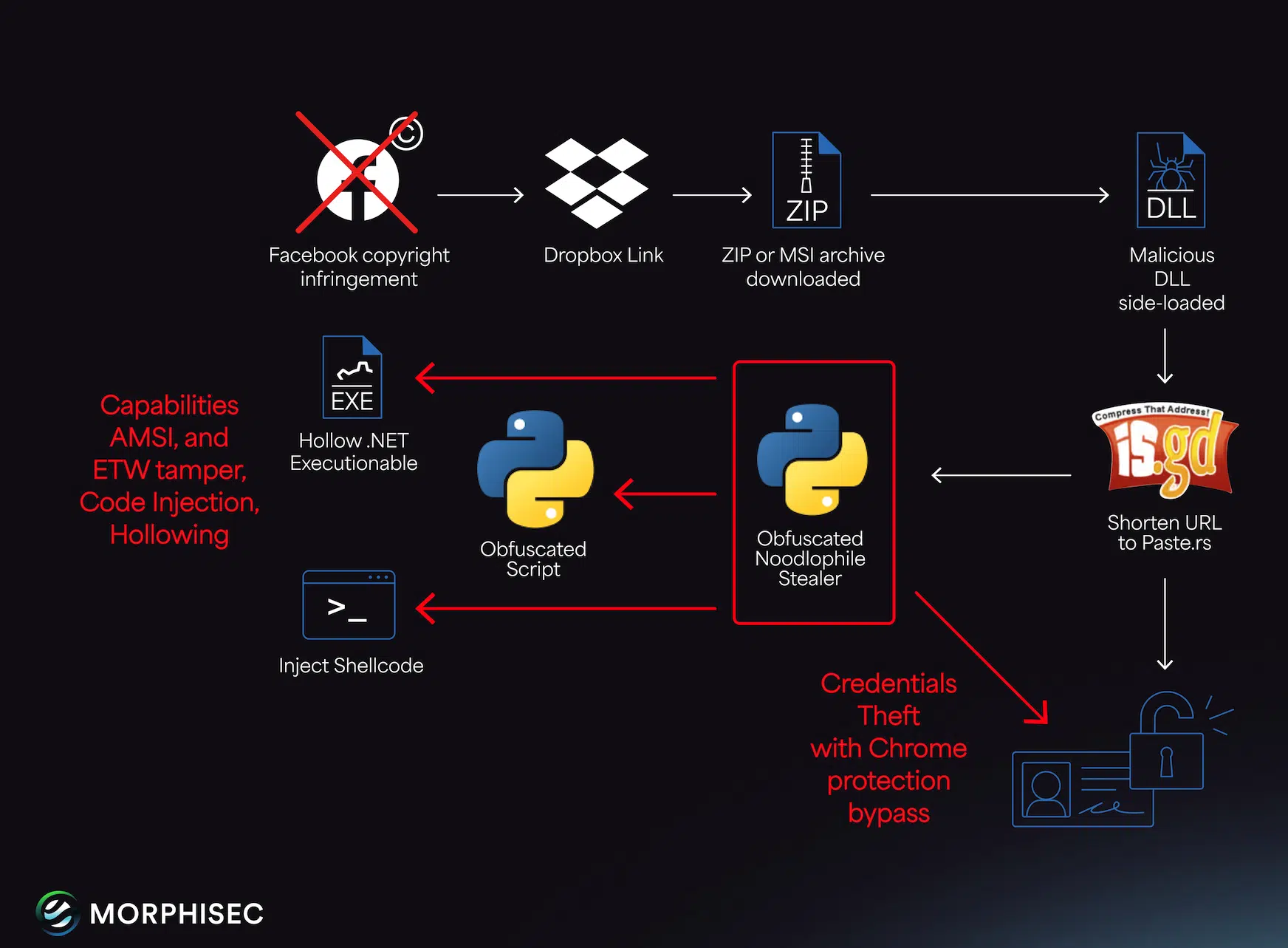
Noodlophile Stealer is a type of malware that steals browser credentials, crypto wallets, and may install remote access trojans like XWorm. What makes this malware stand out is its ability to target enterprises and individuals alike, using advanced spear-phishing emails posing as copyright infringement notices.
**How It Spreads**
The Noodlophile campaign exploits legit software flaws, uses Telegram for staging, and delivers dynamic payloads via urgent Gmail lures claiming Facebook copyright violations. The threat actors tailor their lures with details like Facebook Page IDs and company ownership data, making it difficult for recipients to distinguish between legitimate and malicious emails.
**Spear-Phishing Emails**
The spear-phishing emails are highly personalized, often originating from Gmail accounts to evade suspicion. They include precise details such as Page IDs and ownership information, indicating extensive reconnaissance. The urgent tone and legal threats pressure recipients to click on malicious links disguised as evidence files.
**DLL Side-Loading and Payloads**
Once the malicious DLLs are side-loaded into signed apps like Haihaisoft PDF Reader, the payloads are disguised as .docx or .png files, enabling covert execution inside trusted processes. The payloads are then executed through a series of obfuscated stages, using recursive stub loading and chained DLL flaws.
**Obfuscation and Evasion**
The Noodlophile campaign exploits advanced techniques to evade detection. Malicious scripts disguised as .docx files no longer fetch payloads directly but instead extract download links hidden in Telegram group descriptions. This approach complicates detection and takedown, making it harder for security teams to identify and remove the malware.
**Free Hosting Sites**
The final stealer is hosted on free platforms like Paste.rs, a tactic that complicates detection and takedown. The malware code includes placeholders for future functions like screenshot capture, keylogging, file exfiltration, and even file encryption.
**Expanding Capabilities**
The Noodlophile Stealer's code suggests rapid expansion, making it a growing threat to enterprises. Its ability to target sensitive browser data, including cookies, credentials, and credit cards, with a strong focus on stealing Facebook cookies is particularly concerning.
**Conclusion**
Noodlophile Stealer is a sophisticated malware campaign that targets enterprises and individuals alike. Its advanced spear-phishing emails and use of Telegram for staging make it difficult to detect and remove. As the threat actor continues to evolve, it's essential for organizations to remain vigilant and implement robust security measures to protect themselves against this growing threat.
**Stay Safe Online**
If you're a business owner or individual looking to protect yourself from malware threats like Noodlophile Stealer, here are some tips:
* Be cautious when receiving emails that claim to be from legitimate sources * Use strong passwords and two-factor authentication whenever possible * Keep your software up to date and use anti-virus software * Use a reputable security suite that includes features like email filtering and web protection
By staying informed and taking proactive steps, you can reduce your risk of falling victim to malware threats like Noodlophile Stealer.