Xerox Fixed Path Traversal and XXE Bugs in FreeFlow Core
In a significant move to address security concerns, Xerox has patched two serious flaws in its print automation and workflow management platform, FreeFlow Core. The vulnerabilities, tracked as CVE-2025-8355 and CVE-2025-8356, allowed unauthenticated remote code execution, posing a significant threat to the users of this software.
Path Traversal Vulnerability (CVE-2025-8355)
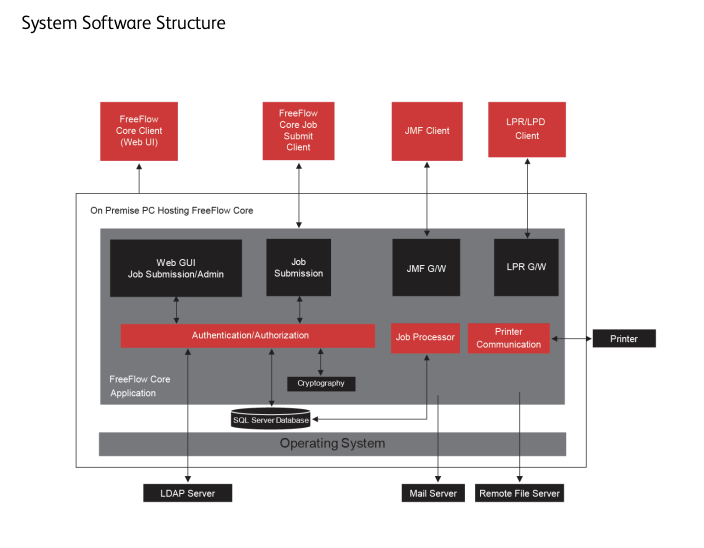
The path traversal vulnerability, CVE-2025-8355, is a critical issue that allows an attacker to inject malicious XML and execute SSRF attacks. According to cybersecurity firm Horizon3's report, this vulnerability was discovered in Xerox FreeFlow Core's JMF Client service. The experts found that the improperly sanitized XML enabled attackers to exploit this flaw.
XXE Injection Vulnerability (CVE-2025-8356)
The XXE injection vulnerability, CVE-2025-8356, is another critical issue that allows an attacker to inject malicious code into the system. In this case, a path traversal vulnerability in file-handling routines was discovered, enabling attackers to place webshells in publicly accessible locations. This combined with the JMF Client service vulnerability, allowed remote attackers to execute malicious payloads through JMF commands and leverage web portals for delivery.
Risk Assessment
According to Horizon3's report, FreeFlow Core installations have a lot of moving parts and require relatively open access and availability. This makes them an ideal target for attackers, especially considering that print jobs often contain pre-public information around marketing campaigns. The combined impact of these vulnerabilities allows remote attackers to execute malicious payloads through JMF commands and leverage web portals for delivery.
Patch and Recommendation
Xerox has addressed both issues in FreeFlow Core version 8.0.5, providing users with a patch to upgrade as soon as possible. Given the severity of these vulnerabilities, it is essential for users to take immediate action to ensure their systems are protected.
Follow us on Twitter: @securityaffairs and Facebook and Mastodon for more updates on cybersecurity threats and solutions.