Shade BIOS: Stealth Malware Hides Below Operating System
A new type of stealth malware has been discovered that can hide below a computer's operating system, making it nearly undetectable to endpoint detection and response tools. According to researchers, this "Shade BIOS" malware uses the Basic Input/Output System (BIOS) and Unified Extensible Firmware Interface (UEFI) code that starts up devices and loads the operating system, allowing attackers to access devices, communicate with command-and-control (C2) servers, and exfiltrate data without ever touching OS application programming interfaces (APIs).
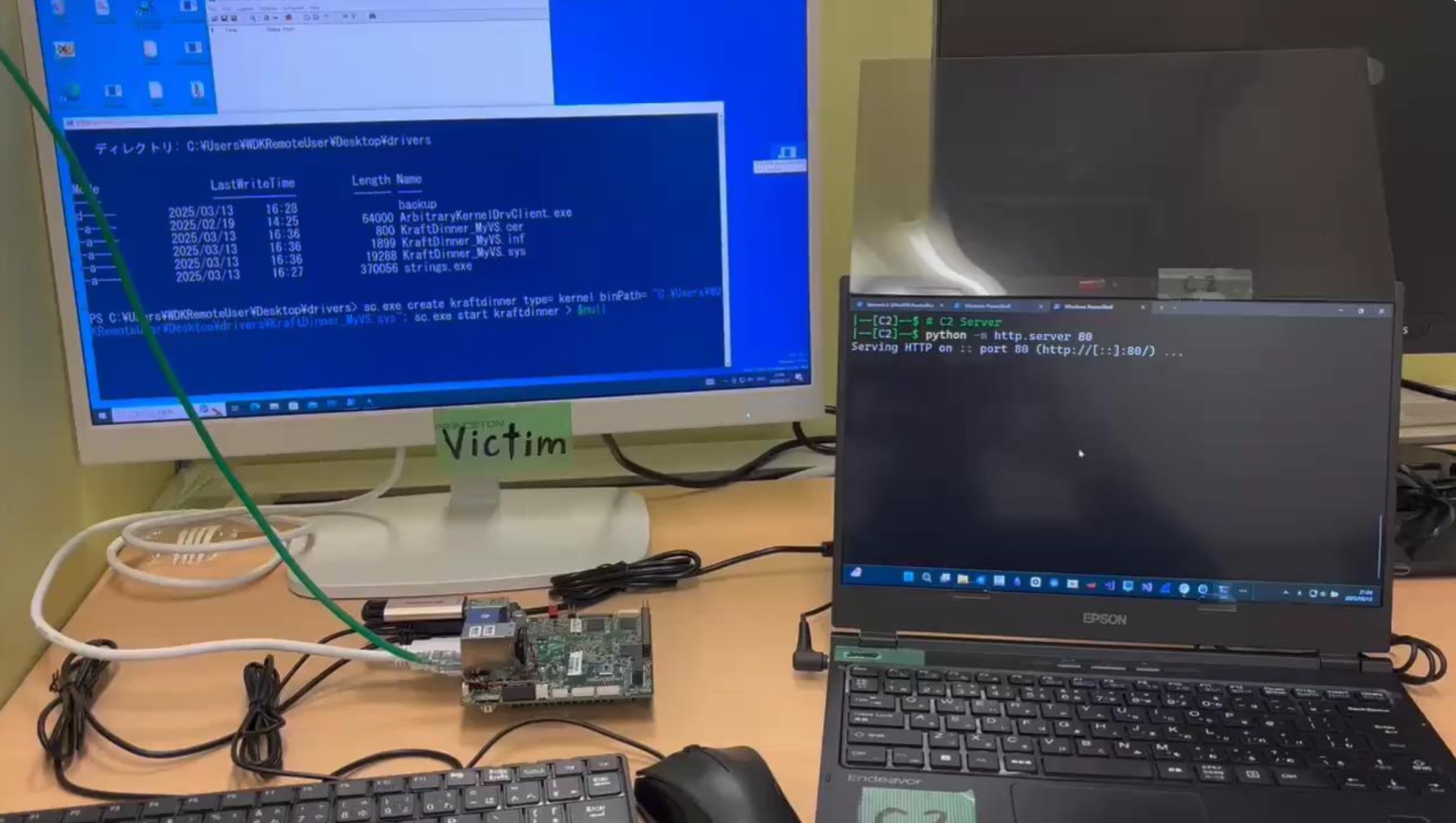
Kazuki Matsuo of Japan's FFRI Security specializes in research covering computers' BIOS and UEFI, the code that starts up devices and loads the operating system. While the firmware-stored computer startup code would normally be flushed after the OS starts up and resumes control, Matsuo's Shade BIOS malware prevents this.
Instead, Shade BIOS retains BIOS memory regions that would normally be overwritten, and keeps UEFI drivers and protocols active, maintaining device access that would normally be under OS control. This allows attackers to remain undetected by traditional security measures, which rely on monitoring API calls made by applications running above the OS level.
The difference between Matsuo's Shade BIOS and traditional BIOS backdoors lies in its use of existing UEFI drivers and protocols, making it easier to write and more compatible with different hardware configurations. This means that identical Shade BIOS code can work across various devices without modification, posing a significant challenge for security researchers and defenders.
Shade BIOS addresses several technical challenges, including run-time memory management, virtualized memory addresses, boot time resources, device settings conflicts, and exclusive control between UEFI/BIOS and OS code. In effect, Shade BIOS becomes an "attacker-exclusive OS" that runs alongside the legitimate operating system, nearly undetectable.
While not directly detectable, Shade BIOS temporarily disrupts device operation during malicious activity, such as network cards losing connectivity briefly or monitoring for similar devices errors becoming an indication of Shade BIOS activity. Researchers are advised to look out for these signs and monitor for frequently occurring device errors that could be indicative of the malware's presence.
Evidence from leaked intelligence documents suggests that nation-state actors are focusing on UEFI/BIOS exploits, with tools such as DerStarke, DEITYBOUNCE, BANANABALLOT, and the commercial vector-edk BIOS hacking kit sold to governments. The research was presented at the recent Black Hat USA 2025 security conference, and a proof of concept (PoC) of Shade BIOS has been published by Matsuo.
Researchers are urged to stay vigilant and update their security measures to counter this new type of stealth malware that is hiding in plain sight. The emergence of Shade BIOS highlights the importance of addressing UEFI/BIOS vulnerabilities and improving endpoint detection and response capabilities to detect and respond to emerging threats like this.