BadCam: Linux-based Lenovo Webcam Bugs Enable BadUSB Attacks
Recently, Eclypsium researchers have uncovered a critical security vulnerability in certain Lenovo webcams that can be exploited by attackers to turn them into malicious devices, dubbed BadUSB. This bug has significant implications for users of these webcams, as it enables BadUSB-style attacks that can inject keystrokes and launch OS-independent attacks.
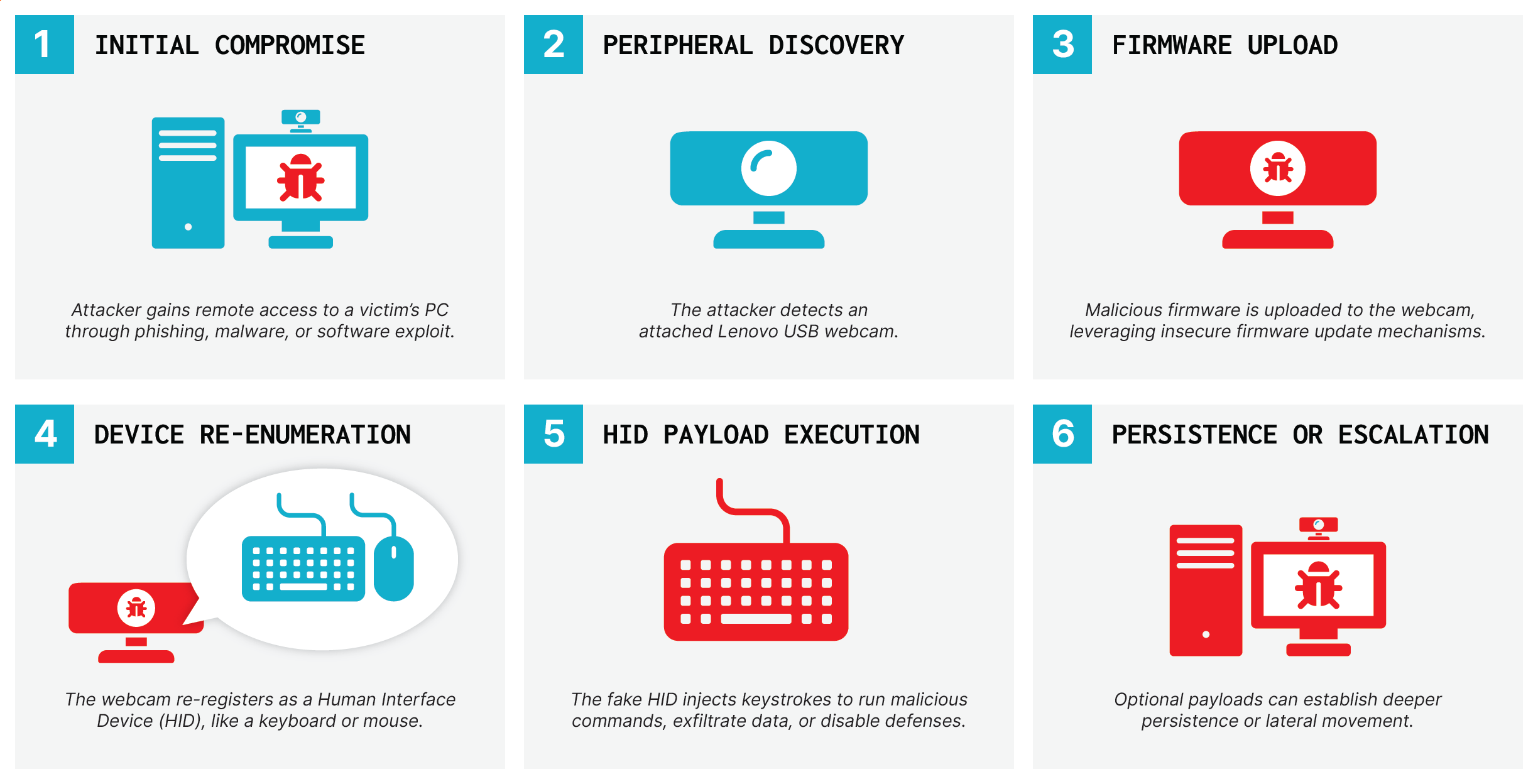
The vulnerabilities were discovered in select model webcams from Lenovo that run Linux and do not validate firmware. These webcams can be easily weaponized as BadUSB devices by reflashing their firmware, allowing attackers to bypass OS defenses and execute malicious commands.
A New Level of Threat
BadUSB exploits trust in USB devices by reprogramming firmware to mimic HIDs (Human Interface Devices) and execute malicious commands. This type of attack is stealthy, modular, and persistent, often evading detection and enabling data theft, privilege escalation, and ransomware.
First demonstrated at Black Hat 2014 by Karsten Nohl and Jakob Lell, BadUSB has now been weaponized with tools like Rubber Ducky, Flipper Zero, and open-source payloads. The attack is made possible by the Linux USB gadget feature, which enables devices to mimic trusted peripherals.
A Remote Hijacking Exploit
Eclypsium researchers demonstrated that Linux-based USB peripherals, such as webcams, can be remotely hijacked and converted into BadUSB devices without requiring physical access. By reflashing firmware, attackers can make them act as malicious HIDs, inject payloads, or persistently re-infect hosts, even after users reinstall the operating systems.
This marks a notable evolution in the BadUSB threat landscape: an attacker who gains remote code execution on a system can reflash the firmware of an attached Linux-powered webcam, repurposing it to behave as a malicious HID or to emulate additional USB devices.
A Vulnerable Web Cam Flaw
Eclypsium discovered that Lenovo 510 FHD and Performance FHD webcams are vulnerable to insecure firmware updates, allowing full camera compromise. Both use SigmaStar ARM-based SoCs running Linux with USB Gadget support, enabling BadUSB-style attacks to hijack a host.
The Update Process Lacks Safeguards
Researchers found that the update process lacks safeguards, simple USB commands can erase and overwrite the 8MB SPI flash, letting attackers replace firmware and weaponize the camera while retaining normal functionality.
A Fix is on the Way
Lenovo responded by creating an updated installation tool with signature validation to fix the flaw. Users of the impacted webcams should download the update from Lenovo's support site to mitigate risks.
The company worked with SigmaStar to assess and address the vulnerability promptly. Eclypsium urges organizations to add firmware verification to affected SoCs.
Why This Matters
"As device supply chains continue to diversify and USB peripherals grow more complex, these attacks underscore the urgent need for firmware signing, device attestation, and more granular visibility into precisely what is plugged into enterprise endpoints," concludes the report. "With BadUSB now possible through not just physical access but also remote manipulation of everyday peripherals, organizations must rethink both endpoint and hardware trust models."