Embero ransomware, likely a BlackCat/Alphv successor, has netted $34.2M in crypto since mid-2024
Researchers from Blockchain intelligence company TRM Labs have identified approximately USD 34.2 million in incoming transaction volume likely associated with the Embargo ransomware group, which emerged in April 2024.
The group has primarily targeted US healthcare, business services, and manufacturing sectors, with victims including American Associated Pharmacies, Memorial Hospital and Manor (GA), and Weiser Memorial Hospital (ID). Ransom demands have reached up to $1.3M.
TRM Believes Embargo is a BlackCat/Alphv Successor
TRM Labs assesses that Embargo is likely a BlackCat/Alphv successor based on multiple technical and behavioral similarities, including using the Rust programming language, a similarly designed data leak site, and on-chain overlaps via shared wallet infrastructure.
The group's use of AI and ML to scale attacks, create convincing phishing lures, adapt malware, and speed up its operations has also been observed by researchers.
Laundering Ransom Proceeds and Evasion Tactics
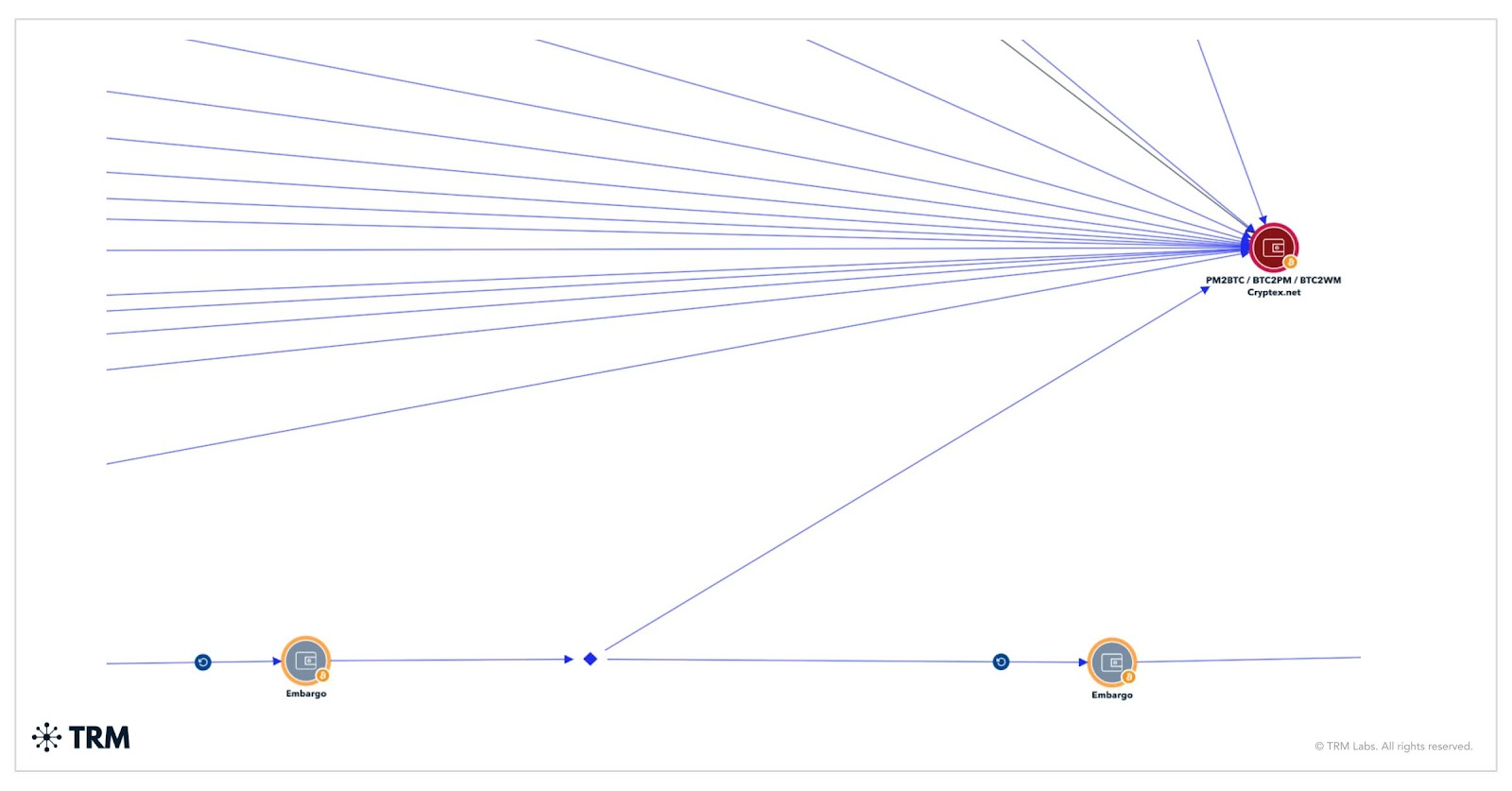
The experts discovered that the group is laundering ransom proceeds through intermediary wallets, high-risk exchanges, and sanctioned platforms such as Cryptex.net.
Approximately USD 18.8 million remains dormant in unattributed wallets, suggesting a deliberate evasion tactic to avoid detection.
A Politically Charged Threat Actor
Embero, though financially driven, has used politically charged messages, hinting at possible links with states. This suggests that the group may be using its attacks as leverage for political influence or extortion.
The group mainly targets healthcare, business services, and manufacturing for maximum disruption, often in the US but also in Europe and Asia. Healthcare attacks risk patient care, reflecting a trend of exploiting critical services for leverage.
Threat Analysis: Double Extortion and Phishing
Embero exploits unpatched flaws or uses phishing as initial access vectors, then disables defenses, removes recovery options, before encrypting the files. It controls negotiations via its infrastructure and runs a leak site to pressure non-paying victims, sometimes naming individuals.
The group also threatens to sell or leak stolen data, amplifying financial, reputational, and regulatory risks.
Conclusion: Collaboration is Key
"While AI is accelerating the scale and sophistication of ransomware attacks, it's also becoming a critical tool in stopping them," concludes the report. "Companies are using AI to detect signs of compromise — such as unusual access behavior and file encryption patterns."
"Effectively countering ransomware threats requires collaboration between the public and private sectors," adds the report.