Over 100 Dell Models Exposed to Critical ControlVault3 Firmware Bugs
A recent discovery by cybersecurity experts at Cisco Talos has left over 100 laptop models from Dell vulnerable to critical firmware bugs, known as ReVault flaws. These vulnerabilities allow attackers to implant malware and bypass Windows login credentials via physical access, posing a significant threat to user data and system security.
The Flaws: A Threat to User Data and System Security
ReVault, collectively tracked as CVE-2025-24311, CVE-2025-25215, CVE-2025-24922, CVE-2025-25050, and CVE-2025-24919, is a hardware-based security module found in various Dell laptop models. It is designed to provide a secure environment for storing and processing sensitive data such as user passwords, biometric information, security codes, and encryption keys.
The ReVault attack can be used as a post-compromise persistence technique that can remain even across Windows reinstalls. This means that once an attacker gains access to the firmware, they can remain undetected even after a system is reinstalled or updated. Additionally, attackers can use the vulnerabilities to bypass Windows login and/or gain local admin privileges.
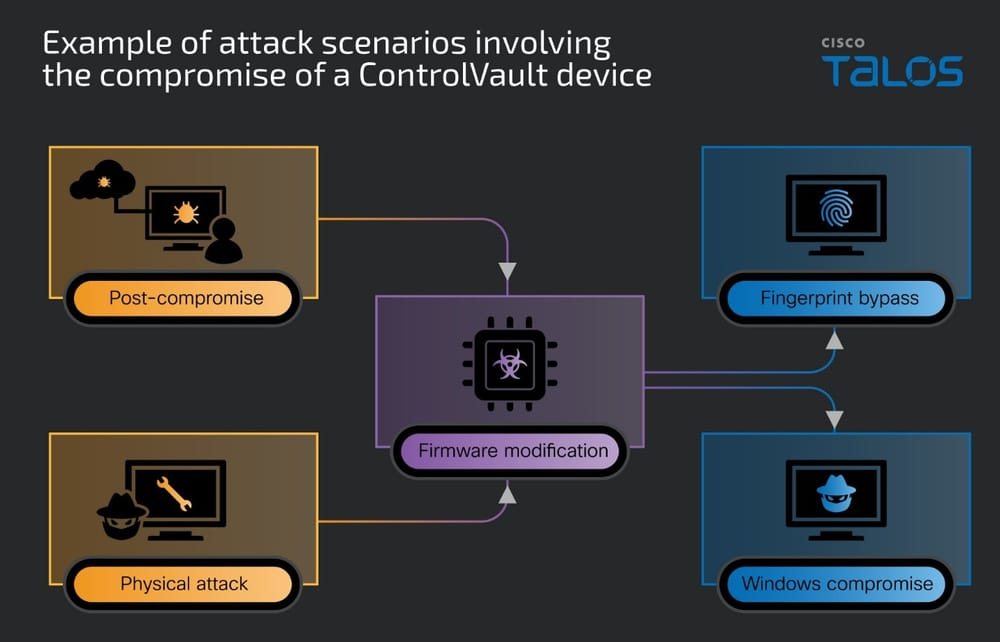
Attack Scenarios: A Wake-Up Call for Cybersecurity
The impact of these vulnerabilities is severe due to both the lack of standard security mitigations and the ability to chain certain flaws. In one attack scenario, a non-admin Windows user could exploit the vulnerabilities to execute arbitrary code in the firmware, exposing sensitive cryptographic material and allowing permanent firmware modification.
In another scenario, a local attacker with physical access could bypass login and disk encryption by connecting directly to the firmware hardware, even tricking the system into accepting fake fingerprints if biometric login is enabled. This highlights the importance of having robust security measures in place to protect against such threats.
What You Can Do to Protect Yourself
To reduce the risk of attack, Cisco Talos advises keeping systems updated with the latest firmware, which can be installed via Windows Update or manually from Dell’s website. If security peripherals like fingerprint or smart card readers aren’t in use, ControlVault (CV) services or devices can be disabled through the Service or Device Manager.
In high-risk situations, it is recommended to disable fingerprint login and consider using Windows’ Enhanced Sign-in Security (ESS) to detect tampered firmware. Additionally, enabling chassis intrusion alerts in BIOS can flag physical tampering, and unusual crashes in biometric or credential services may indicate compromise.
A Call to Action: Stay Vigilant and Patch Your Systems
Cisco Secure Endpoint can also detect suspicious behavior linked to CV exploitation. The discovery of these ReVault flaws highlights the importance of evaluating the security posture of all hardware components within your devices, not just the operating system or software.
"Staying vigilant, patching your systems and proactively assessing risk are essential to safeguard your systems against evolving threats," concludes Cisco Talos. "These findings underscore the importance of ongoing security monitoring and proactive measures to protect against emerging vulnerabilities."