Nation-state group CL-STA-0969 targeted Southeast Asian telecoms in 2024
In a concerning report published by Palo Alto Networks' Unit 42, it has been revealed that a nation-state actor, tracked as CL-STA-0969, targeted critical infrastructure of telecommunications firms in Southeast Asia between February and November 2024. This sophisticated attack highlights the evolving nature of cyber threats and the need for robust security measures.
A Threat Actor with Sophisticated Ties
The threat actor CL-STA-0969 is believed to overlap with other known groups, including the China-linked cyber espionage group Liminal Panda, as well as Light Basin, UNC3886, UNC2891, and UNC1945. The group's tactics, techniques, and procedures (TTPs) demonstrate a high level of expertise in exploiting vulnerabilities in telecommunications infrastructure.
Tools of the Trade
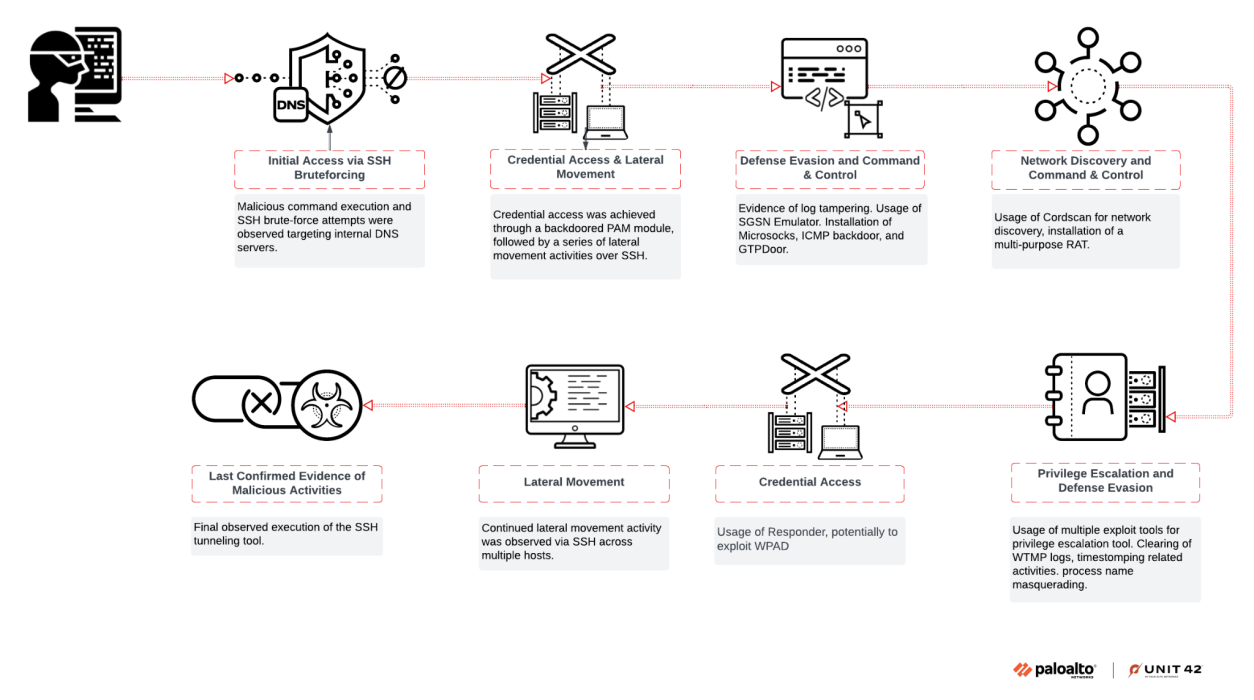
The researchers at Palo Alto Networks identified several tools used by CL-STA-0969, including:
* Custom tools like AuthDoor, GTPDoor, ChronosRAT, and NoDepDNS * Exploits for known vulnerabilities such as CVE-2016-5195, CVE-2021-4034, and CVE-2021-3156 * Microsocks, FRP, FScan, and Responder
Stealthy Tactics
The group demonstrated strong operational security (OPSEC) measures to stay undetected. These included:
* DNS tunneling * Routing via compromised mobile networks * Log clearing * Disguising process names * PAM backdoors
Brute-Force Attacks and Exploits
The researchers found that the group likely gained initial access through brute-force attacks on authentication systems. Using custom tools like AuthDoor, GTPDoor, ChronosRAT, and NoDepDNS, they exploited telecom protocols such as SSH, ICMP, DNS, and GTP for covert access and command-and-control.
Resilient Remote Access
The group set up resilient remote access, likely for future espionage operations. This suggests that CL-STA-0969 is a persistent threat actor with a long-term presence in the targeted infrastructure.
Conclusion
Despite their high level of OPSEC, substantial evidence points to attackers gaining initial access via SSH brute force. The report concludes that organizations relying on legacy hosts and services within the targeted infrastructure increases vulnerability to such attacks.
"CL-STA-0969's multi-pronged operational strategy, combining technical expertise with environmental adaptation, underscores the need for vigilant security measures and proactive threat intelligence."