PlayPraetor Android RAT Expands Rapidly Across Spanish and French-Speaking Regions
A new and highly sophisticated Android malware campaign, dubbed PlayPraetor, has been discovered by cybersecurity researchers at Cleafy. The malware has infected over 11,000 devices, primarily targeting Spanish and French-speaking users in Portugal, Spain, France, Morocco, Peru, and Hong Kong.
The rapid spread of the PlayPraetor Android RAT is a notable shift in strategy, as it previously focused on targeting English-speaking regions. The malware's operators have managed to evade detection by utilizing a Chinese-language C2 panel with a multi-tenant setup, allowing multiple affiliates to run campaigns simultaneously. This approach enables the threat actors to scale their operations and increase their reach.
The majority of victims are located in Europe, with 58% of infections reported in Portugal, Spain, and France. Moroccan users account for another significant portion, followed by Peruvian and Hong Kong-based devices. Two main operators dominate the botnet, focusing on Portuguese speakers, while smaller affiliates target Chinese, Spanish, and French users.
How PlayPraetor Spreads
The PlayPraetor Android RAT abuses Android Accessibility Services for real-time control of infected devices. This allows the operators to gain complete control over the compromised device, making it an ideal tool for financial fraud and other malicious activities.
A total of nearly 200 banking apps and cryptocurrency wallets have been targeted by the malware. The researchers found new commands in the overlay attack payloads, indicating that the malware is under active development and evolving rapidly.
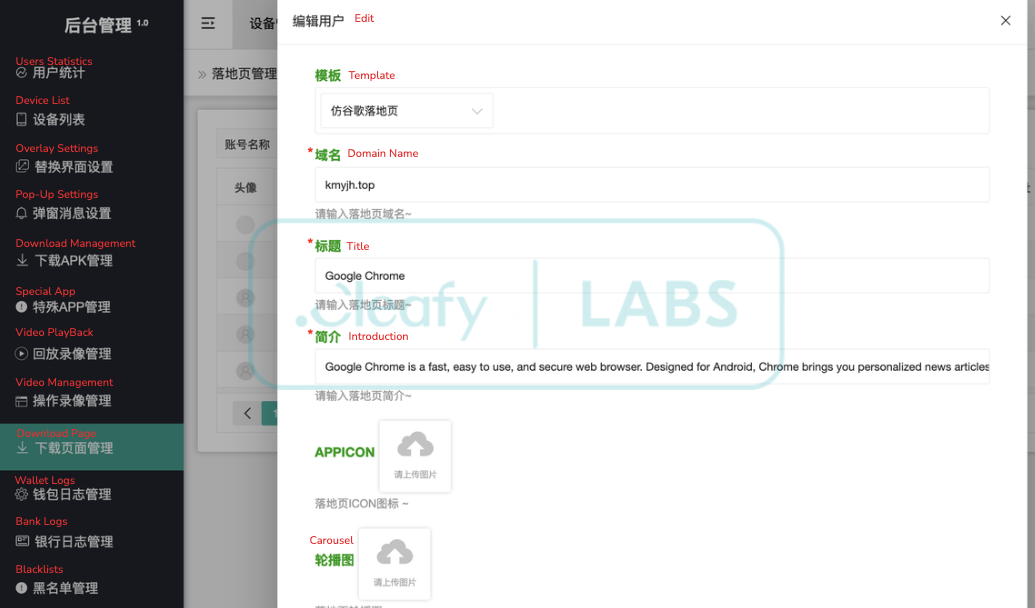
The PlayPraetor C2 Panel
The PlayPraetor C2 panel is a Chinese-language control hub that manages infected devices and runs phishing campaigns. The multi-tenant setup enables affiliates to operate independently while using shared infrastructure, making it a highly organized and professional threat operation.
Key features of the C2 panel include real-time device control, app launching, data exfiltration, and impersonation tools. Operators can create fake Google Play-like pages to deliver malware and use pre-registered domains for quick deployment of phishing pages. The modular design allows for swift adaptation to new threats, indicating a well-oiled machine behind the scenes.
Implications and Conclusion
The discovery of PlayPraetor represents another significant entry from Chinese-speaking threat actors into the global financial fraud landscape. The trend exemplified by recent campaigns such as ToxicPanda and Supercard X demonstrates an increasing interest in this region for developing and deploying sophisticated attack vectors against financial institutions worldwide.
"PlayPraetor represents another significant entry from Chinese-speaking threat actors into the global financial fraud landscape. This trend, exemplified by recent campaigns such as ToxicPanda and Supercard X, demonstrates an increasing interest from TAs in this region in developing and deploying sophisticated attack vectors against financial institutions worldwide."
While PlayPraetor shares similarities with other modern Android banking trojans, its innovative operational model sets it apart. By leveraging established techniques for on-device fraud through the abuse of Android's Accessibility Services, PlayPraetor has become a major global cyber threat.