# DDoS Peaks Hit New Highs: Cloudflare Mitigated Massive 7.3 Tbps Assault
The latest numbers from Cloudflare reveal that Distributed Denial of Service (DDoS) peaks have hit an all-time high, with the company mitigating a staggering 7.3 terabits per second (Tbps) and 4.8 billion packets per second (Bpps) in just two quarters of 2025.
Cloudflare blocked over 7 million DDoS attacks in Q2 2025, down from 20.5 million in the previous quarter. However, hyper-volumetric attacks surged with over 6,500 blocked, averaging an astonishing 71 daily.
The company's latest report reveals that Cloudflare has already surpassed its 2024 DDoS mitigation volume, with nearly 28 million attacks stopped so far in 2025. This marks a significant increase from the previous quarter and highlights the growing threat landscape.
"DDoS attacks continue to break records," reads the report published by Cloudflare. "During 2025 Q2, Cloudflare automatically blocked the largest ever reported DDoS attacks, peaking at 7.3 terabits per second (Tbps) and 4.8 billion packets per second (Bpps)."
Attacks exceeding 100 million packets per second (pps) surged 592% quarter-over-quarter, while those topping 1 billion pps or 1 Tbps doubled. HTTP DDoS attacks above 1 million requests per second (rps) remained steady at around 20 million total, or 220 kilobytes daily.
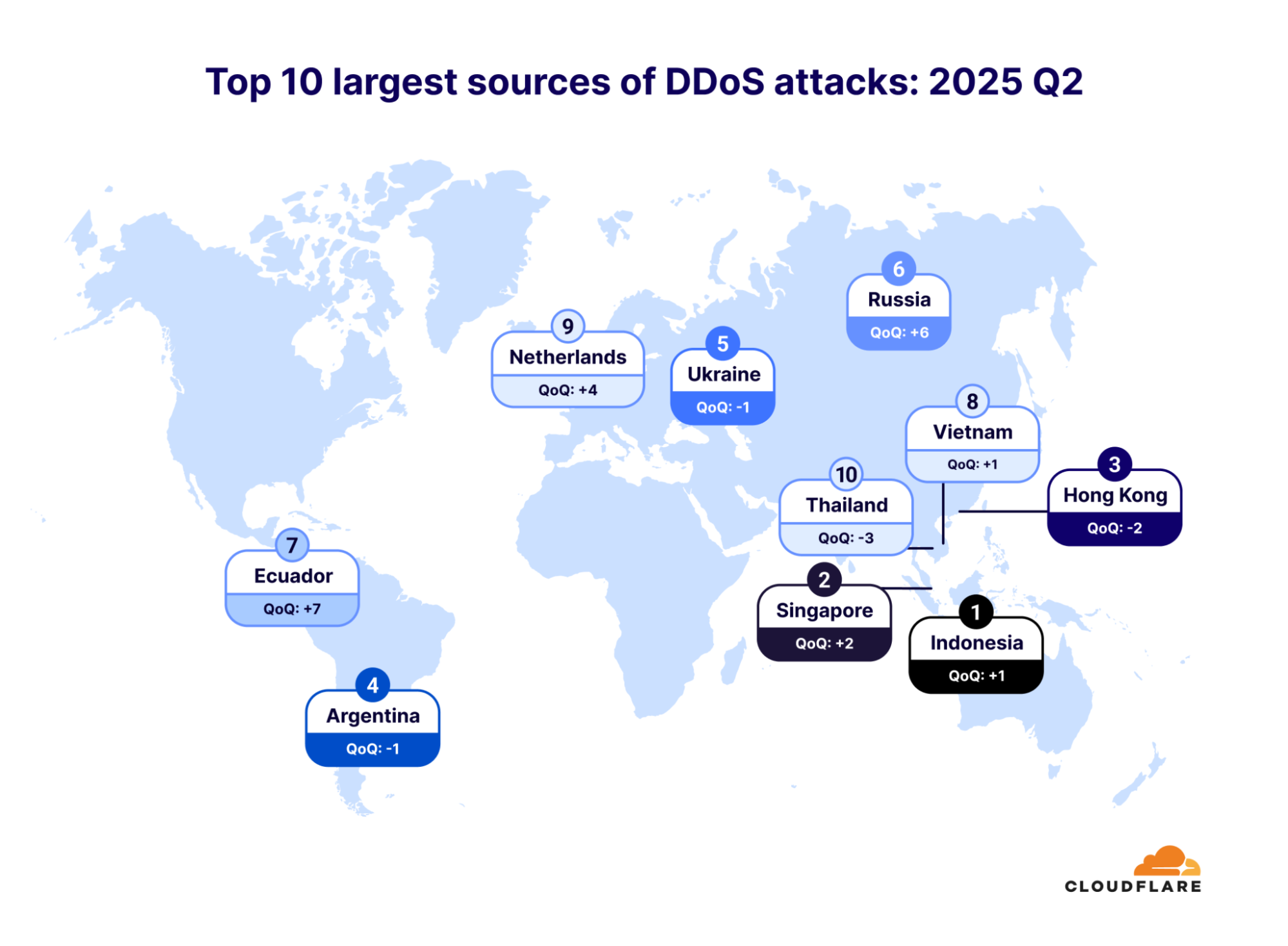
In Q2 2025, most of the attacks targeted Cloudflare customers in China, followed by Brazil and Germany. Russia and Vietnam saw major jumps in attack activity, climbing 40 and 15 spots, respectively. On the industry front, telecom, internet services, and IT were hit hardest, while agriculture surprisingly made it into the top 10 after a sharp rise, suggesting attackers are expanding their focus.
These rankings reflect where the affected customers are based, not necessarily where the attacks originated. In Q2 2025, Indonesia became the top source of DDoS attacks, followed by Singapore and Hong Kong. Russia and Ecuador also climbed the ranks.
Cloudflare is helping service providers fight back by offering a free threat intelligence feed that flags abusive IPs from their networks. Over 600 organizations are already using it to take down malicious botnet infrastructure.
In Q2 2025, attackers revived old DDoS methods targeting games, networks, and IoT devices. They flooded Teeworlds game servers with fake UDP packets, exploited outdated RIPv1 routing, abused misconfigured RDP servers, and infected Linux-based IoT devices with DemonBot malware to launch high-volume floods.
The researchers warned that VxWorks-based IoT devices also became attack sources. Cloudflare protects customers using Magic Transit, Spectrum, and intelligent filtering to block attacks while preserving legitimate traffic and service availability.
Most DDoS attacks in Q2 2025 stay small and brief, with 94% of L3/4 attacks under 500 Mbps and 85% under 50,000 packets per second. Modern servers can handle moderate traffic, but even small attacks can overwhelm unprotected systems during peak times.
While most attacks remain small, very large attacks are growing rapidly, with some exceeding 1 Tbps. Attackers use short, intense bursts to avoid detection and maximize disruption, highlighting the need for constant, real-time defense.
"Critical infrastructure continues to face sustained pressure, with the Telecommunications, Service Providers, and Carriers sector jumping again to the top as the most targeted industry," concludes the report.