Android Malware Konfety Evolves with ZIP Manipulation and Dynamic Loading
A new variant of the infamous Konfety Android malware has emerged, showcasing sophisticated tactics to evade detection by security tools. The Konfety malware, known for its ability to deliver malicious ads and install payloads without user knowledge, has evolved its methods once again.
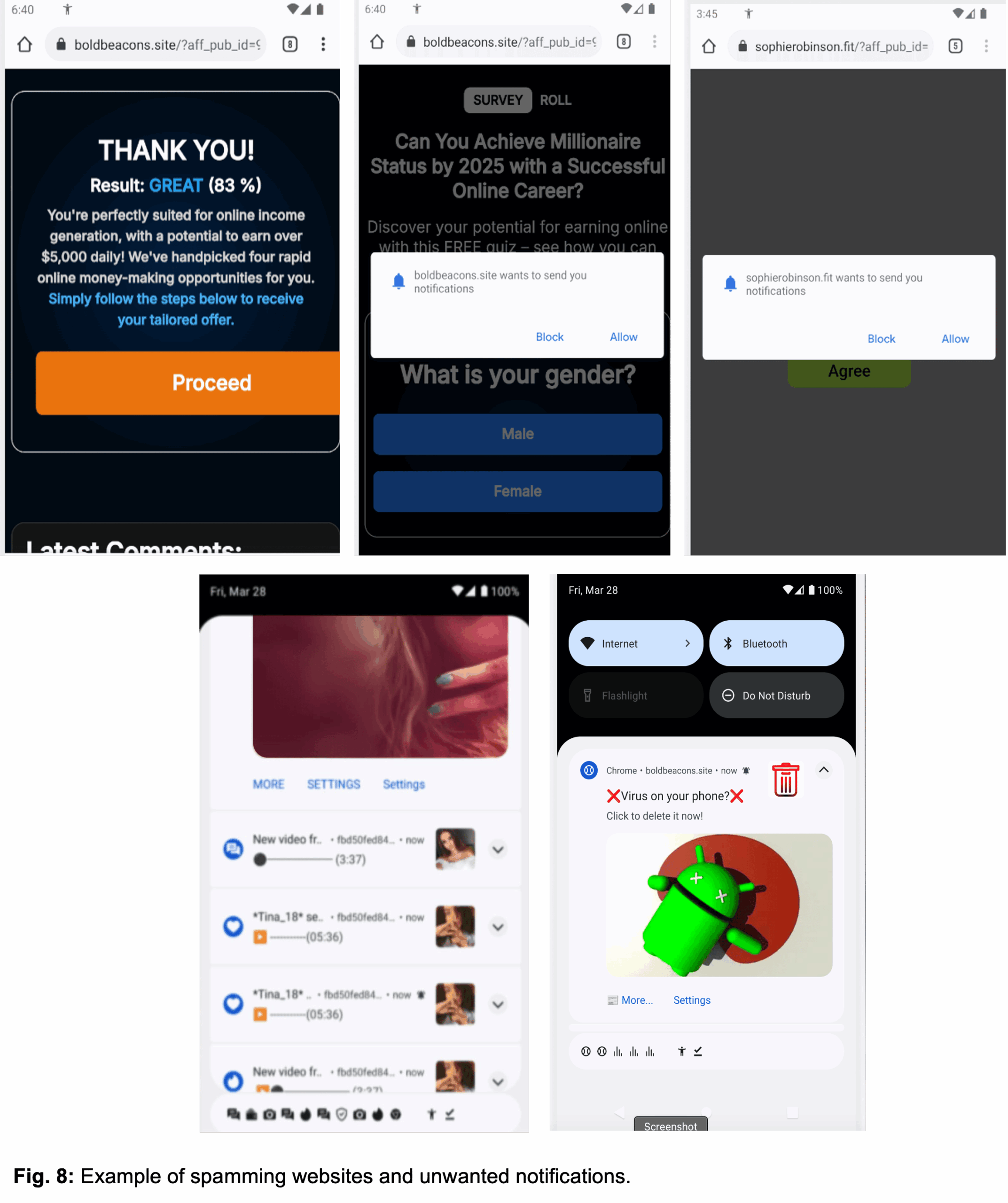
According to a recent report from Zimperium zLabs researchers, the new Konfety variant uses an "evil-twin" tactic and duplicate package names to avoid detection. This tactic involves creating fake apps with no real functionality, disguised as legitimate Google Play apps. The malware then tricks users into accepting a user agreement, which opens a browser to connect with a remote server.
Malformed ZIP Files: A New Layer of Evasion
The new Konfety variant uses malformed ZIP files to evade analysis tools. The report explains that the APK contains a misleading flag and declares an unsupported BZIP compression method, causing some tools to incorrectly identify the APK as encrypted and request a password for decompression.
"The AndroidManifest.xml of these samples declared the BZIP compression method," reads the report. "However, the file is not actually compressed using this algorithm. This discrepancy resulted in partial decompression for decompression tools and invalid file parsing for analysis tools."
Dynamic Loading: A New Level of Obfuscation
The latest Konfety malware variants use advanced obfuscation techniques to avoid detection. They load hidden, encrypted code at runtime, which makes the code not visible during standard scans.
"One of the key techniques employed is dynamic code loading," states the report. "Where additional executable code is loaded at runtime from an encrypted asset bundled within the APK." This encrypted file contains a secondary DEX (Dalvik Executable) file, which links back to Konfety's past use of the CaramelAds SDK for ad fraud.
Stealthy and Deceptive: How Konfety Works
Konfety disguises itself as a legitimate Google Play app but delivers none of its claimed features. The malware tricks users into accepting a user agreement, then opens a browser to connect with a remote server. This redirects through several sites, ultimately leading victims to install unauthorized apps or enable intrusive browser notifications.
Conclusion
The Konfety malware variant is a sophisticated example of how Android malware can evolve and adapt to evade detection. Its use of malformed ZIP files and dynamic loading techniques makes it difficult for security tools to analyze its code. As the report by Zimperium zLabs researchers highlights, this new variant poses significant threats to user privacy and security.
Stay ahead of the threat: follow us on Twitter (@securityaffairs), Facebook, and Mastodon for the latest security news and updates.