North Korea-linked Actors Spread XORIndex Malware via 67 Malicious npm Packages
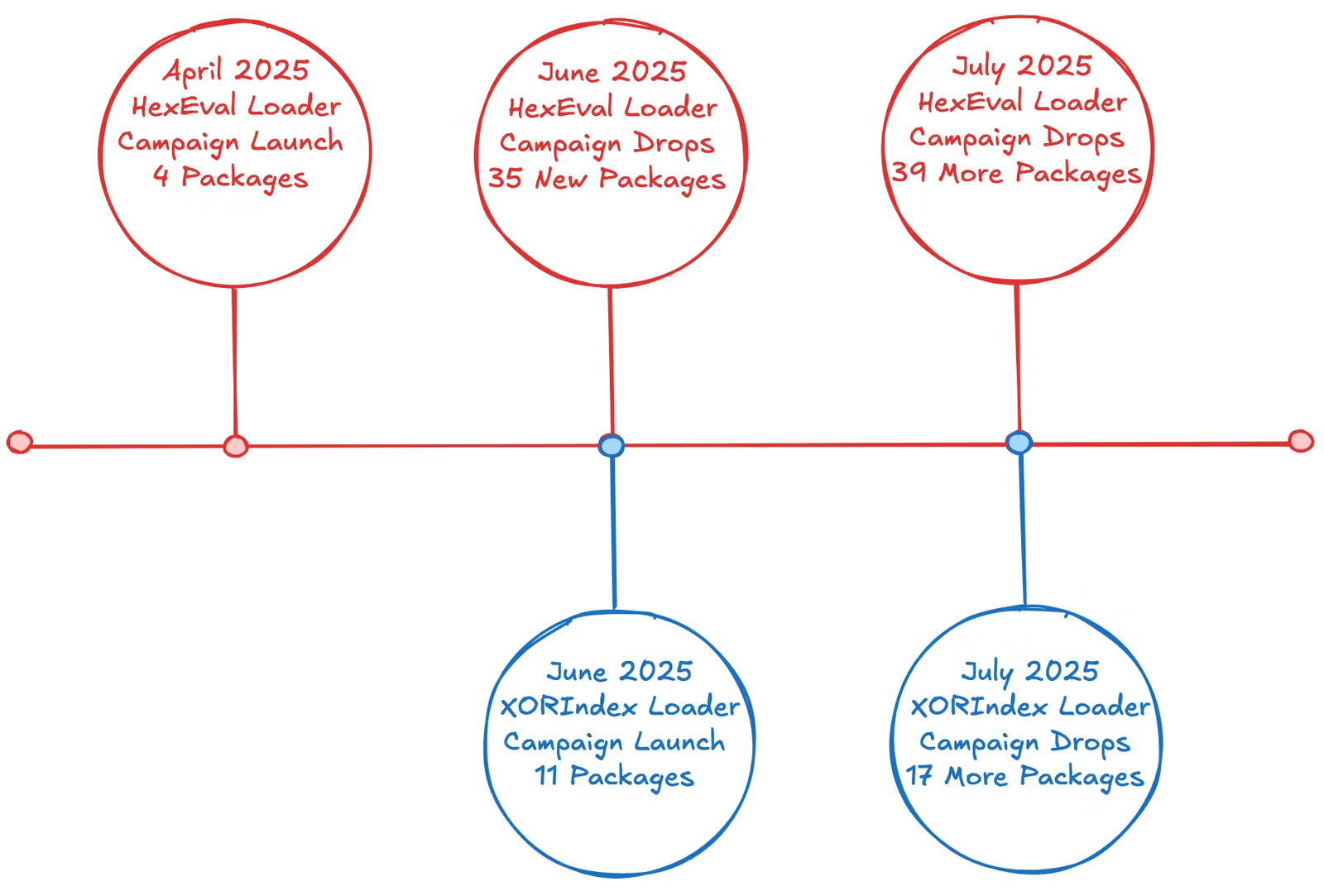
Recent revelations have exposed a sophisticated supply chain attack by North Korea-linked actors, who have infiltrated the Node.js package manager npm with 67 malicious packages containing the XORIndex malware loader. This malicious software has already garnered over 17,000 downloads, further highlighting the ongoing threat landscape.
The Contagious Interview Campaign
The attack is attributed to North Korea-linked threat actors behind the Contagious Interview campaign, which has been active since June 2025. The HexEval Loader campaign, also linked to this group, has shown no signs of slowing down, with over 8,000 downloads. Despite takedown efforts, 27 packages remain live, indicating the persistence of these nation-state actors.
XORIndex Malware Loader
The XORIndex malware loader is a new variant that was previously unreported by cybersecurity firms. It uses advanced techniques like string obfuscation, multi-endpoint C2 rotation, and host profiling to evade detection. These malicious packages allow attackers to collect system data and deliver the BeaverTail malware, which targets crypto wallets and browser extensions.
The InvisibleFerret Backdoor
The second-stage malware delivered by the XORIndex Loader is the BeaverTail backdoor, a hallmark payload of the North Korean Contagious Interview operations. This malware scans for dozens of known desktop wallet directories and browser extension paths, archives the collected data, and exfiltrates it to a hardcoded IP-based HTTP endpoint.
Evasive Methods and Supply Chain Defense
The attackers persist by using legitimate services like Vercel, making supply chain defenses critical for developers and organizations. The report concludes that defenders should expect continued iterations of these loaders across newly published packages, often with slight variations to evade detection. Evasive methods such as memory-only execution and obfuscation will likely increase, complicating detection and incident response.
Conclusion
The XORIndex Loader campaign by North Korean threat actors highlights the ongoing evolution of nation-state attacks on software supply chains. As developers and organizations face growing pressure to maintain security, it is essential to stay vigilant and implement robust defenses against these types of threats.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon for more updates on cybersecurity and threat intelligence.