Interlock Ransomware Group Deploys New PHP-Based RAT via FileFix
The Interlock ransomware group has launched a new campaign deploying a PHP-based variant of the Interlock Remote Access Trojan (RAT) via the FileFix delivery method. According to researchers from the DFIR Report, in partnership with Proofpoint, this latest development marks a significant shift in the group's tactics, as it leverages PHP, a common web scripting language, to gain and maintain access to victim networks.
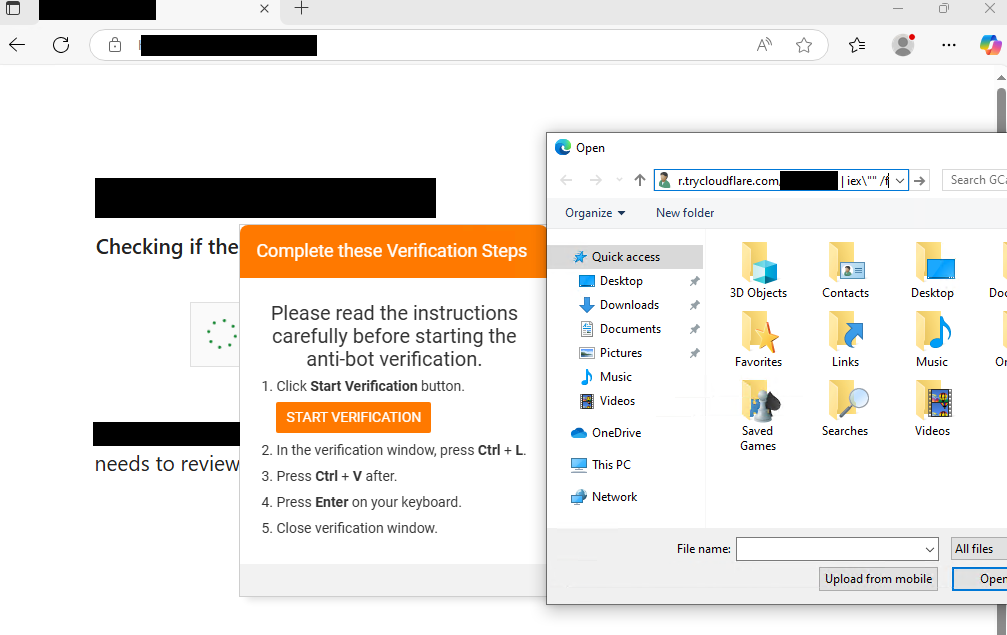
Since May 2025, the Interlock RAT has been linked to the KongTuke (LandUpdate808) threat cluster. The new PHP-based variant is a notable departure from the earlier JavaScript-based Node.js version. According to the DFIR report, this campaign uses a delivery method known as FileFix, an evolution of ClickFix, which exploits Windows File Explorer's address bar to trick users into executing commands.
Here's how it works: compromised websites are injected with a single-line script hidden in the page's HTML. The linked JavaScript employs heavy IP filtering to serve the payload, prompting victims through fake CAPTCHA checks to run a PowerShell script. Once executed, the script will ask the user to paste some text from the clipboard into the run command. If the text is pasted correctly, it will execute a PowerShell script that eventually leads to the Interlock RAT.
The PHP version of the malware executes through PowerShell, launching a PHP binary from an unusual path and using a custom config file. This new variant marks a significant improvement in terms of operational sophistication for the Interlock group.
The Interlock RAT: A Malicious Powerhouse
Once installed on a victim's system, the Interlock RAT performs extensive system reconnaissance, checking its privilege level (USER, ADMIN, or SYSTEM) and exfiltrating system info in JSON format. The malware also connects to a remote server to download and execute EXE or DLL files.
The Interlock RAT conducts automated system profiling using various PowerShell commands, collecting detailed information about the system, processes, services, drives, and network. It also performs hands-on-keyboard discovery, such as querying Active Directory, user accounts, and domain controllers, showcasing signs of attacker interaction.
Establishing a Robust Command and Control Channel
The Interlock RAT establishes a robust command and control (C2) channel with the attackers' infrastructure. Notably, it leverages trycloudflare.com URLs to abuse the legitimate Cloudflare Tunnel service and mask the true location of the C2 server.
Furthermore, the malware contains hardcoded fallback IP addresses, ensuring communication can be maintained even if the Cloudflare Tunnel is disrupted. This demonstrates the Interlock group's commitment to maintaining a reliable command and control channel, even in the face of disruptions.
A New Dimension for Lateral Movement
The Interlock RAT also supports lateral movement via RDP (Remote Desktop Protocol), allowing attackers to traverse networks with ease. This new capability highlights the continued evolution of the Interlock group's tooling and operational sophistication.
This discovery marks a significant milestone in our understanding of the Interlock ransomware group's tactics, operations, and techniques. The fact that this variant leverages PHP underscores the commonality of web scripting languages used to gain access to victim networks.
Stay Ahead of the Threat
In light of this new development, it is essential for organizations to take proactive measures to protect themselves against the Interlock RAT. This includes implementing robust security controls, conducting regular vulnerability assessments, and ensuring timely software updates.
By staying informed about emerging threats like the Interlock RAT, you can better equip yourself to defend against the ever-evolving landscape of cyber threats.