McDonald's Job App Exposes Data of 64 Million Applicants
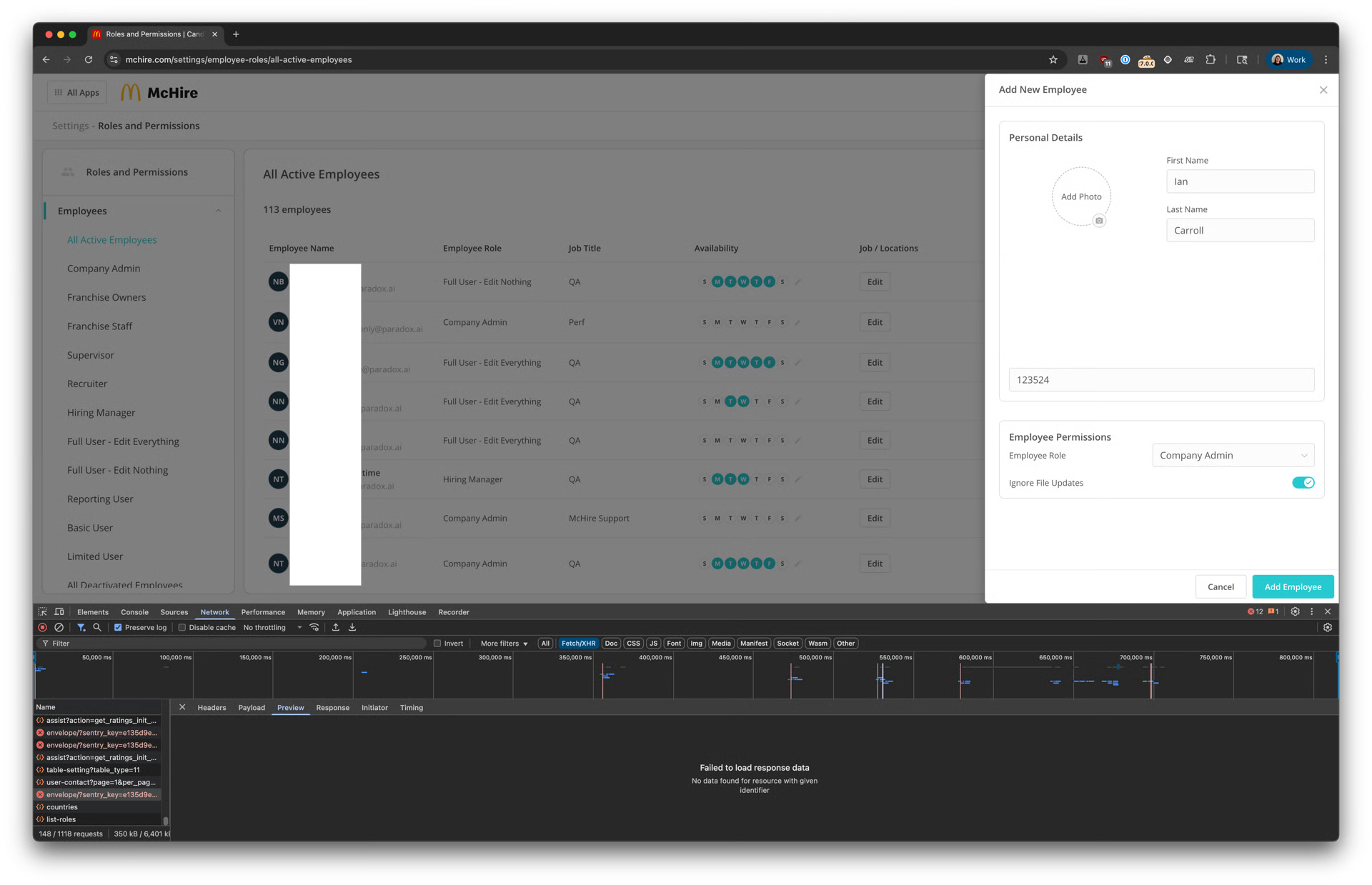
McDonald's job app, McHire, has been left vulnerable to cyber attacks, exposing the sensitive information of over 64 million job applicants. Security researchers Ian Carroll and Sam Curry discovered multiple vulnerabilities in the chatbot recruitment platform built by Paradox.ai, which has raised serious concerns about the security of the application.
The security duo found that the hiring bot had major flaws, including a test account with default credentials "123456" for both username and password. This allowed them to access private chats between job seekers and the bot, as well as gain admin access to a test restaurant, where they saw internal staff data and ongoing interviews.
The bug exposed sensitive information from millions of applicants due to poor security setup. Researchers found that the McHire administration interface for restaurant owners accepted the default credentials, while an insecure direct object reference (IDOR) on an internal API allowed them to access any contacts and chats they wanted. This meant that anyone with a McHire account and access to any inbox could retrieve the personal data of over 64 million applicants.
The Discovery
Researchers tested McDonald's McHire job app by applying for a job, interacting with its chatbot "Olivia," and taking a personality test powered by Traitify. The process stalled pending human review, but curious researchers explored the login page for McHire admins and found a "Paradox team members" option.
Using the default credentials "123456" / "123456," they unexpectedly gained admin access to a test restaurant account. This revealed how the system worked and exposed internal employee data from Paradox.ai, although they had not yet proven deeper data security risks at that point.
The Vulnerabilities
Researchers found multiple vulnerabilities in the McHire chatbot recruitment platform, including:
- A test account with default credentials "123456" / "123456" that accepted login attempts
- An insecure direct object reference (IDOR) on an internal API that allowed access to any contacts and chats
- A hidden API that let them access chat data, including names, emails, phone numbers, and job details from real McDonald's applicants
- Access to auth tokens to impersonate applicants
The researchers quickly alerted Paradox.ai, which quickly fixed the issue and announced security enhancements. However, this incident highlights the importance of robust security measures in place for sensitive data and the need for regular vulnerability testing.
Causes and Consequences
According to the report published by the experts, multiple causes can contribute to such an attack:
- Insufficient security setup
- Default credentials being too easy to guess
- Lack of regular vulnerability testing
- Weak password policies
- Dangerous use of APIs
The consequences of such an attack can be severe, including identity theft, financial loss, and reputational damage. As a result, it is essential for organizations to take the necessary steps to protect sensitive data and implement robust security measures.
Call to Action
McDonald's has taken swift action to address the vulnerabilities in their McHire job app, but this incident serves as a reminder of the importance of maintaining robust security measures. Organizations must prioritize data protection and vulnerability testing to prevent similar incidents from occurring in the future.