PerfektBlue Bluetooth Attack Allows Hacking into Infotainment Systems of Mercedes, Volkswagen, and Skoda
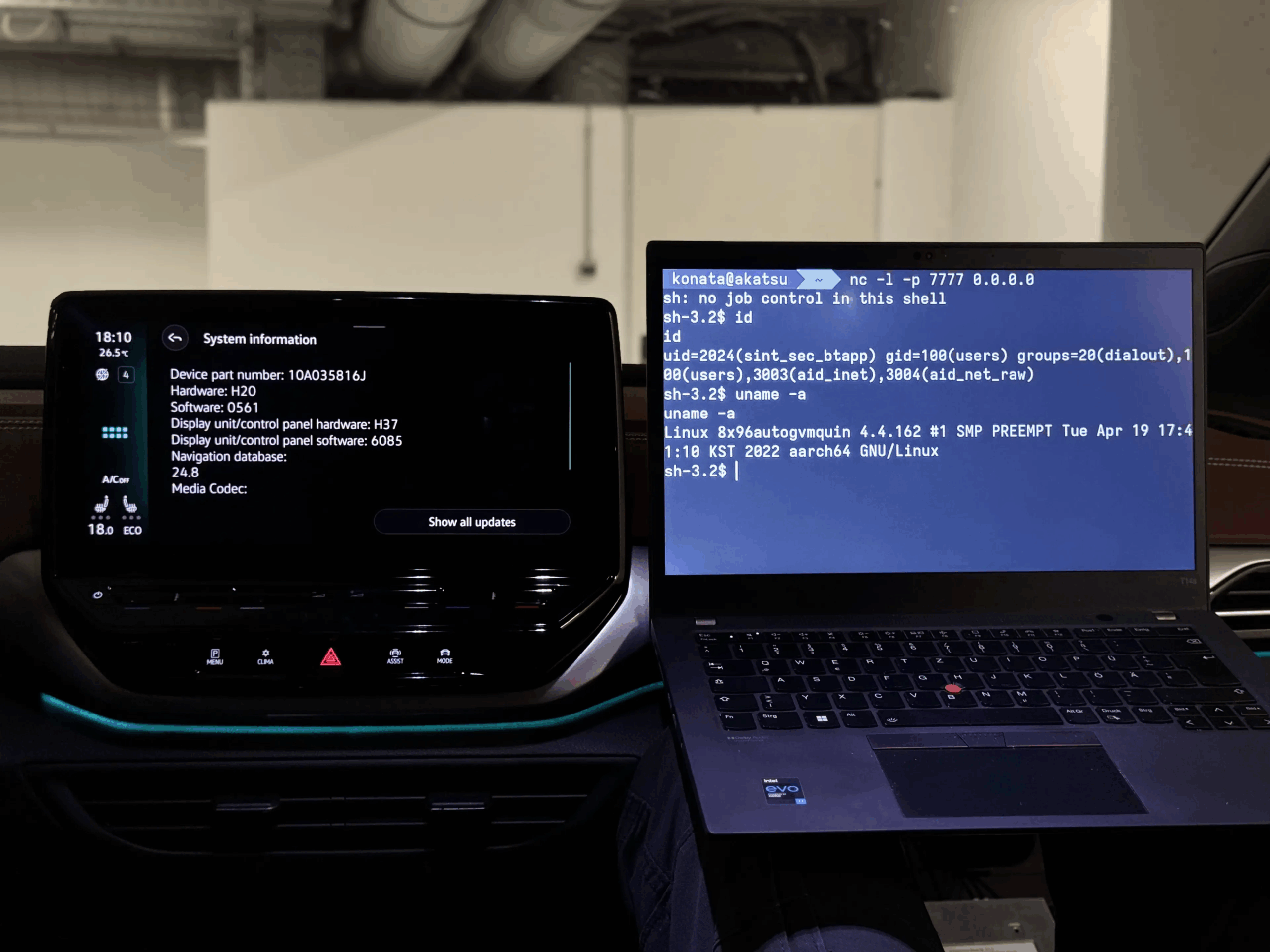
A recent discovery by researchers at PCA Cyber Security has highlighted a critical vulnerability in the OpenSynergy BlueSDK Bluetooth stack, which could allow hackers to remotely exploit millions of vehicles' infotainment systems. The flaw, collectively tracked as PerfektBlue, enables attackers to execute remote code on vehicles, potentially leading to location tracking, audio recording, and access to sensitive data.
The PerfektBlue attack chain exploits vulnerabilities in the BlueSDK Bluetooth framework, which is widely used in the automotive industry. This framework allows vendors like Mercedes-Benz, Volkswagen, and Skoda to customize their systems, making it more challenging to secure. The researchers found that pairing with a target device is the only requirement for the attack, but this can be implementation-specific due to the framework's flexibility.
"Essentially, PerfektBlue requires at most 1-click from a user to be exploited over-the-air by an attacker," reads the advisory published by the researchers. "This means that even with security measures in place, hackers could potentially gain access to critical functions like steering and wipers."
The Impact on the Automotive Industry
The PerfektBlue attack has significant implications for the automotive industry, as millions of vehicles are affected. The researchers demonstrated the attack against Mercedes-Benz NTG6 head unit, Volkswagen MEB ICAS3 head unit, and Skoda MIB3 head unit. The discovery highlights the need for manufacturers to prioritize security in their systems.
The vulnerabilities discovered by the researchers include multiple issues with low-to-critical severity, allowing an attacker to obtain 1-click Remote Code Execution (RCE) in the operating system of a device which utilizes BlueSDK Bluetooth stack. This level of access enables hackers to manipulate the system, escalate privileges and perform lateral movement to other components of the target product.
The Response from OpenSynergy
OpenSynergy, the company behind the BlueSDK framework, was informed of the vulnerabilities by PCA Cyber Security on May 17, 2024. They confirmed the issues and started working on patches in July 2024. The patches were completed in September 2024.
The Responsible Disclosure Process
PCA Cyber Security initiated responsible disclosure by sharing the content of the PerfektBlue advisory website with OpenSynergy, allowing them time to review the findings. By early June, PCA had confirmed that the vulnerabilities affected several vehicle models from an undisclosed original equipment manufacturer (OEM), whose security team was promptly notified.
However, the OEM reported that they had not received any official notification or patch regarding the vulnerabilities through their supply chain. In response, PCA decided to move forward with publication while choosing not to reveal the OEM's identity publicly. The advisory was finally released on July 7th, with the primary goal of raising awareness among OEMs, suppliers, and end users, encouraging faster remediation and enhanced security across the affected ecosystem.
Conclusion
The PerfektBlue Bluetooth attack highlights the need for manufacturers to prioritize security in their systems. The discovery emphasizes the importance of responsible disclosure and collaboration between researchers, companies, and government agencies to ensure that vulnerable systems are patched promptly and effectively. By sharing this information, we can work together to prevent similar attacks in the future.