DoNot APT is Expanding Scope Targeting European Foreign Ministries
A sophisticated cyber espionage group, DoNot APT, likely linked to India, has expanded its operations and is targeting European foreign ministries with a new malware, called LoptikMod. This latest campaign, analyzed by cybersecurity firm Trellix, highlights the group's ongoing efforts to gather sensitive information through stealthy and sophisticated means.
The DoNot Team (also known as APT-C-35 and Origami Elephant) has been active since 2016, focusing on government entities, foreign ministries, defense organizations, and NGOs in South Asia and Europe. Over the years, this group has demonstrated a consistent track record of using custom Windows malware via phishing for espionage, enabling long-term access and data theft.
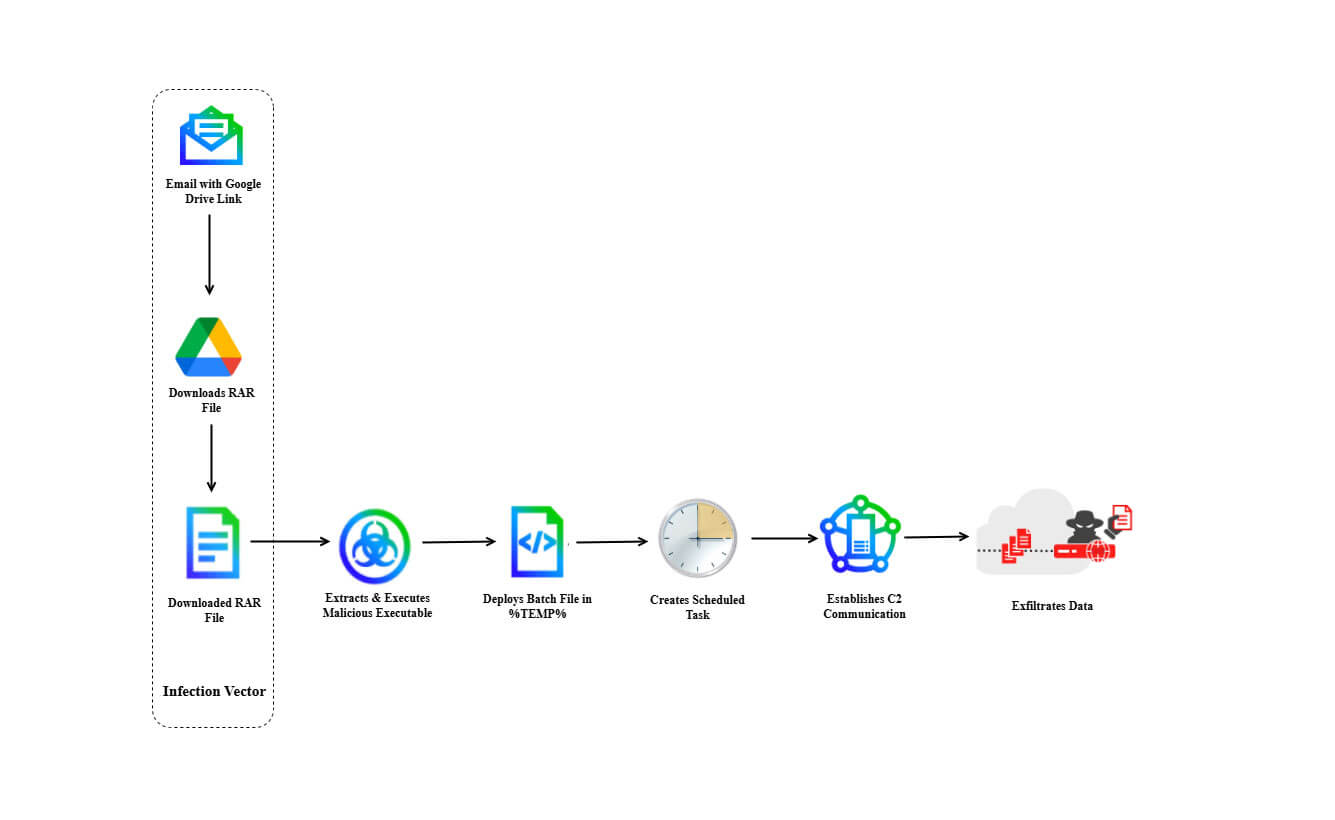
In the recent campaign, DoNot APT used LoptikMod malware to steal sensitive data from infected systems. The attackers employed a spear-phishing email impersonating defense officials to target a European diplomatic entity, delivering the malware via a password-protected RAR file. The phishing email was designed to appear legitimate, complete with proper special characters and an HTML structure that mimicked real-world diplomatic correspondence.
The archive contained a disguised executable (notflog.exe) with a PDF icon, which tricked users into running the malware. Once opened, the disguised executable established persistence using a scheduled task and connected to a C2 server to send system information, receive commands, download additional payloads. The malware used binary string obfuscation and techniques linked to DoNot APT, making it difficult for security researchers to analyze.
The campaign reflects the group's ongoing efforts to gather sensitive information through sophisticated infection chains and deception tactics. According to Trellix's report, the email was designed to appear legitimate diplomatic correspondence that would reasonably contain document attachments or links.
Malware Analysis
The LoptikMod malware uses selective obfuscation by packing only critical code sections, hindering static analysis. It minimizes listed imports and loads APIs like LoadLibrary and GetProcAddress at runtime to evade detection. Once executed, it creates a mutex to prevent multiple instances, drops a batch file for persistence via scheduled tasks.
The malicious code uses anti-VM checks and gathers system info, encrypts it with AES, and communicates with a C2 server over HTTPS, possibly downloading and executing a second-stage payload ('socker.dll') via further scheduled tasks. However, the C2 server was inactive during analysis, preventing full observation of the malware's behavior.
Implications and Recommendations
The recent targeting of a European foreign affairs ministry highlights DoNot APT's expanding scope and persistent interest in gathering sensitive information. This underscores the need for heightened vigilance and robust cybersecurity measures to protect against such threats.
"The email leveraged diplomatic themes related to defense attaché coordination between Italy and Bangladesh," reads Trellix's report. "While the exact body content was not gathered in the findings, the subject line 'Italian Defence Attaché Visit to Dhaka, Bangladesh' suggests a lure designed to appear as legitimate diplomatic correspondence that would reasonably contain document attachments or links."
The incident highlights the importance of employee education and awareness programs in preventing phishing attacks. It also emphasizes the need for organizations to maintain up-to-date security software, regular backups, and robust incident response plans to mitigate the impact of such threats.