Hackers Weaponize Shellter Red Teaming Tool to Spread Infostealers
Threat actors have been exploiting the legitimate red teaming tool, Shellter, to spread stealer malware after a licensed copy was leaked. Elastic Security Labs has identified several malware campaigns using the commercial AV/EDR evasion tool SHELLTER.
A Legitimate Tool Turned Malicious
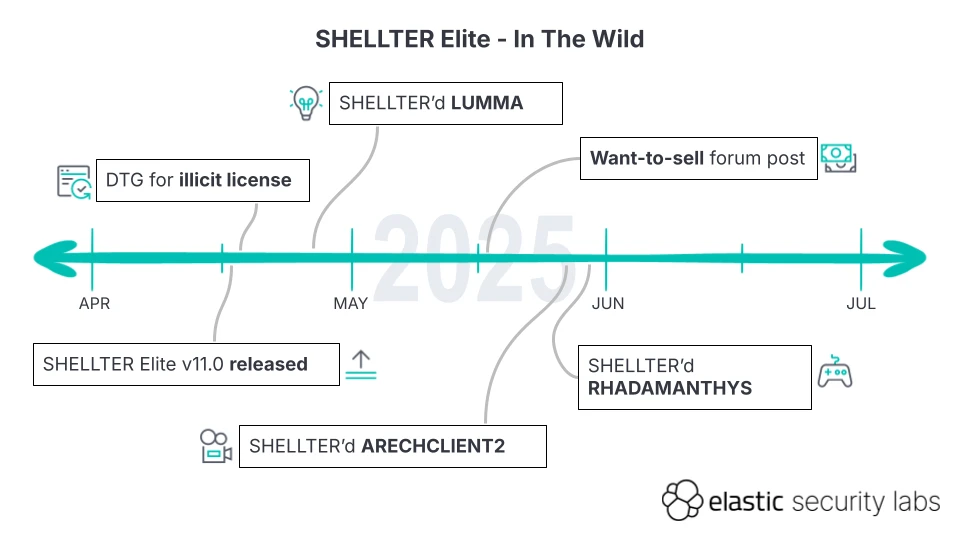
The tool was originally built for legitimate red team operations, but it has now been adopted by threat actors to bypass security measures and deploy malware. Shellter Elite version 11.0, which was released on April 16, 2025, is the latest version being used in infostealer attacks.
A Breach in Vendor Security
A company that bought Shellter Elite licenses leaked their copy of the software, leading to malicious actors exploiting the tool for harmful purposes. The vendor has identified the issue and addressed it. However, this breach highlights the need for better security measures in place.
Shellter's Response
The creators of Shellter criticized Elastic Security Labs for their "reckless and unprofessional" disclosure. They claimed that the lab was aware of the malicious abuse of Shellter Elite for months but chose not to notify them, opting instead for a surprise exposé to gain publicity.
Elastic Security Labs' Response
Shellter's team emphasized their commitment to vetting customers and cooperating with authorities. They also called for better communication between red and blue team communities in the cybersecurity industry.
Malware Campaigns Using Shellter
Threat actors have been using Shellter to evade detection across various operations. A campaign spreading the LUMMA stealer began using Shellter in late April, while others used it in phishing campaigns targeting YouTubers with fake sponsorship offers.
A Dynamic Unpacker Released
Elastic Security Labs has released a dynamic unpacker to analyze and detect SHELLTER-protected binaries more effectively. This tool uses static and dynamic analysis techniques to extract payloads from binaries protected by SHELLTER.
Risks Associated with the Tool
The unpacker should only be executed within an isolated virtual machine due to potential risks of malicious executable code being mapped into memory.
The Future of Shellter
Given that cracked versions of Cobalt Strike and Brute Ratel C4 have already ended up in the hands of cybercriminals, it's not far-fetched to expect Shellter might follow a similar path. The commercial OST community must now contend with real threats wielding more capable tools.
Conclusion
The exploitation of Shellter by threat actors highlights the importance of security measures and vetting processes in place. It also underscores the need for better communication between red and blue team communities in the cybersecurity industry.