**Elastic Detects Stealthy NANOREMOTE Malware Using Google Drive as C2**
A new Windows backdoor, named NANOREMOTE, has been discovered by Elastic Security Labs researchers. This malware uses the Google Drive API for command and control (C2) communications, making it difficult to detect.
NANOREMOTE shares code with FINALDRAFT/REF7707, a similar implant that utilizes the Microsoft Graph API. The report published by Elastic highlights the unique features of NANOREMOTE, including its use of the Google Drive API for data theft and payload staging.
How NANOREMOTE Works
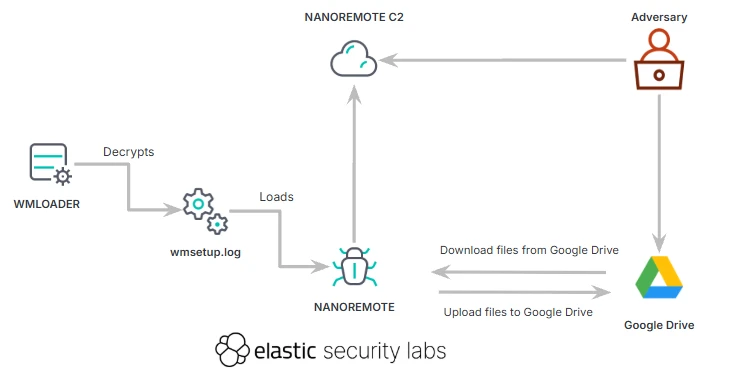
The malware is delivered through WMLOADER, a loader disguised as a Bitdefender executable with an invalid signature. This loader prepares the process for shellcode execution using VirtualAlloc/VirtualProtect. The shellcode searches for wmsetup.log and decrypts it with AES-CBC using a fixed key, loading the NANOREMOTE backdoor into memory.
NANOREMOTE is a 64-bit backdoor written in C++ that runs commands, moves files, and uses the Google Drive API via pipe-separated configs or the NR_GOOGLE_ACCOUNTS environment variable. The malware communicates over HTTP with a hard-coded, non-routable IP, receiving operator commands and returning the corresponding results.
Command Handlers and Features
NANOREMOTE supports 22 command handlers, enabling full control over an infected Windows system. These handlers allow attackers to gather system info, modify beacon timing, terminate the implant, and manage files and directories (list, move, delete, create). The backdoor can execute commands, load PE files from disk or directly from memory, and change or retrieve the working directory.
The malware also includes advanced file-transfer capabilities using the Google Drive API, with queued download/upload tasks that can be paused, resumed, or canceled. These transfers blend into normal encrypted cloud traffic, complicating detection.
Security Implications
The discovery of NANOREMOTE highlights the ongoing threat posed by sophisticated malware actors. The use of custom PE loaders and task queues to manage ongoing operations makes it challenging for security teams to detect and respond to this type of malware.
Elastic's report concludes that the threat group behind these implants is likely using a shared codebase and development environment, as evidenced by the similarities between FINALDRAFT and NANOREMOTE. This finding underscores the importance of staying vigilant in detecting and mitigating threats from advanced actors.
Conclusion
The discovery of NANOREMOTE demonstrates the evolving nature of cyber threats and the need for continuous monitoring and detection capabilities. As threat actors continue to innovate and adapt, security teams must remain proactive in their defense strategies to stay ahead of these emerging threats.
Follow me on Twitter: @securityaffairs and Facebook and Mastodon