Two Flaws in vBulletin Forum Software are Under Attack
A recent discovery by security experts has revealed two critical vulnerabilities in the popular vBulletin forum software, leaving users and administrators vulnerable to API abuse and remote code execution. The flaws, tracked as CVE-2025-48827 and CVE-2025-48828, were identified by researcher Egidio Romano on May 23, 2025, and have already been exploited in the wild.
The First Flaw: API Abuse
CVE-2025-48827 (CVSS score of 10) is a particularly egregious flaw that allows an unauthenticated user to invoke protected API controllers' methods when running on PHP 8.1 or later, as demonstrated by the /api.php?method=protectedMethod pattern. This means that an attacker can potentially bypass security restrictions and execute arbitrary code without requiring authentication.
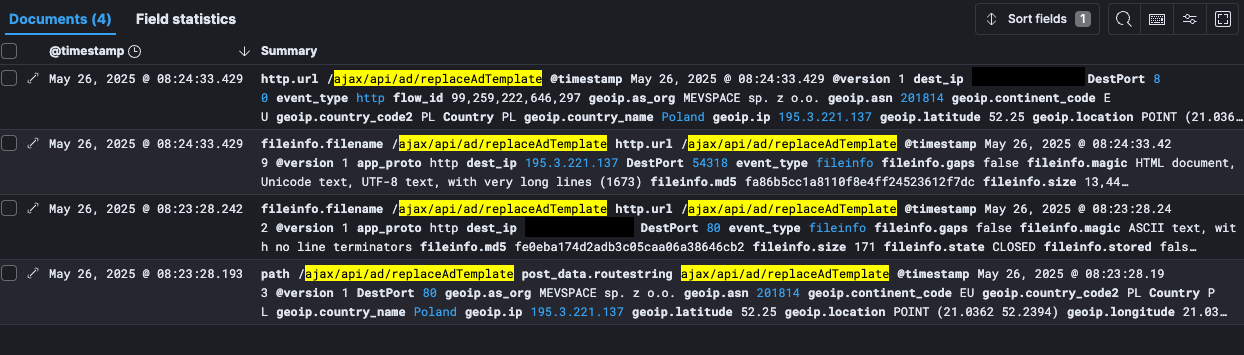
Security researcher Ryan Dewhurst has confirmed that this vulnerability is being actively exploited in the wild, with exploit attempts recorded on his honeypot targeting the vulnerable replaceAdTemplate API endpoint, giving attackers potential server access.
The Second Flaw: Template Conditionals
The second flaw, tracked as CVE-2025-48828 (CVSS score of 9), enables attackers to run arbitrary PHP code by abusing template conditionals. This allows an attacker to inject malicious code into the vBulletin platform, potentially leading to remote, unauthenticated code execution.
Vulnerable Versions and Remediation
The vulnerabilities affect vBulletin versions from 5.0.0 to 5.7.5 and from 6.0.0 to 6.0.3, specifically when the platform is running on PHP 8.1 or newer. Security experts urge administrators to review their frameworks and custom APIs, ensuring that access restrictions are enforced robustly.
Expert Analysis
"For defenders and developers: now is a good time to review your frameworks and custom APIs," reads the analysis published by Romano. "If you're dynamically routing controller methods through Reflection, audit whether you're enforcing access restrictions robustly. Look at how your application behaves across different PHP versions, and always assume that method visibility alone is not a security boundary."
"For researchers: this vulnerability class might be ripe for further exploration," adds Romano. "My quick survey of popular PHP platforms suggests that while vBulletin is the most egregious case, others may have similar patterns waiting to be exploited. Custom CMS platforms, internal admin panels, legacy enterprise code — all of these are candidates."
Timeline
Here is a timeline of the vulnerability:
* May 23, 2025: Security researcher Egidio Romano discovers the two vBulletin vulnerabilities. * May 24, 2025: A Nuclei template for the vulnerability is released. * May 26, 2025: Exploit attempts are seen in the wild targeting the vulnerable replaceAdTemplate API endpoint.
Follow this reporter on Twitter (@securityaffairs), Facebook, and Mastodon for the latest security news and updates.