China-linked APT41 Used Google Calendar as C2 to Control Its TOUGHPROGRESS Malware
In a shocking revelation, Google has revealed that China-linked Advanced Persistent Threat (APT) group APT41 used the popular calendar service Google Calendar as a command and control (C2) channel to control its malicious software, TOUGHPROGRESS. This unprecedented use of cloud services by threat actors highlights the growing importance of protecting these platforms from malicious activity.
According to a recent report published by Google, APT41 exploited a government website hosting malware, dubbed "TOUGHPROGRESS", which was designed to target multiple government entities. The malware took advantage of Google Calendar for C2 communication, demonstrating the group's creativity in using legitimate services to evade detection.
"Misuse of cloud services for C2 is a technique that many threat actors leverage in order to blend in with legitimate activity," reads the report. This tactic allows attackers to mask their malicious activities as innocent, making it harder for security tools and analysts to detect their presence.
The TOUGHPROGRESS Malware: A Stealthy Threat
TOUGHPROGRESS is a highly sophisticated malware that operates in three stealthy stages. The first stage, PLUSDROP, decrypts and runs the next stage entirely in memory, evading detection by traditional antivirus software. The second stage, PLUSINJECT, uses process hollowing to inject malicious code into legitimate Windows processes, further complicating analysis.
The final stage, TOUGHPROGRESS, carries out the attacker's tasks on the infected system, communicating with its operators through Google Calendar to avoid detection. This communication channel is encrypted using XOR keys and compressed using LZNT1, making it challenging for analysts to intercept and understand the malware's activities.
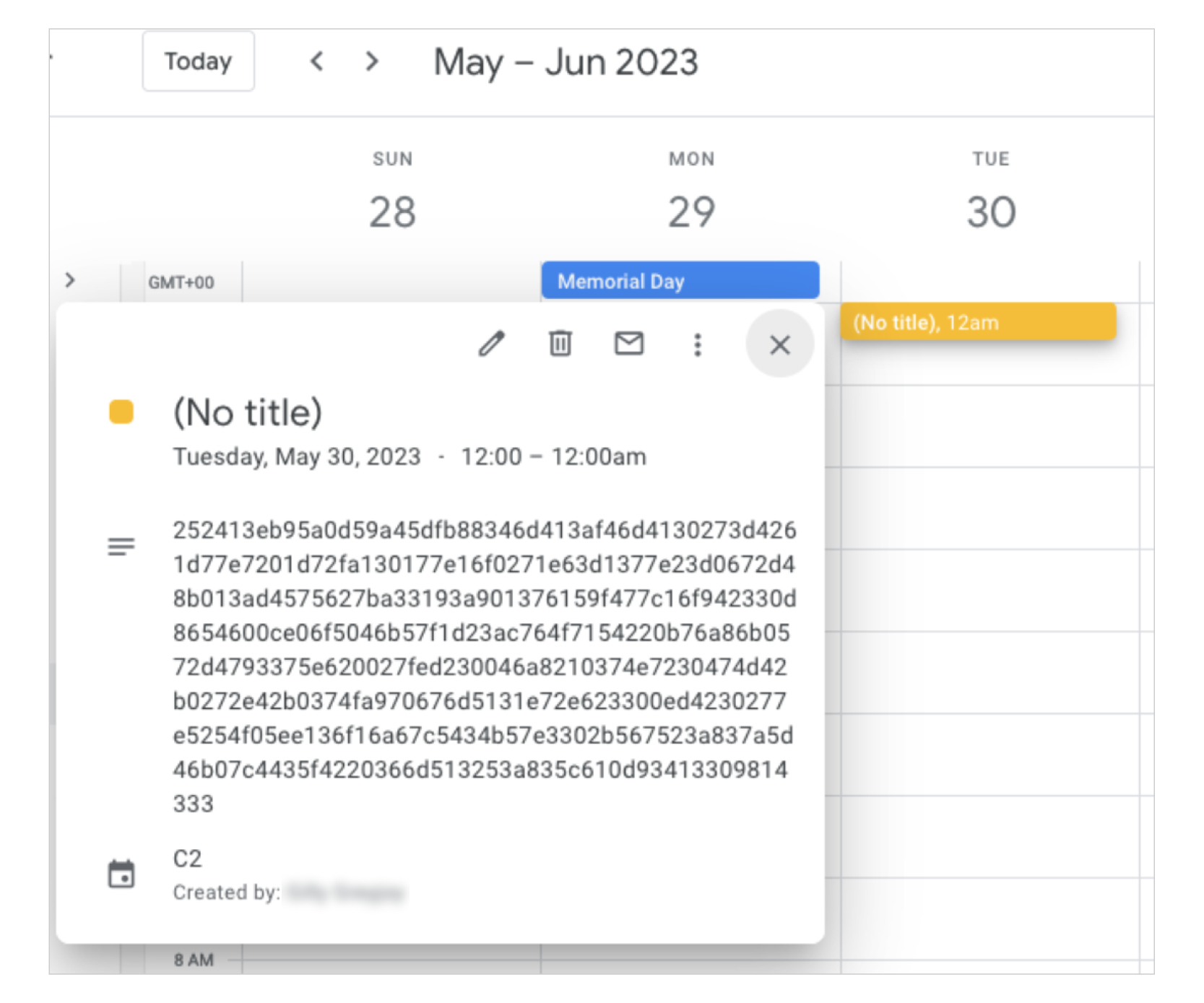
How TOUGHPROGRESS Uses Google Calendar
TOUGHPROGRESS creates hidden events on specific hardcoded dates to exfiltrate stolen data and receive commands. The malware encrypts both data and commands using XOR keys and compresses messages with LZNT1. Commands are placed in Calendar event descriptions, retrieved and decrypted by the malware, then executed on the infected system.
Results are encrypted and uploaded back as new calendar events, effectively turning Google Calendar into a covert communication tool. This technique allows APT41 to maintain a low profile while still maintaining control over its infected systems.
Google Takes Action Against APT41
Google has taken steps to disrupt APT41 and TOUGHPROGRESS malware, including developing custom fingerprints to identify and take down attacker-controlled Calendars. The company has also terminated attacker-controlled Workspace projects, effectively dismantling the infrastructure that APT41 relied on for this campaign.
"We have updated file detections and added malicious domains and URLs to the Google Safe Browsing blocklist," continues the report. "Additionally, we have alerted affected organizations, sharing TOUGHPROGRESS network logs and threat intel to support detection and response efforts."
Stay Vigilant: Protecting Against APT41 and TOUGHPROGRESS
The incident highlights the importance of staying vigilant against evolving threats like APT41 and TOUGHPROGRESS. Users should be cautious when using cloud services, ensuring they have adequate security measures in place to prevent malicious activity.