New AyySSHush Botnet Compromised Over 9,000 ASUS Routers, Adding Persistent SSH Backdoor
A recent discovery by GreyNoise, a threat intelligence firm, has revealed a sophisticated botnet compromising over 9,000 ASUS routers worldwide. The attackers have added a persistent SSH backdoor to these devices, allowing them to maintain control even after reboots or firmware updates.
The attack, which began on March 18, 2025, utilizes subtle tactics such as authentication bypasses and legitimate setting abuses to evade detection. This stealthy campaign has left security experts scrambling to understand the scope of the compromise and the motivations behind it.
"Using an AI-powered network traffic analysis tool we built called SIFT, GreyNoise has caught multiple anomalous network payloads with zero-effort that are attempting to disable TrendMicro security features in ASUS routers," states a GreyNoise spokesperson. "The attackers then exploit vulnerabilities and novel tradecraft in ASUS AiProtection features on those routers."
The threat intelligence firm uncovered evidence of an ongoing exploitation campaign, where attackers have gained unauthorized, persistent access to thousands of internet-exposed ASUS routers. This access survives both reboots and firmware updates, giving the attackers durable control over affected devices.
Attack Payloads and Exploited Vulnerabilities
The payloads observed by GreyNoise only target ASUS RT-AC3100 or RT-AC3200 with an out-of-box configuration. However, the experts also discovered a payload exploiting the authenticated command injection flaw CVE-2023-39780 in ASUS RT-AX55 v3.0.0.4.386.51598 to execute arbitrary system commands.
"This payload leverages built-in ASUS router features to enable SSH on both LAN and WAN, bind it to TCP/53282, and add an attacker-controlled public key," reads the full technical analysis published by GreyNoise. "Because this key is added using the official ASUS features, this config change is persisted across firmware upgrades. If you've been exploited previously, upgrading your firmware will NOT remove the SSH backdoor."
Scale of the Compromise and Implications
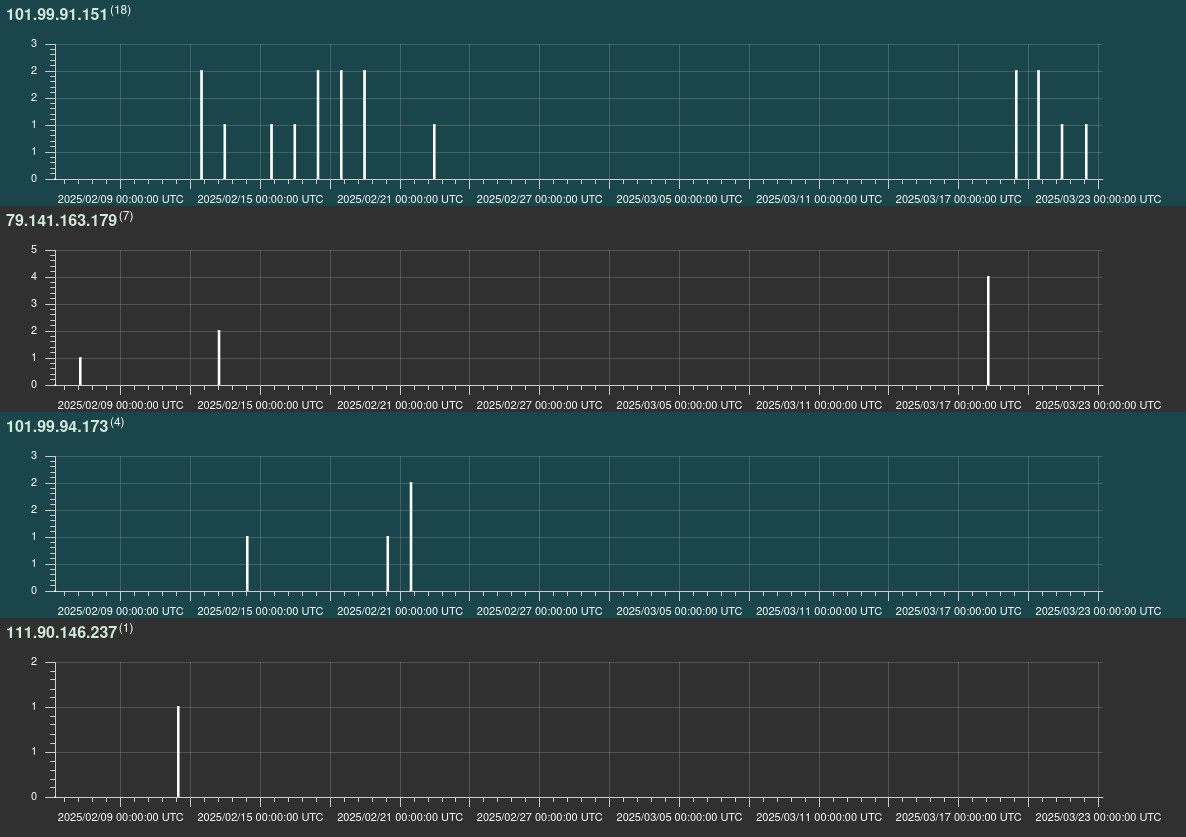
As of May 27, nearly 9,000 ASUS routers are confirmed compromised, based on Censys data. Despite the scale, only 30 related requests were observed over three months, highlighting how stealthy the campaign is.
The compromise has significant implications for individuals and organizations relying on these devices for internet connectivity. GreyNoise published a list of four IP addresses associated with the botnet's campaign as Indicators of Compromise (IOCs).
What to Do Next
If you own an ASUS router that may have been compromised, it is essential to take immediate action to secure your device and network. GreyNoise recommends checking the IOCs published by the firm and taking steps to patch any potential vulnerabilities.
Additionally, users should be cautious when updating their firmware, as the attackers' persistent backdoor will remain even after reboots or updates. Stay vigilant and monitor your network activity for any suspicious behavior.
Stay Informed
To stay informed about the latest security threats and vulnerabilities, follow GreyNoise on Twitter (@securityaffairs) and Facebook. You can also join their community on Mastodon to receive real-time updates and alerts.