What’s up with… Ciena, Salt Typhoon, remote surgery
In today's industry news roundup, we're looking at some of the latest developments in the world of telecommunications, cybersecurity, and medical technology.
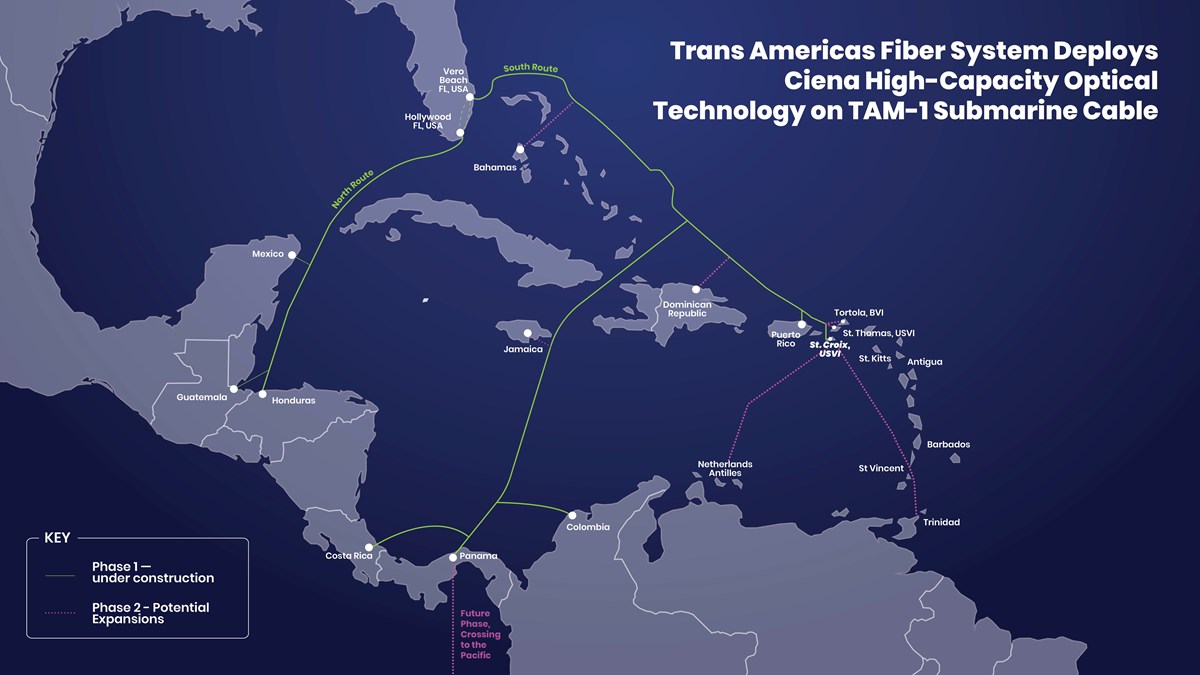
Ciena gear is set to be deployed in a new subsea network that will connect Central America and the Caribbean directly to the US. The TAM-1 system, developed by Trans Americas Fiber System (TAFS), features two diverse subsea routes and has been designed with a total system capacity of more than 650 Tbit/s across 24 fibre pairs southbound and 12 northbound.
The northern route of TAM-1 is expected to be ready for service before the end of 2025, followed by the southern route in the first quarter of 2026. Xtera is deploying the network for TAM-1, while AT&T will serve as the anchor tenant and landing station partner in all US jurisdictions.
Meanwhile, cybersecurity specialist Darktrace has warned that the Salt Typhoon hacking group has breached a European telco. The group, which is classed globally as an advanced persistent threat, has been active in North America and Europe, and has targeted telecom operators, government departments, and technology companies around the world.
Darktrace says that Salt Typhoon's attacks are carried out with levels of strategic rigour that point to Chinese state involvement, and that the group steals sensitive intelligence data more or less to the order of the politburo. The Chinese government denies any connections to the group, but it is clear that Salt Typhoon is a prime example of the creeping reach of nation-state-sponsored cyber-criminal groups.
Darktrace claims its technology can learn a company's "particular pattern of life" to identify and automatically neutralise novel and in-progress attacks with minimal disruption. The platform supports the entire security lifecycle, from proactively identifying weak points and preventing attacks to autonomously containing them and helping companies to recover from them.
On a more positive note, a team of scientists at the University of Glasgow's James Watt School of Engineering has used cheap, off-the-shelf hardware to build an Open RAN-based 4G network that connects a haptic controller to a robot arm. The system allows users to direct and manipulate movement of the arm in "near-real time" with extremely low latency, enabling a very high level of delicate control.
The team hopes that their work will eventually enable remote medical procedures and operations using affordable, open-source mobile networks. A paper detailing their efforts is published in the latest edition of the academic journal Communications Engineering.
Finally, a reminder from UK operator Virgin Media O2 that security threats are on the rise comes in the form of phishing attempts. The company notes that its security partner, Akamai, recorded 232,365 new phishing threat entries to its threat intelligence feeds during the April-to-June quarter this year, up a staggering 285% from the same period last year.