China-linked APT UNC5221 Exploits Ivanti EPMM Flaws Shortly After Disclosure
A China-linked Advanced Persistent Threat (APT) group, identified as UNC5221, has been exploiting two critical vulnerabilities in Ivanti Endpoint Manager Mobile (EPMM) to target organizations across Europe, North America, and the Asia-Pacific region. According to researchers from EclecticIQ, the group began chaining these vulnerabilities, CVE-2025-4427 and CVE-2025-4428, shortly after their disclosure by Ivanti on May 15, 2025.
The two vulnerabilities, reported by CERT-EU, are severe enough that they can be chained together to achieve remote code execution without authentication. Ivanti has since released updates for EPMM that address these vulnerabilities and provide a patch for users to update immediately. However, researchers have observed active exploitation of these flaws starting on the same day as their disclosure.
The attacks appear to be targeted at internet-exposed systems, with organizations in critical sectors such as healthcare, telecommunications, aviation, municipal government, finance, and defense across Europe, North America, and the Asia-Pacific region being affected. The attackers used Java Reflection to run remote commands, gained reverse shells, and formed a C2 channel using crafted HTTP GET requests.
Chinese cyber spies deployed the KrustyLoader malware on Ivanti EPMM systems, which allowed them to deploy malicious files from Amazon S3 buckets. The attackers relied on standard Linux tools like wget and curl to download an encrypted version of the Sliver backdoor, which was then decrypted using built-in AES keys.
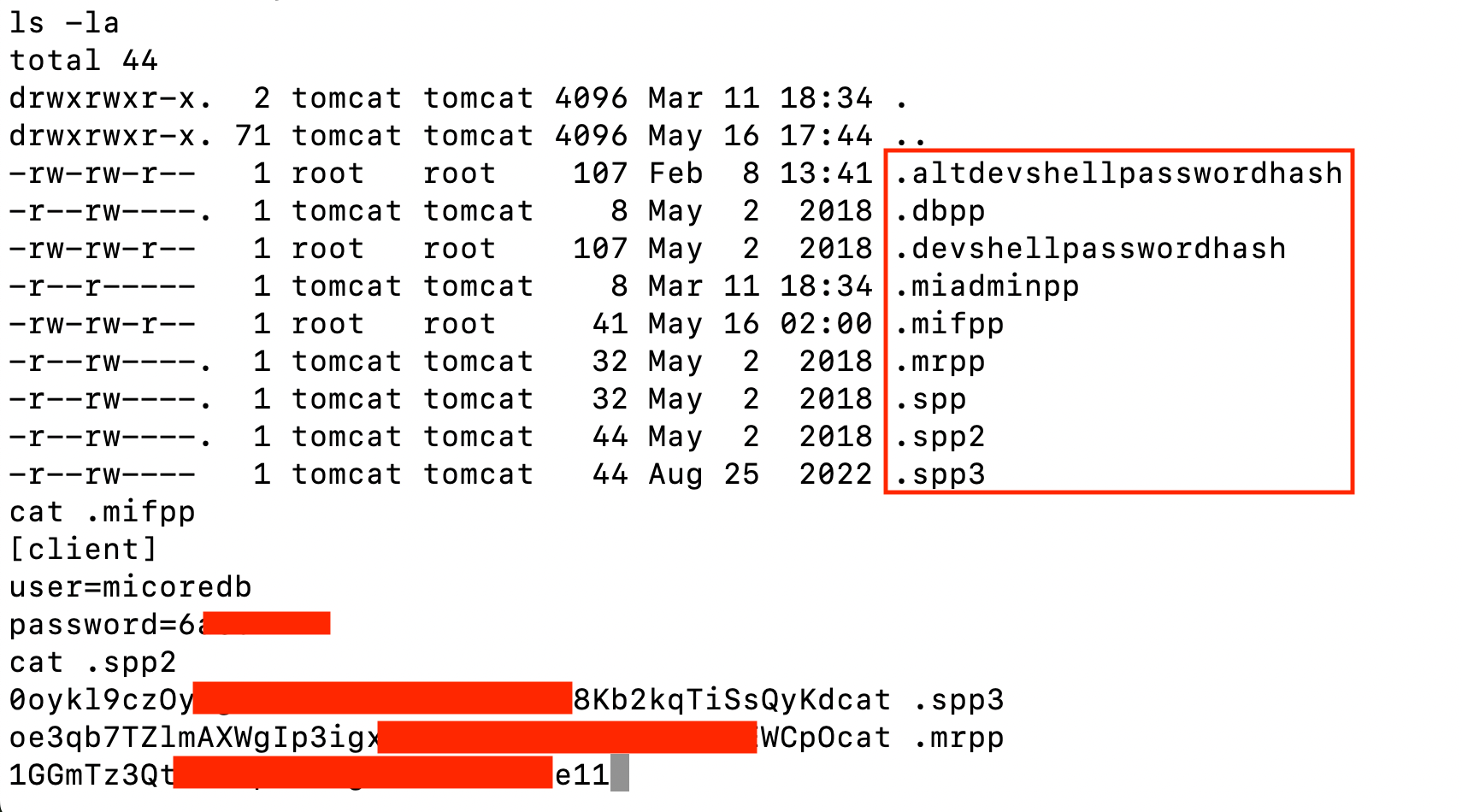
Researchers observed that the attackers targeted the mifs database in Ivanti EPMM systems as a key part of their espionage campaigns. They used hardcoded MySQL credentials, stored insecurely in system files, to access the database and extract sensitive information like mobile device data (IMEI, SIM, location), LDAP user details, and Office 365 tokens.
Using tools like mysqldump and Bash scripts downloaded from paste sites, the attackers extracted LDAP configs, Office 365 credentials, and metadata on managed devices. This information could allow unauthorized access to Microsoft cloud services like email and SharePoint. The attackers also dumped memory from Java processes to search for more credentials, saving the data in temporary directories for later exfiltration.
In short, the attackers abused built-in Ivanti tools and weak credential storage to steal vast amounts of sensitive data—likely for espionage targeting key public and private sector individuals. Chinese-linked hackers deployed FRP (Fast Reverse Proxy) on compromised Ivanti EPMM systems to maintain stealthy access.
Identifying the APT Group
EclecticIQ analysts assessed with high confidence that the observed Ivanti EPMM exploitation activity is very likely linked to UNC5221, a China-nexus cyber-espionage group. Infrastructure reuse and observed tradecraft closely align with previous campaigns attributed to this actor.
Recommendations for Users
Ivanti has released patches for the vulnerable EPMM software, and users are urged to update immediately to prevent exploitation by the UNC5221 APT group. Additionally, organizations should review their security controls and ensure that sensitive information is properly protected against unauthorized access.
Conclusion
The exploitation of Ivanti EPMM vulnerabilities by the UNC5221 APT group highlights the importance of timely patching and proper security measures to prevent cyber-attacks. As threat actors continue to evolve their tactics, it is essential for organizations to stay vigilant and adapt their security strategies accordingly.