Russia-linked APT28 Targets Western Logistics Entities and Technology Firms
A joint cybersecurity advisory issued by the US Cybersecurity and Infrastructure Security Agency (CISA) has warned of a Russian state-sponsored cyber campaign targeting Western logistics entities and technology companies. The group, known as APT28, also operates under other names such as Fancy Bear, Pawn Storm, Sofacy Group, Sednit, BlueDelta, and STRONTIUM, and has been active since at least 2007.
APT28 has targeted governments, militaries, and security organizations worldwide, including the 2016 Presidential election. The group is linked to Russia's Main Intelligence Directorate (GRU) 85th Main Special Service Center (GTsSS), military unit 26165, which is tracked by the cybersecurity community under several names.
A Threat to Supply Chains
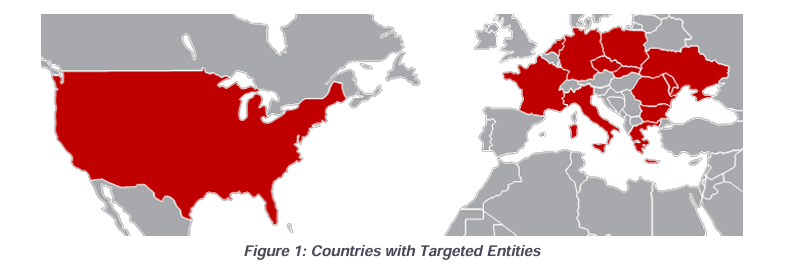
Since 2022, Western logistics entities and IT companies have faced an elevated risk of targeting by the Russian General Staff Main Intelligence Directorate (GRU) 85th Main Special Service Center (85th GTsSS), military unit 26165. This has resulted in a significant increase in cyber attacks on these organizations, which are involved in coordinating, transporting, and delivering foreign assistance to Ukraine.
These targeted entities span across NATO nations and Ukraine, including defense, maritime, air, and rail sectors. APT28 has exploited business ties to expand access to these targets, even probing Industrial Control System (ICS) makers for railway systems.
Methods Used by APT28
APT28 uses a mix of previously disclosed tactics, techniques, and procedures (TTPs) in its cyber espionage-oriented campaign. The group has employed various methods for initial access, including brute-force attacks, spear-phishing, exploiting known vulnerabilities in Outlook, Roundcube, WinRAR, VPNs, and SOHO devices.
The attackers also used compromised nearby devices to proxy attacks and evade detection. They sent emails mimicking government/cloud providers, often in the target language, and used lures like legit documents. Some campaigns bypassed Multi-Factor Authentication (MFA) and used IP checks, redirectors, and delivered malware.
Exploiting Vulnerabilities
GRU Unit 26165 exploited CVE-2023-23397 in Outlook to steal NTLM hashes via fake calendar invites. They also leveraged a WinRAR flaw (CVE-2023-38831) to execute code via malicious archives sent through emails or embedded links.
Lateral Movement and Data Exfiltration
After initial access, APT28 conducted reconnaissance on key personnel, cybersecurity teams, and partners. The experts observed the group using tools like Impacket, PsExec, RDP, and Certipy for lateral movement and Active Directory data exfiltration.
The actors harvested credentials, manipulated mailbox permissions, and accessed sensitive shipment data. Threat actors also used voice phishing to target privileged accounts. APT28 deployed custom malware like HEADLACE and MASEPIE, using DLL hijacking, scheduled tasks, run keys, and malicious shortcuts to maintain access.
Other Malware Used
Experts warned that attackers can use other malware like OCEANMAP and STEELHOOK in cyber operations against logistics and IT sectors. The threat actors exfiltrated data using PowerShell, APIs (EWS/IMAP), and periodic queries, leveraging local infrastructure to evade detection.
Targeting IP Cameras
The attackers also targeted IP cameras near Ukrainian borders and military sites via RTSP, using default/brute-forced credentials to access live feeds. This campaign helped monitor aid and material movement into Ukraine.
Security Mitigations
The joint alert includes general and detailed security mitigations to help prevent these types of attacks. It is essential for organizations to stay vigilant and take proactive measures to protect their networks and systems from APT28's tactics, techniques, and procedures.