New botnet HTTPBot targets gaming and tech industries with surgical attacks
A new botnet known as HTTPBot has emerged, targeting China's gaming, tech, and education sectors with highly sophisticated and targeted attacks. NSFOCUS cybersecurity researchers have discovered this Go-based botnet, which was first detected in August 2024 but saw a significant surge in activity by April 2025.
HTTPBot employs a periodic, multi-stage strategy to launch continuous assaults on specific victims, using an "attack ID" for precise control. The botnet utilizes advanced DDoS tactics like HTTP Floods and obfuscation to bypass traditional detection methods. This approach marks a significant shift in DDoS attacks, moving from indiscriminate traffic suppression to high-precision business strangulation.
"HTTPBot has taken a different approach by developing a range of HTTP-based attack methods to conduct transactional (business) DDoS attacks," reads the report published by NSFOCUS. "Attackers can use these methods to precisely target high-value business interfaces and launch targeted saturation attacks on critical interfaces, such as game login and payment systems."
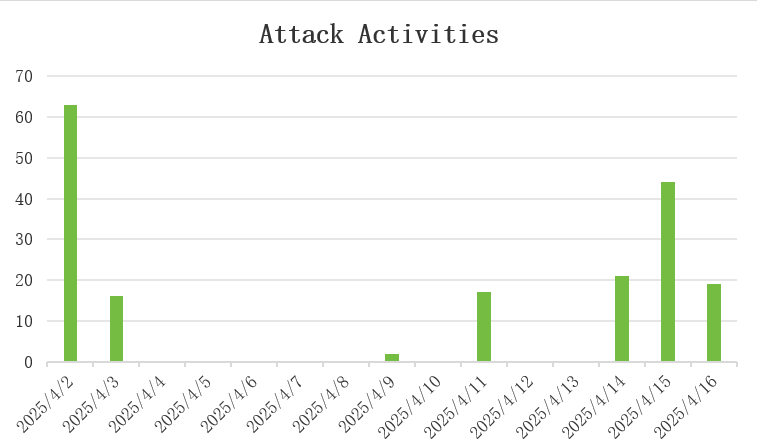
"This attack with 'scalpel-like' precision poses a systemic threat to industries that rely on real-time interaction," warns the report. Since early April 2025, the botnet has issued over 200 attack commands, with activity spread across all hours of the day.
The researchers pointed out that the botnet supports 7 built-in DDoS attack methods, all of which are HTTP types. The most commonly used attacks include http_fp, http_auto, and HTTP. "The above attacks covered more than 80 independent targets, mainly in the domestic gaming industry, but also technology companies, educational institutions, and tourist attractions," continues the report.
"Attackers usually launch multiple rounds of attacks on the same target in different time periods, with clear targets," the researchers observed. The malware hides its GUI to evade detection and ensures persistence by adding itself to the Windows startup registry.
The bot communicates with its server via a streamlined process using an "attack ID" for precise control. It supports 7 HTTP-based DDoS methods, configurable with parameters like target, duration, and method. Some attacks require Windows version greater than 8, showcasing advanced evasion and control techniques.
"DDoS Botnet families tend to congregate on Linux and IoT platforms," concludes the report. "However, the HTTPBot Botnet family has specifically targeted the Windows platform. In just a few months, it has emerged as a significant threat that cannot be ignored on the Windows platform."
Follow me on Twitter: @securityaffairs and Facebook and Mastodon for more updates on this developing story.