Inside Starlink's User Terminal
The name Starlink conjures up images of satellites orbiting the Earth, carrying data to and from ground stations in a celestial dance. But what about the user terminal itself? A crucial component of the system, often overlooked in favor of its space-bound brethren. Luckily, thanks to DarkNavy, we can now take a closer look at this fascinating piece of hardware.
The Terminal: A Modular Marvel
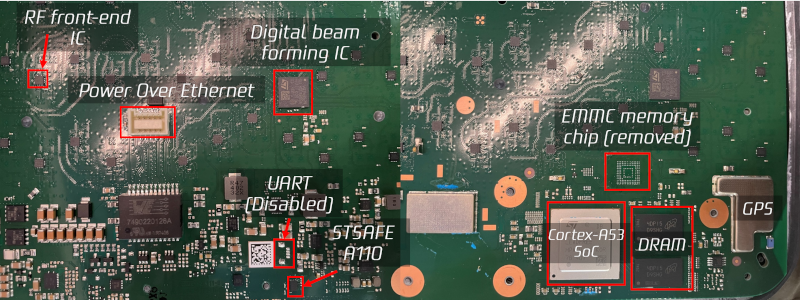
The user terminal consists of two main parts: the router and the antenna. Or, to be more precise, it's the RF transceiver and antenna combined into one unit. This modular design allows for easy maintenance and upgrades, but also raises interesting questions about security.
The Anatomy of the Antenna
So, what makes up this antenna? In a nutshell, it's 100% full of printed circuit board (PCB) goodness, with many RF chips at its core. But that's not all - a custom ST Microelectronics Cortex A-53 quad-core CPU also calls the shot. It may look like just another ordinary CPU, but trust us, it's got some tricks up its sleeve.
The Hack That Exposed the Terminal
A brave hacker, known only by their handle DarkNavy, managed to gain root shell access on one of these terminals. This led to a firmware update that disabled the UART (Universal Asynchronous Receiver-Transmitter), essentially cutting off the terminal's ability to communicate with the outside world.
However, this didn't deter DarkNavy from continuing their investigation. They wanted to take a closer look at the code and see if they could find any hidden vulnerabilities or backdoors. But as it often does, security proved to be the ultimate puzzle-solver.
Decoding the Code
DarkNavy's next move was to try and dump the flash memory from the device. They decided to take a more hands-on approach by desoldering the eMMC chip (a crucial storage component) and reading its contents. The result? A treasure trove of code snippets, waiting to be deciphered.
The Next Step: Creating a Virtual Environment
With the code in hand, DarkNavy turned their attention to creating a virtual environment where they could run the software under Qemu (a popular emulator). This allowed them to test and analyze the terminal's behavior in greater detail.
Security Questions Linger
As with any security investigation, questions arose about the terminal's setup. One notable red flag was the presence of 41 trusted SSH keys stored in the device's authorized_keys file. While not necessarily a smoking gun, it did raise some eyebrows among security experts.
The ongoing cat-and-mouse game between Starlink and hackers has been an intriguing spectacle to watch. With this latest investigation, we're reminded that even seemingly secure devices can hold secrets waiting to be uncovered.