Threat Actors Use Fake AI Tools to Deliver Information Stealer Noodlophile
Researchers at Morphisec have warned that threat actors are using fake AI tools to trick users into installing the information stealer Noodlophile. This malicious software has been spotted spreading through viral posts and Facebook groups, luring unsuspecting victims into downloading it as part of a supposed free AI video tool.
According to Morphisec, attackers are exploiting the hype surrounding artificial intelligence (AI) to spread malware via fake AI tools promoted on social media platforms. Users who click on these posts or join related Facebook groups may unknowingly download Noodlophile Stealer, a new and previously undocumented malware that can steal browser credentials, crypto wallet data, and potentially install remote access trojans like XWorm.
The experts pointed out that Noodlophile Stealer is being sold on cybercrime forums as part of malware-as-a-service schemes, often bundled with tools for credential theft. The developer, likely Vietnamese, has been seen actively engaging in related Facebook posts and has been promoting the malware to potential buyers.
How Fake AI Tools Work
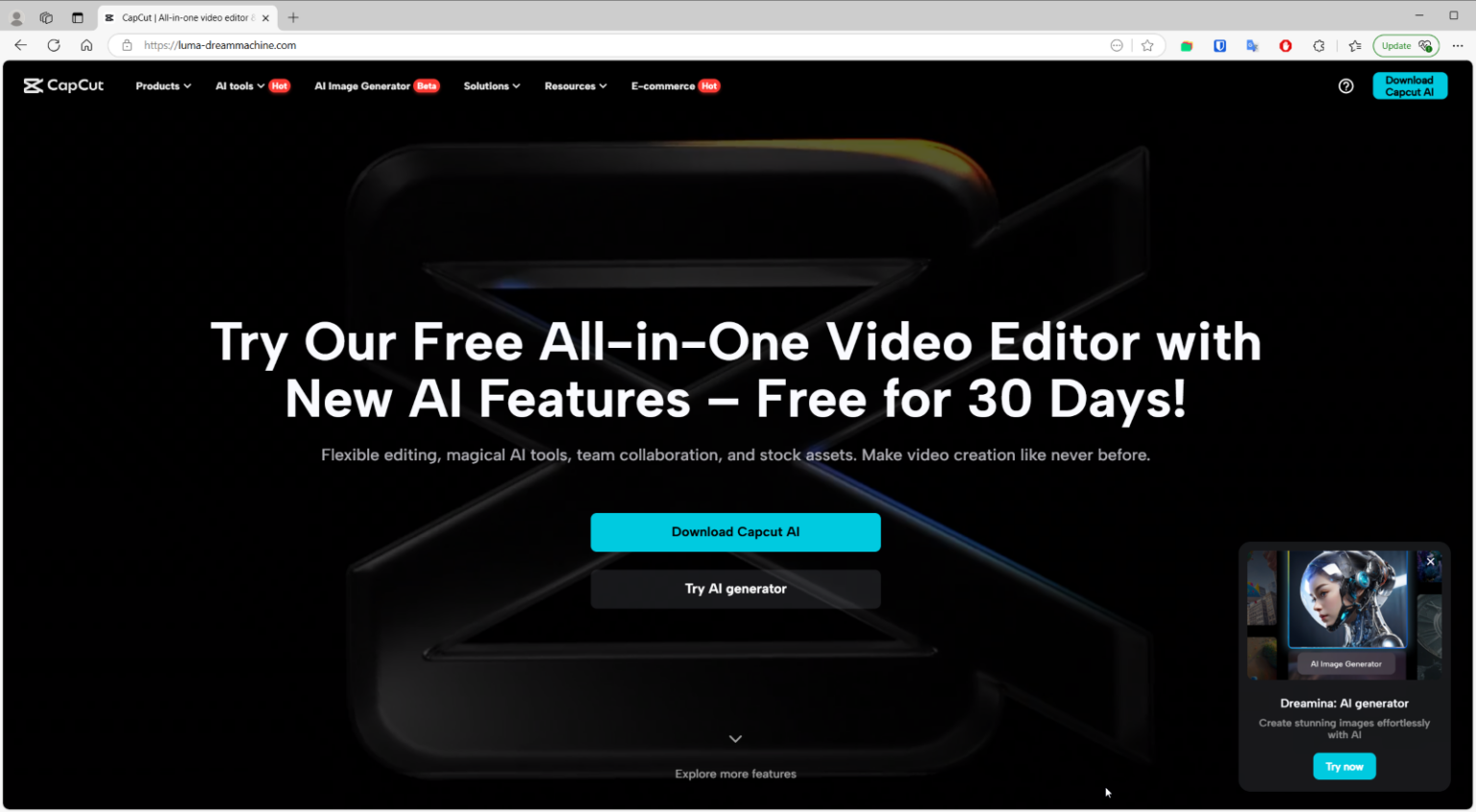
Fake AI tools are being used to spread malware via social media and scam websites like "Dream Machine" or "CapCut". These platforms lure users into uploading media, which then delivers a malicious ZIP file disguised as an AI-generated content. The victims are tricked into downloading malware such as Noodlophile or XWorm, which steals credentials, crypto wallets, and can grant attackers remote access to infected systems.
The fake AI tool posts have garnered over 62,000 views per post, making them highly effective at deceiving users seeking free video/image editors. However, instead of providing the promised software, these posts deliver malware disguised as AI-generated content.
The Anatomy of the Malware
The malware spreads through a fake video file called "Video Dream MachineAI.mp4.exe" which launches a legitimate CapCut binary. The deceptive naming and certificate used in this binary help it evade user suspicion and some security solutions.
"The main objective of this binary is to locate and execute a secondary file, CapCut.exe, from a folder within its current directory," reads the report published by the researchers. "This triggers a .NET loader (“CapCutLoader”) which fetches and runs a Python-based malware (“srchost.exe”). The Python binary deploys Noodlophile Stealer, which extracts browser credentials, crypto wallet data, and sometimes includes XWorm for remote system access."
The report also includes Indicators of Compromise (IOCs) for this campaign, allowing security researchers to identify and track the malware.
Conclusion
Threat actors are becoming increasingly sophisticated in their use of fake AI tools to spread malware. It is essential for users to be aware of these tactics and take precautions to protect themselves from falling victim to such attacks. By staying informed and vigilant, we can all play a crucial role in preventing the spread of this malicious software.