Operation Moonlander Dismantles 20-Year Botnet Behind Anyproxy and 5socks Cybercriminal Services
In a significant crackdown, law enforcement agencies have dismantled a vast botnet behind the notorious cybercriminal services of Anyproxy and 5socks. The operation, codenamed "Operation Moonlander," has resulted in the arrest of four suspects, including three Russians, who will face charges for their role in maintaining and operating the illegal proxy networks.
The botnet, which has been active for over 20 years, was created by infecting older-model wireless internet routers worldwide using malware without the owners' knowledge. The installed malware allowed the routers to be reconfigured, granting unauthorized access to third parties and making them available for sale as proxy servers on the Anyproxy.net and 5socks.net websites.
The Scope of the Botnet
According to court documents, 5socks.net sold over 7,000 proxies globally, charging users $9.95–$110/month, and earning a staggering $46 million by exploiting infected routers via the Anyproxy botnet. The site falsely claimed identities to register domains, further adding to its nefarious activities.
Malware and Its Tactics
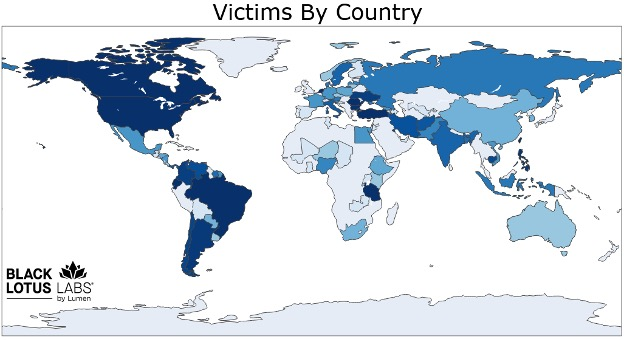
FBI agents in Oklahoma found malware on residential and business routers without users' knowledge. Black Lotus Labs Lumen researchers discovered an average of 1,000 unique bots weekly contacting C2 servers in Turkey, with most victims in the U.S., followed by Canada and Ecuador.
The botnet operators allowed cryptocurrency payments, targeting IoT and SOHO devices, and designed to help conceal a range of illicit pursuits including ad fraud, DDoS attacks, brute forcing, or exploiting victim's data. Proxies like this are "designed to help conceal a range of illicit pursuits," according to the report published by Black Lotus Labs.
The Rent-a-Proxy Service
The botnet offers a "Rent-a-Proxy" service, where users can buy access to IP:port combos for 24 hours with no authentication required. The system checks deny-lists to avoid detection but allows customers to carry out a broad range of malicious activities like ad fraud, DDoS, brute force attacks, and data exploitation.
The Threat to Internet Security
"Proxy services have and will continue to present a direct threat to internet security as they allow malicious actors to hide behind unsuspecting residential IPs, complicating detection by network monitoring tools," concludes the report. "As a vast number of end-of-life devices remain in circulation, and the world continues to adopt devices in the 'Internet of Things,' there will continue to be a massive pool of targets for malicious actors."
A Warning from the FBI
The FBI released a FLASH alert warning about 5Socks and Anyproxy malicious services targeting end-of-life (EOL) routers. Attackers target EoL devices to deploy malware by exploiting vulnerabilities and create botnets for attacks or proxy services.
Infected routers form botnets used in coordinated attacks or sold as proxies on 5Socks and Anyproxy. Once installed, the malware allows threat actors to achieve persistent access, allowing regular communication with the device every 60 seconds to five minutes to maintain control and availability for customers.
Malware spreads through internet-connected devices with remote access enabled, and attackers can gain shell access even with password protection.
The dismantling of this botnet marks a significant blow to cybercriminals and highlights the need for continued vigilance in protecting against such threats. As technology continues to evolve, it's essential that we stay informed about emerging risks like these and take proactive steps to protect ourselves and our digital assets.