**Broadside Botnet Hits TBK DVRs, Raising Alarms for Maritime Logistics**
A new variant of the Mirai botnet, dubbed Broadside, has been identified targeting vulnerable TBK Vision Digital Video Recorders (DVRs) used in the maritime logistics sector. The campaign, uncovered by Cydome's cybersecurity researchers, poses a significant threat to shipping companies and raises concerns about the potential for compromised devices to disrupt operations and compromise sensitive information.
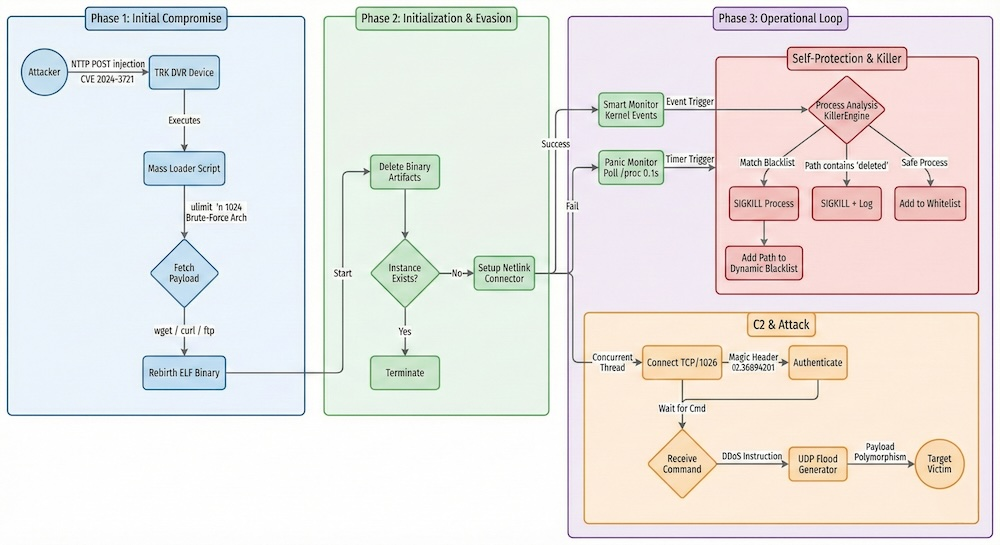
The Mirai botnet's source code was made public nearly a decade ago, but its variants continue to evolve and cause widespread damage. The Broadside variant exploits the command injection vulnerability CVE-2024-3721 in TBK DVR devices, which was disclosed in April 2024 with proof-of-concept (PoC) code available. However, it has been widely exploited by multiple DDoS botnets by mid-2025.
Cydome's researchers observed that the campaign's infrastructure has been active for months, showing fluctuating activity and indicating a sustained effort to target vulnerable devices. The Broadside botnet differs from typical Mirai variants through its custom C2 protocol over TCP/1026 (with fallback communications on TCP/6969), unique Magic Header, and "Judge, Jury, and Executioner" exclusivity module.
The botnet uses Netlink kernel sockets for stealthy monitoring and payload polymorphism to evade detection. It also employs a mass loader that executes multi-architecture payloads in memory and wipes traces, making it difficult to track the compromised devices. Furthermore, Broadside supports UDP-based DDoS attacks and steals system files (/etc/passwd and /etc/shadow) to enable privilege escalation and lateral movement.
The researchers warn that TBK DVR flaw also impacts rebranded models sold as CeNova, Night Owl, QSee, and others. The campaign poses serious risks to shipping firms, as the targeted DVRs are often installed on vessels. Compromised devices could enable access to CCTV feeds of the bridge, cargo areas, or engine room, disrupt satellite communications through flooding, or provide a foothold for lateral movement toward critical OT systems on the ship.
"Crucially, the threat extends beyond denial-of-service attacks; analysis confirms that Broadside actively attempts to harvest system credential files (/etc/passwd and /etc/shadow). This indicates a secondary objective of privilege escalation and lateral movement, transforming the compromised device from a simple bot into a strategic foothold," concludes the report.
**Similar Threats and Implications**
In June, researchers from Kaspersky discovered another variant of the Mirai botnet that exploits the same vulnerability in TBK DVR-4104 and DVR-4216 digital video recording devices. This variant uses a simple RC4 algorithm to decrypt strings and XOR to obfuscate the key. Once decrypted, strings are stored in a global list for use during execution.
The malware also includes anti-VM and anti-emulation checks by scanning running processes for signs of VMware or QEMU. The malware verifies its execution path against a list of allowed directories to avoid detection. If all checks pass, it proceeds to prepare the infected device to receive commands.
**Regional Breakdown**
Most infections are reported in China, India, Egypt, Ukraine, Russia, Turkey, and Brazil. While the exact number of infected devices is unclear, Kaspersky found over 50,000 exposed DVRs, which are potential targets for exploitation.
The discovery of the Broadside botnet highlights the ongoing threat posed by Mirai variants and the importance of addressing vulnerabilities in IoT devices. Shipping companies and maritime logistics operators must take immediate action to secure their TBK DVRs and prevent potential disruptions and data breaches.