New 'Bring Your Own Installer (BYOI)' Technique Allows to Bypass EDR
A new "Bring Your Own Installer" (BYOI) technique has been discovered that allows attackers to bypass SentinelOne Endpoint Detection and Response (EDR), disable protection, and deploy Babuk ransomware by exploiting the agent upgrade process.
The Discovery
Aon's Stroz Friedberg recently uncovered this vulnerability while investigating an incident where a threat actor gained local administrative access and bypassed SentinelOne's anti-tamper protections without using malicious driver files. The researchers discovered that the attack was possible due to disabled local upgrade/downgrade authorization.
The Attack Vector
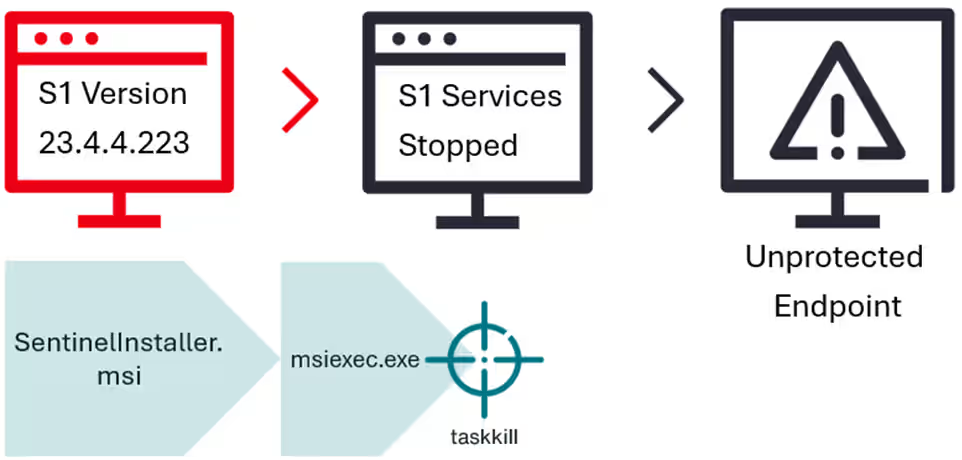
The attack vector involves exploiting a flaw in SentinelOne's upgrade process, specifically the lack of online authorization for local upgrades and downgrades. This allows attackers to interrupt the upgrade process at the right moment, leaving the system vulnerable and completely unprotected.
The Stroz Friedberg researchers tested this technique on a Windows Server 2022 machine with SentinelOne version 23.4.6.223 installed. They confirmed that the agent was running properly and showing as online in the management dashboard. To exploit the vulnerability, they launched an installer (MSI file) for a different version of SentinelOne, which triggered the Windows built-in msiexec.exe process to shut down the currently running SentinelOne processes.
The Consequences
Once the upgrade process was interrupted, the system became vulnerable to attacks. The researchers observed rapid version changes, installer file use, and event log entries tied to EDR tampering. In this case, the attackers deployed Babuk ransomware.
Mitigation and Prevention
SentinelOne has since issued guidance on mitigating this issue to their customers. The solution involves enabling the "Online authorization" feature in the Sentinels Policy menu in the management console. This removes the ability to perform local upgrades and downgrades, preventing attackers from exploiting this vulnerability.
Conclusion
The discovery of this BYOI technique highlights the importance of keeping endpoint security software up-to-date and ensuring that online authorization is enabled for local upgrades and downgrades. Attackers are becoming increasingly sophisticated in their tactics, and it's essential for organizations to stay vigilant and adapt to new threats.