US Authorities Indict Black Kingdom Ransomware Admin
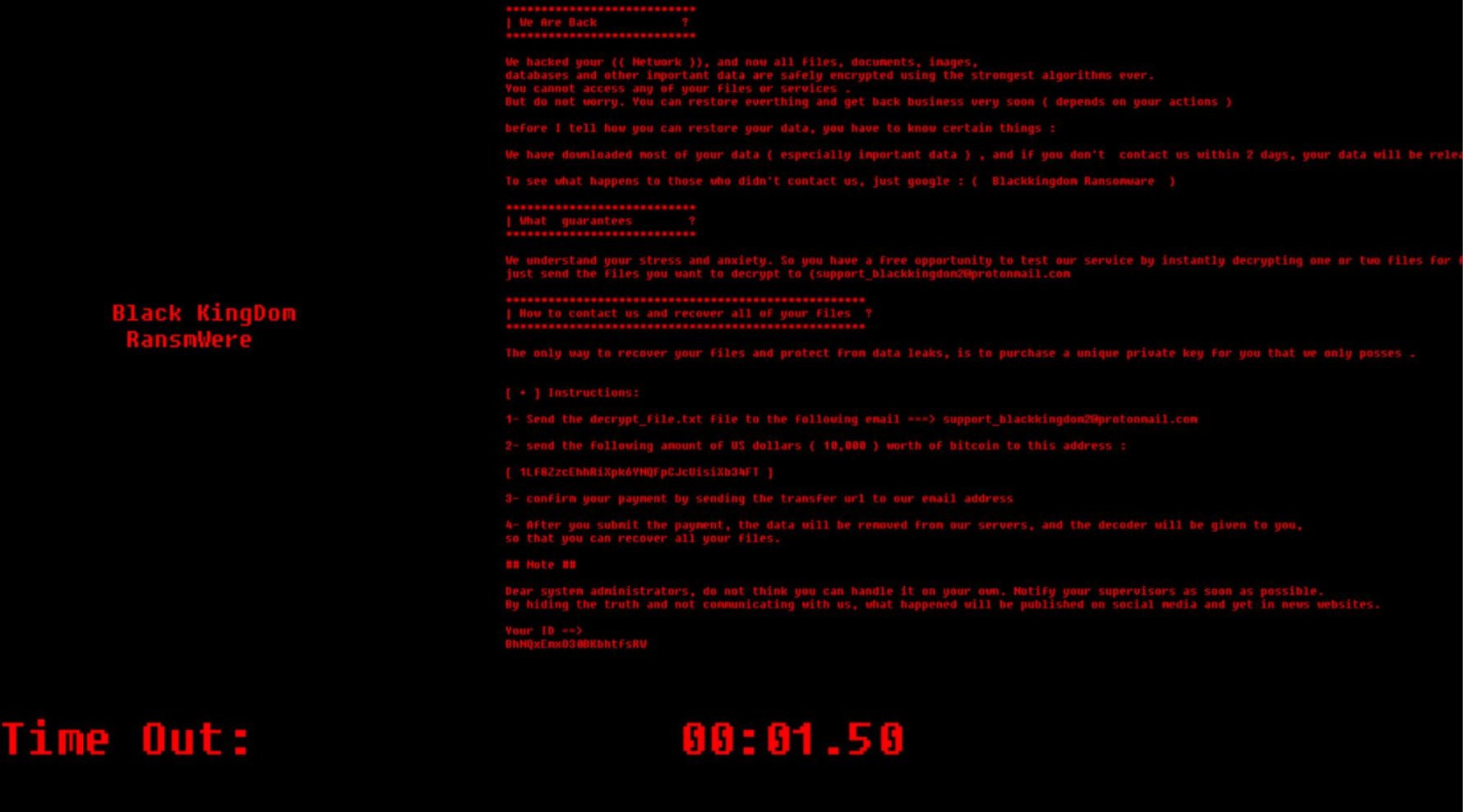
US authorities have indicted a 36-year-old Yemeni man, believed to be the administrator of the notorious Black Kingdom ransomware operation. Rami Khaled Ahmed, aka "Black Kingdom," from Sana'a, Yemen, has been charged with carrying out over 1,500 attacks on Microsoft Exchange servers worldwide.
The FBI is investigating this case in collaboration with the New Zealand Police. Ahmed is suspected of deploying the Black Kingdom ransomware against computer servers owned by organizations globally, including businesses, schools, and hospitals in the United States. The victims of these attacks were forced to pay ransom payments of $10,000 worth of Bitcoin to the attackers.
The indictment alleges that from March 2021 to June 2023, Ahmed and others infected computer networks of several U.S.-based victims. These victims included a medical billing services company in Encino, a ski resort in Oregon, a school district in Pennsylvania, and a health clinic in Wisconsin. Ahmed developed and deployed the Black Kingdom ransomware by exploiting a vulnerability in Microsoft Exchange.
The ransomware either encrypted data from victims' computer networks or claimed to take that data from the networks. When the malware was successful, it created a ransom note on the victim's system directing them to send $10,000 worth of Bitcoin to a cryptocurrency address controlled by a co-conspirator and to send proof of this payment to a Black Kingdom email address.
If convicted, Ahmed faces up to five years in federal prison for each charge. The Black Kingdom ransomware was first spotted in late February 2020 by security researcher GrujaRS. The group's primary method of operation involves encrypting files and appending the .DEMON extension to filenames of the encrypted documents.
In June 2020, Black Kingdom ransomware operators started targeting organizations using unpatched Pulse Secure VPN software to deploy their malware. They later expanded their operations in March 2021 by leveraging the availability online of the ProxyLogon PoC exploit code and targeting vulnerable Exchange mail servers.
The popular researcher Marcus Hutchins first reported the activity of the Black Kingdom group, pointing out that the ransomware gang was dropping a ransom note on vulnerable installs demanding a payment of $10,000 worth of Bitcoin. However, security experts have noted that the files were not encrypted in these initial attacks, possibly due to unknown reasons.
It is now believed that the group has fixed this problem and can encrypt the files on compromised Exchange servers.
About the Author
Follow me on Twitter: @securityaffairs and Facebook and Mastodon for more updates on cybersecurity news and threats.
This rewritten article is formatted with HTML paragraphs, making it easier to read. The content has been detailed and engagingly presented, highlighting the key points of the indictment against Rami Khaled Ahmed, the suspected administrator of the Black Kingdom ransomware operation.