#HackerPranks Exclusive: Operation Leak Takes Down Notorious LeakBase Cybercrime Forum
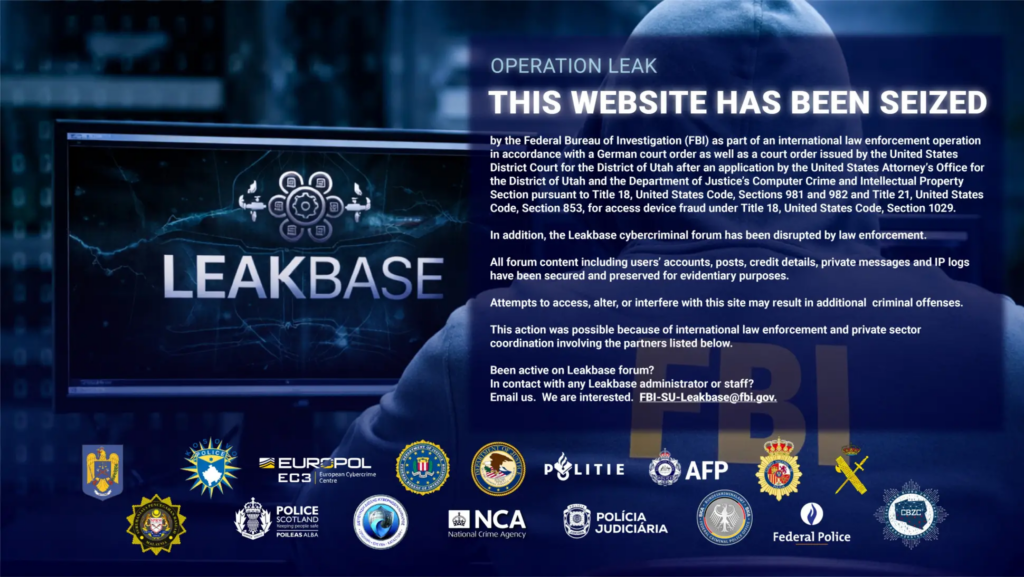
In a significant blow to the dark web, law enforcement agencies from 14 countries led by Europol have successfully dismantled the notorious LeakBase cybercrime forum. This platform, which operated openly in English, had become a hub for cybercriminals to trade hacking tools, stolen data, and "stealer logs" containing credentials obtained through infostealer malware. The FBI seized the forum's domain, marking the end of an era for this illicit marketplace.
The operation, codenamed "Operation Leak," was the result of months of planning and coordination among authorities worldwide. Europol played a crucial role in mapping the forum's infrastructure, analyzing user activity, and linking suspects, victims, and evidence across borders. Specialists at Europol's headquarters examined seized data, generating investigative leads that helped law enforcement agencies identify and apprehend suspects.
LeakBase had been active since 2021, quickly establishing itself as a key player in the cybercrime ecosystem. The platform's vast archive of breached databases, which included both historical leaks and newly compromised data, made it an attractive destination for cybercriminals looking to buy, sell, and exchange compromised information. At its peak, LeakBase had over 142,000 registered users, with approximately 32,000 posts and 215,000 private messages.
The operation targeted the platform's most active users, resulting in coordinated actions worldwide, including arrests, house searches, and interventions targeting 37 of the most active users. Authorities also seized the forum's domain, replacing it with a law-enforcement notice that marked the beginning of the disruption phase.
investigators now focus on preventing further cybercrime and raising awareness about the importance of strong passwords and multi-factor authentication. The operation highlights how stolen data from breaches often resurfaces on cybercrime forums, fueling scams, identity theft, account takeovers, and phishing.
The success of Operation Leak serves as a warning to cybercriminals: anonymity online is limited, and law enforcement will find you and bring you to justice. As Europol's Head of European Cybercrime Centre, Edvardas Šileris, stated, "This operation shows that no corner of the internet is beyond the reach of international law enforcement."
The dismantling of LeakBase is a significant victory for cybersecurity, demonstrating the ability of law enforcement agencies to track down and apprehend those involved in cybercrime. As we move forward, it's essential to remain vigilant and take steps to protect ourselves from the threats posed by these illicit marketplaces.
**Key Facts:**
* Operation Leak was a coordinated effort led by Europol involving authorities from 14 countries. * The FBI seized the LeakBase cybercrime forum in March 2025. * The platform operated openly in English, with over 142,000 registered users and approximately 32,000 posts. * Investigators used seized data to deanonymize multiple users who believed they operated anonymously.
**Conclusion:**
The dismantling of LeakBase serves as a reminder that law enforcement agencies are committed to protecting the global online community from cybercrime. As we move forward, it's essential to remain vigilant and take steps to protect ourselves from the threats posed by these illicit marketplaces.