Silver Dragon's Sophisticated APT41 Playbook: From Phishing to Google Drive C2
The world of advanced persistent threats (APTs) has taken a significant leap with the emergence of Silver Dragon, an APT group linked to the infamous China-based threat actor APT41. Since mid-2024, this group has been targeting government entities in Europe and Southeast Asia, leveraging a sophisticated playbook that includes server exploits, phishing, Cobalt Strike, and Google Drive-based command-and-control (C2) channels.
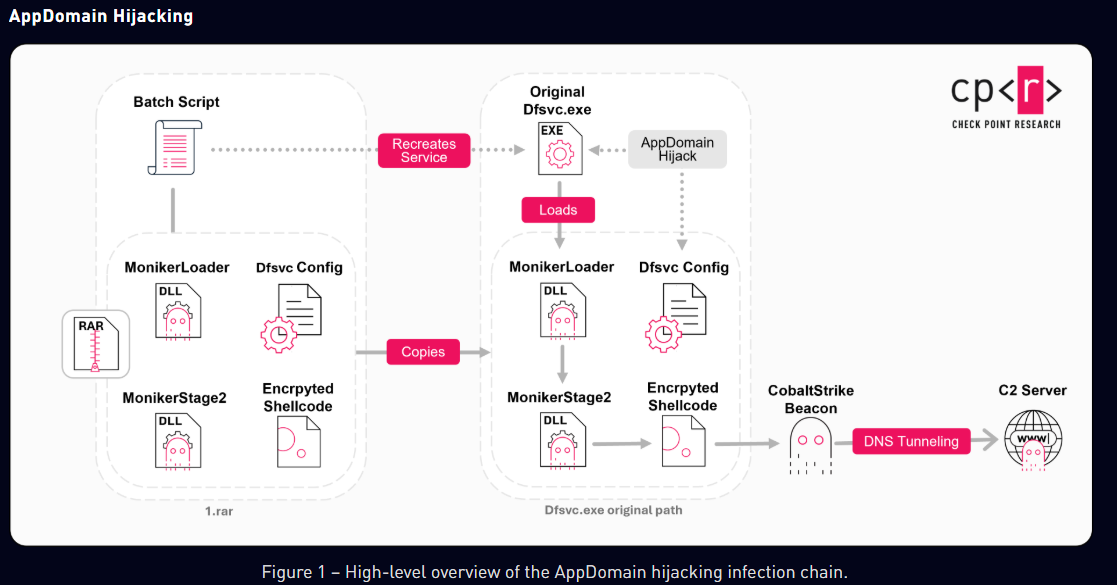
Silver Dragon's attack chain relies heavily on exploiting public-facing servers to gain initial access, followed by sending phishing emails with malicious attachments. To maintain persistence, the group hijacks legitimate Windows services and utilizes tools like Cobalt Strike and Google Drive-based C2 channels to evade detection. The attack vector involves AppDomain hijacking, malicious service DLL deployment, and weaponized LNK attachments, all of which are facilitated by heavily obfuscated loaders such as MonikerLoader and BamboLoader.
These loaders play a crucial role in decrypting and injecting payloads in memory, hijacking legitimate Windows services for persistence, and evading detection. Furthermore, evidence suggests the use of an automated framework to generate tailored attack packages, with all files contained within the initial archive sharing identical creation timestamps. This strongly suggests the involvement of an automated payload generation framework.
The group's reliance on Cobalt Strike beacons as the final payload is noteworthy, using cracked versions configured for DNS tunneling, HTTP via Cloudflare, or even SMB communication within compromised networks. Beyond Cobalt Strike, Silver Dragon also relies on custom post-exploitation tools, such as SilverScreen for covertly capturing screenshots and SSHcmd for remote command execution and file transfer over SSH.
One of the most interesting aspects of Silver Dragon's playbook is its use of Google Drive as a C2 channel. The group uses GearDoor, a .NET backdoor, to manage tasks through specially crafted file extensions, encrypting communications and providing persistence in compromised networks. This combination of tools highlights an advanced and modular intrusion framework that provides persistence, stealthy data exfiltration, lateral movement, plugin execution, and even self-updating capabilities.
Silver Dragon's primary target is high-profile government organizations, with a focus on Southeast Asia and additional activity observed in parts of Europe. The group's ability to continuously evolve its tooling and techniques, actively testing and deploying new capabilities across different campaigns, underscores the complexity and adaptability of this threat actor.
In conclusion, Silver Dragon's APT41 playbook represents a significant escalation in the sophistication and diversity of threats targeting government entities worldwide. Its use of automated payload generation frameworks, heavily obfuscated loaders, and custom post-exploitation tools highlights an advanced and modular intrusion framework that is likely to continue evolving in response to changing threat landscapes.
Key Takeaways:
* Silver Dragon is an APT group linked to APT41, targeting governments via server exploits and phishing. * The group uses a sophisticated playbook that includes Cobalt Strike, Google Drive-based C2 channels, and custom post-exploitation tools. * Automated payload generation frameworks are used to generate tailored attack packages. * Heavily obfuscated loaders such as MonikerLoader and BamboLoader play a crucial role in decrypting and injecting payloads in memory.
Recommendations:
* Government entities should prioritize monitoring their networks for suspicious activity, particularly focusing on server exploits and phishing attempts. * Organizations should ensure that all software is up-to-date and patched, with a particular focus on Windows services and vulnerabilities. * Implementing robust security measures, such as intrusion detection systems (IDS) and threat intelligence feeds, can help identify and mitigate the use of custom post-exploitation tools like GearDoor.
By understanding the tactics, techniques, and procedures (TTPs) employed by Silver Dragon and its APT41 counterparts, organizations can better prepare themselves to defend against these sophisticated threats.